A tour through Defender for Cloud Apps
Microsoft Defender for Cloud Apps (CAS). A cloud broker - probably one of the most powerful tools regarding security and compliance in the cloud cosmos. If you are completely new to all these topics, I would suggest to read about the M365 security concepts before. Here is an official Microsoft sheet on CAS.
Solution review
Todays applications are found in the web = SaaS - Software as a Service. Some use case, that a business wants, hosted from the Internet, that you draw a benefit. The challenge is that there is no way to centrally manage these interactions from your users. The legacy approach was maybe to set firewall policies, but that is laborious. Defender for Cloud Apps stands between these connections, gives major insights and leverages controls.
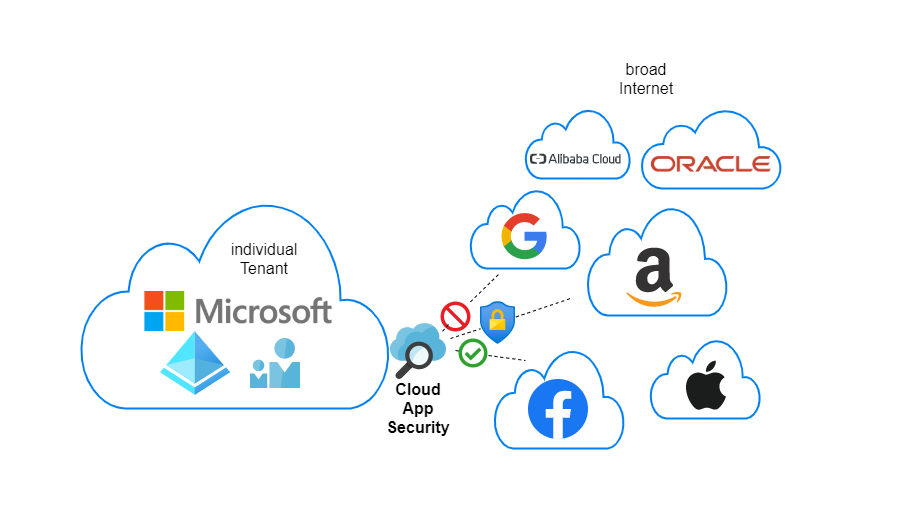
Shadow IT
Shadow IT describes the concept of decentralized IT actions, that are (most of the time) not allowed. Here is an example: a user of your organization enables collaboration to a cloud app. The IT department has no information or governance on this. This is where CAS enters the game to benefit you.
License requirements
Official pricing sheet
When talking about pricing, Defender for Cloud Apps has some included features in Azure AD Premium P1, that is part of Enterprise Mobility + Security E3. The full capabilities get available with the Microsoft 365 E5 Security or the standalone CAS license, which only costs 3.5$/user/month. See all license functionalities.
Setup
Let's start with the configuration of the service. Enter the portal portal.cloudappsecurity.com/.
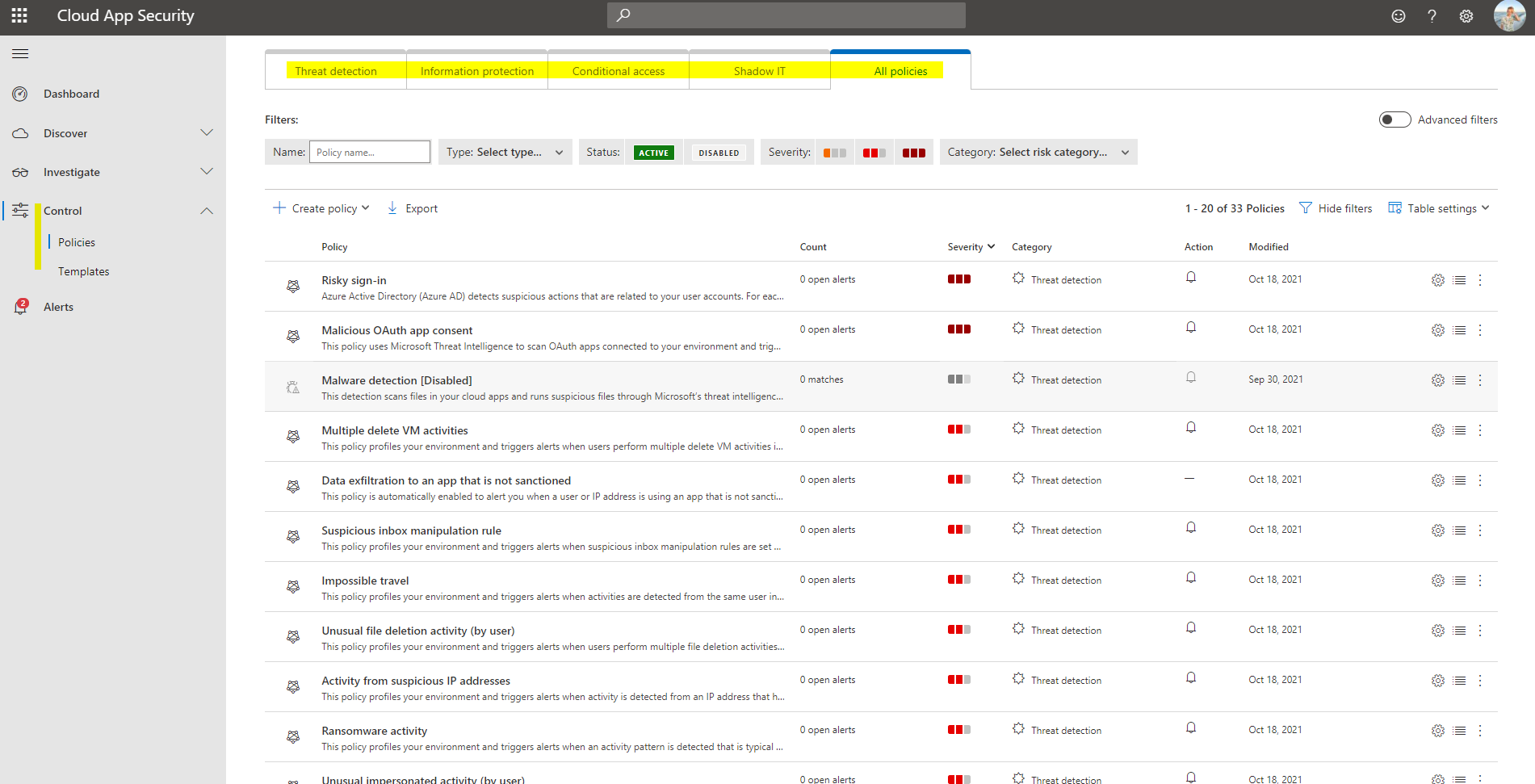
Policies and templates
Centrally, it comes down to alert definition and generation. And this is really the key point, why we are doing this. I really want you to understand the difference between a policy and a template:
- Policies - are active templates that will produce alerts
- Templates - are blueprints that can be used to create policies
Creating a policy
Let's create a policy from a template. In my case I choose "Logon from a risk IP address" and click on the + symbol at the side.
- Give it a friendly name, so you understand what it's about
- Define the severity and a category of the alert (based on that, you can act different in the future)
- Choose whether this triggers on a single activity or if repeated
- Build your own filter, based on the attributes available
- Alert handling, usually alerts always come up at the left side, but you can individually define, if an email or text message should be sent. To avoid spam, set a daily alert limit. Furthermore here you can also send alerts to Power Automate - like I did, to Teams.
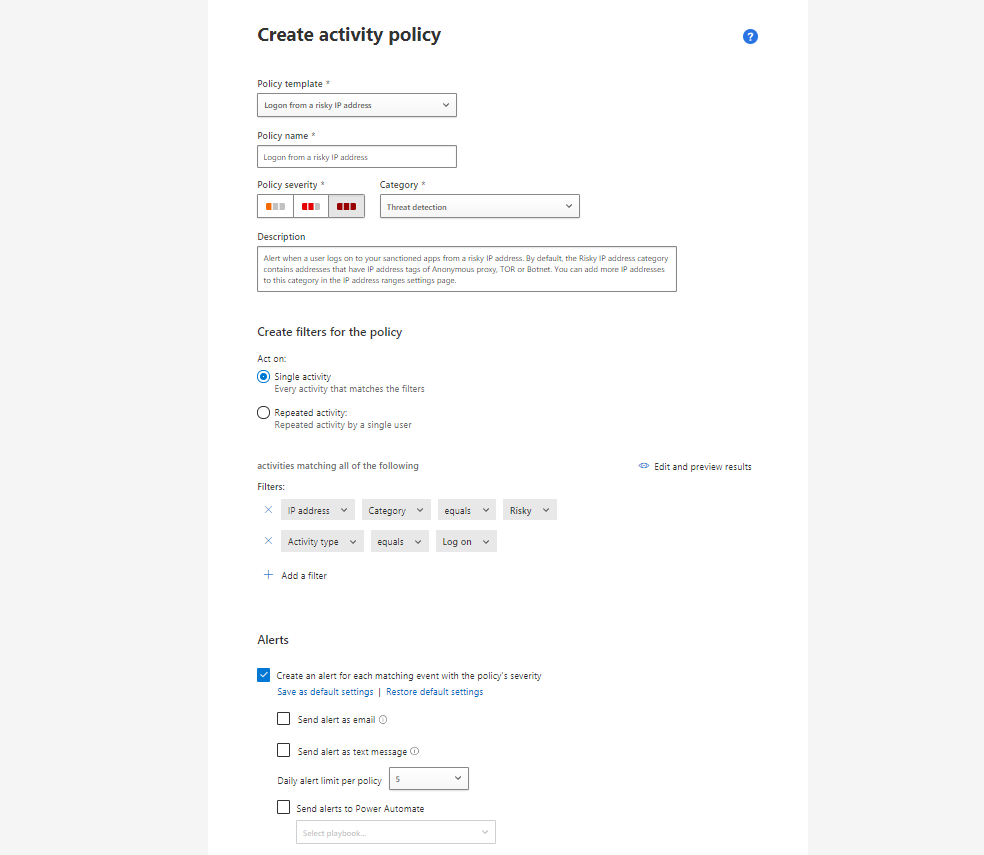
- Governance actions goes into granular controls of cloud apps. You can notify the user, suspend him, require to sign in again or confirm the user is compromised for Identity Protection.
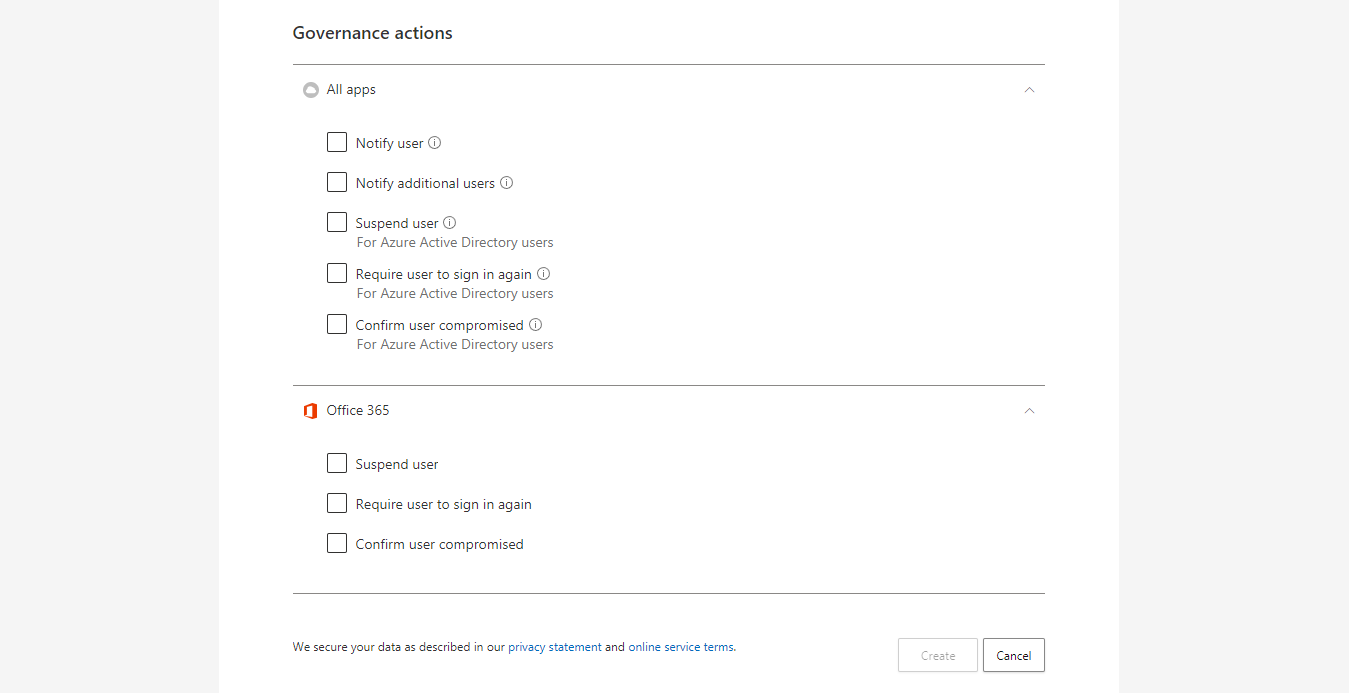
Settings
The management settings are found at the top right.
You will see a lot of configurations in this tab. I will describe some of the most important.
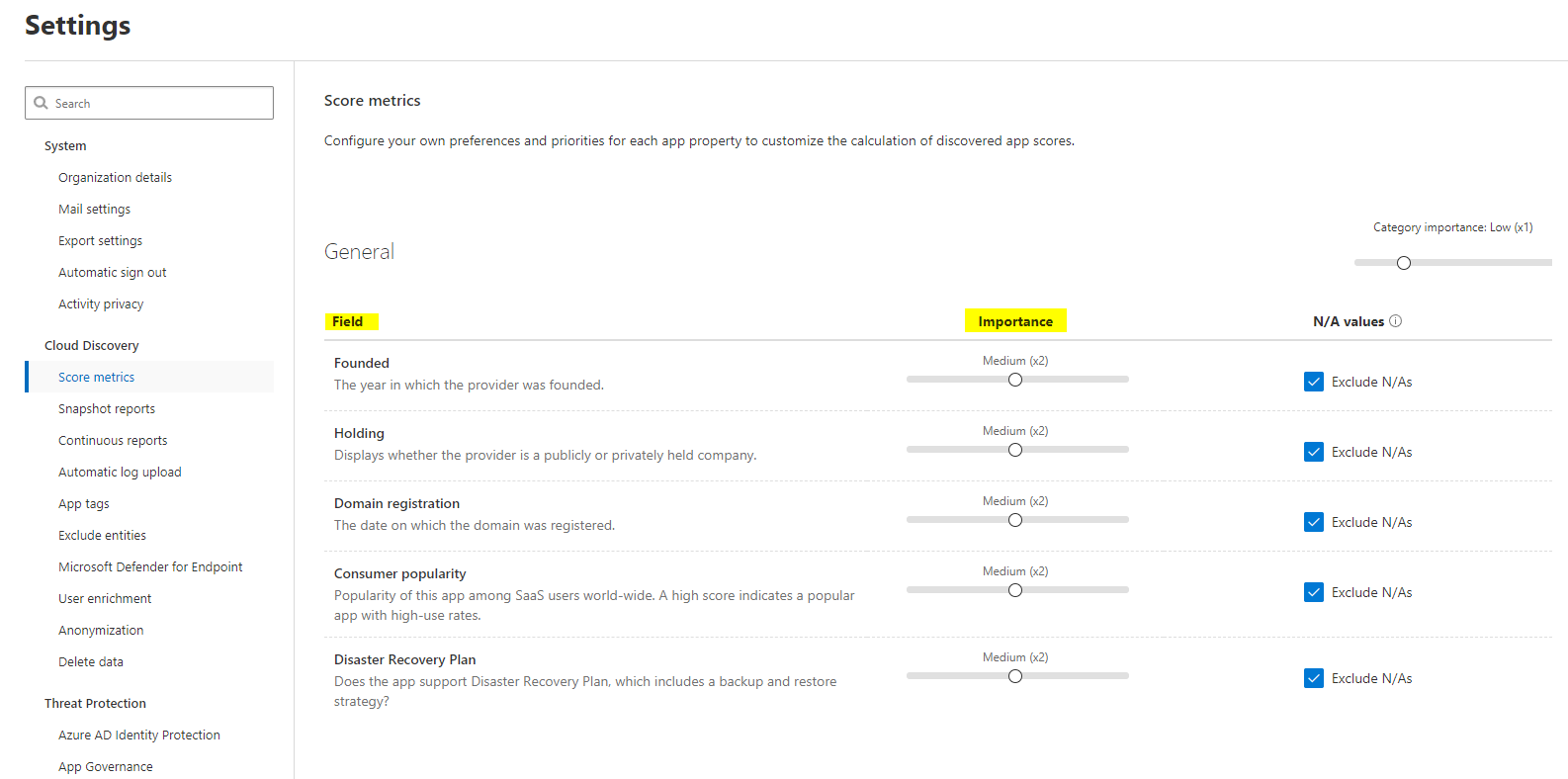
Score metrics
All applications in the Internet are rated by Microsoft in this tool. You can set a personal preference about the importance of the key attributes of each app.
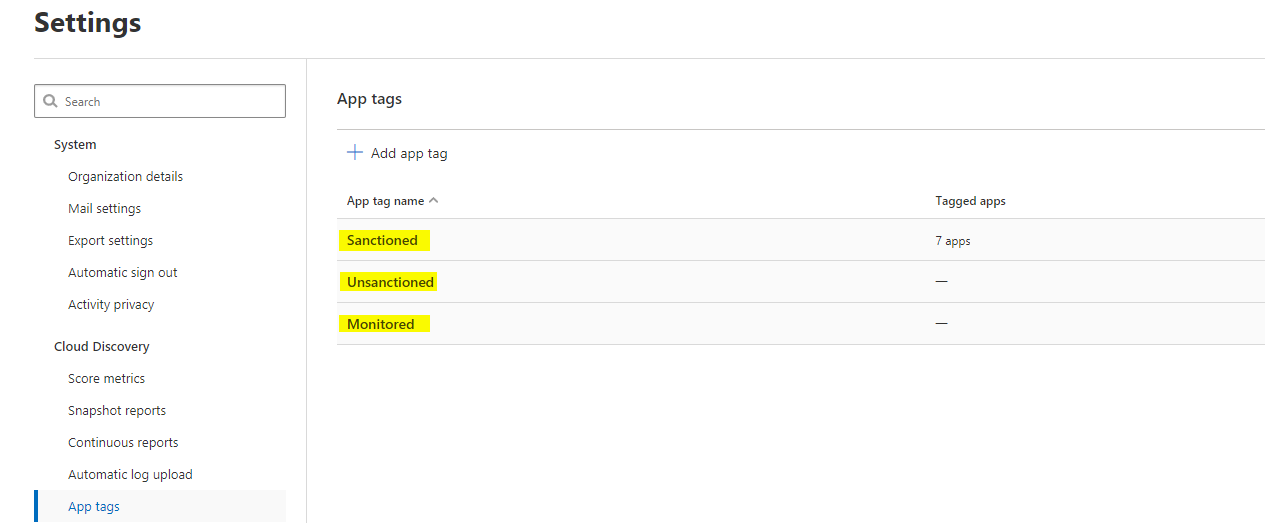
App tags
Tag apps as sanctioned, unsanctioned or monitored. These classifications can later help to take controls. This is an overview of these.
Exclusions
Here you can exclude users, groups or IP addresses from this tool, so they don't take part in any report or action.
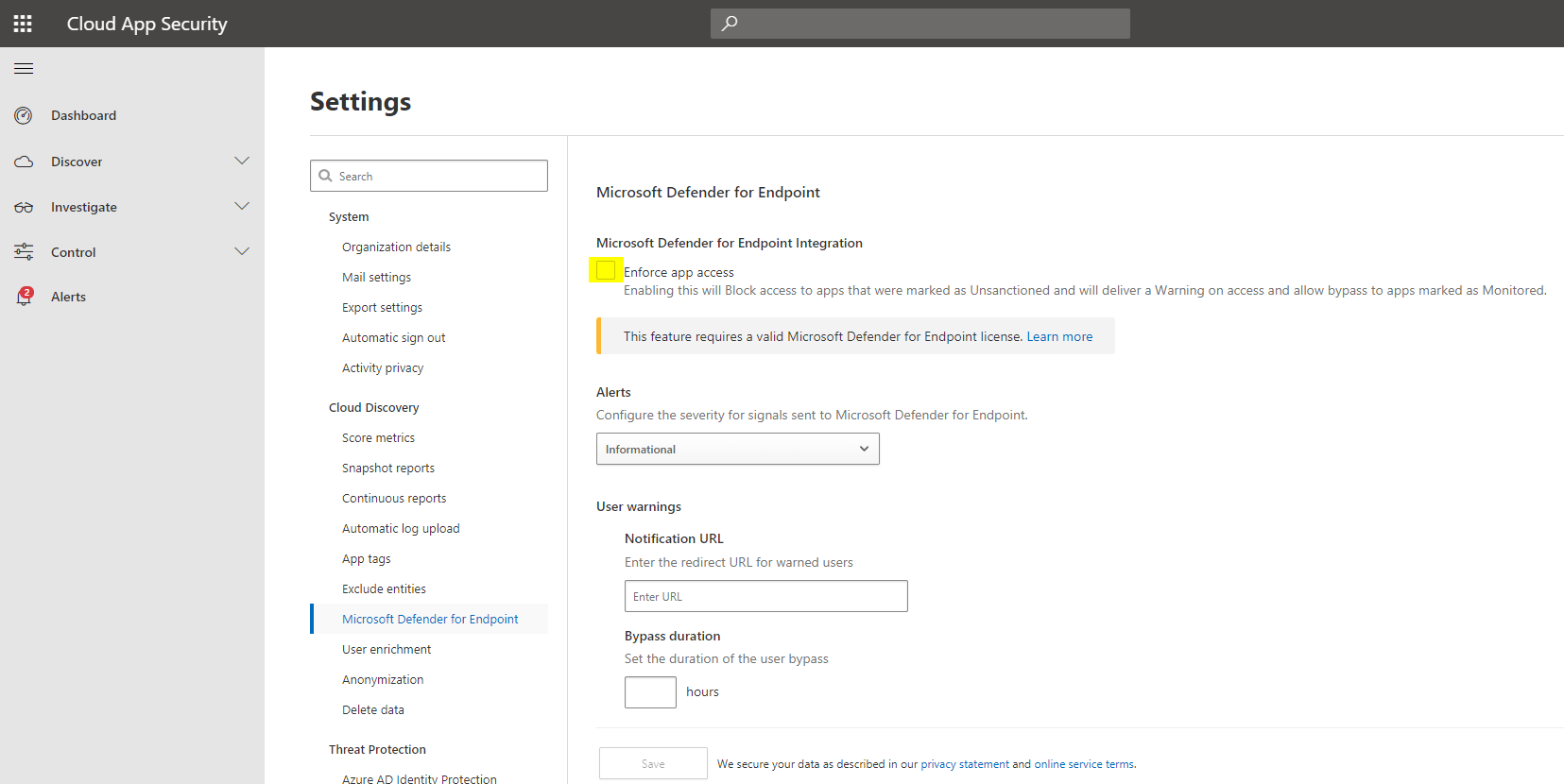
Microsoft Defender for Endpoint
Defender for Endpoint can enforce app access (in the end to a website or URL) through this page. Unsanctioned apps will not be accessible from your devices, even if they are not in the corporate network, without any proxy.
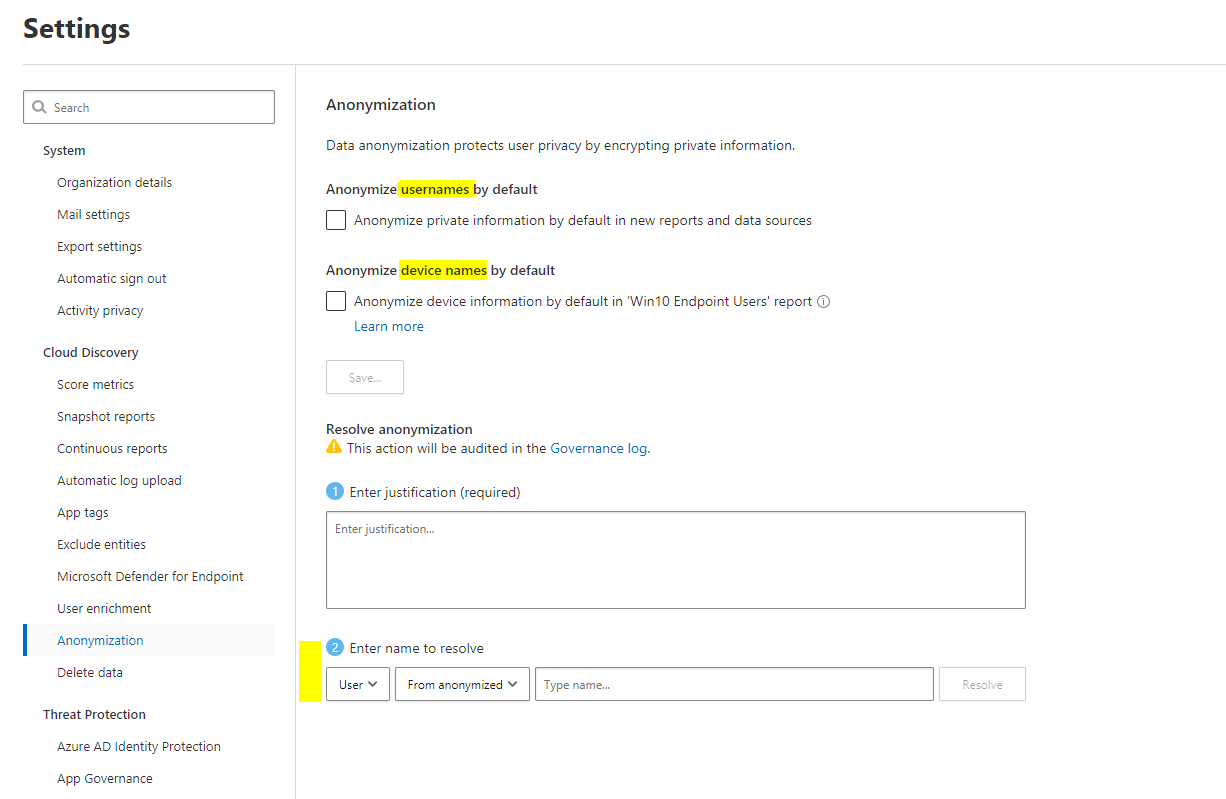
Anonymization
All data gathered, will be visible very clearly. You may want some type of anonymization through the process for user- or device names. Although trends and reports still hold metric information.
Azure AD Identity Protection
One more integration is to AAD Identity Protection to deliver identity information and determine risk levels for a user. This signals will flow into Identity Protection.
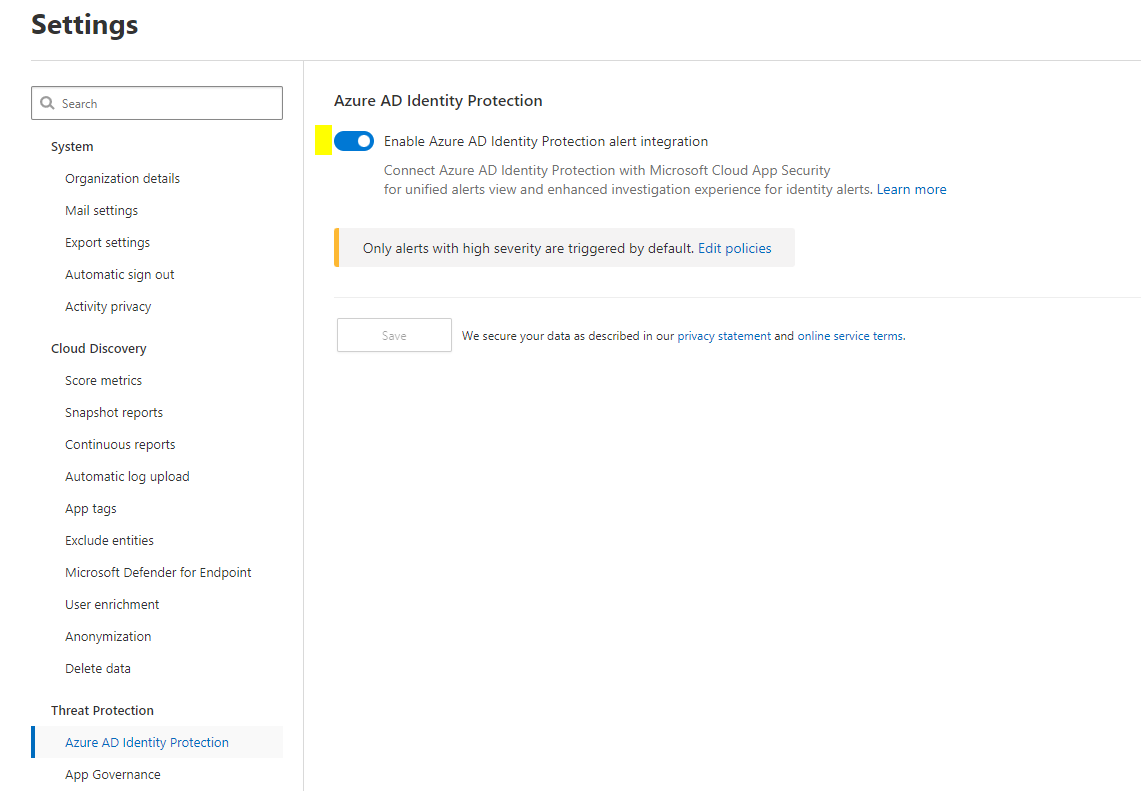
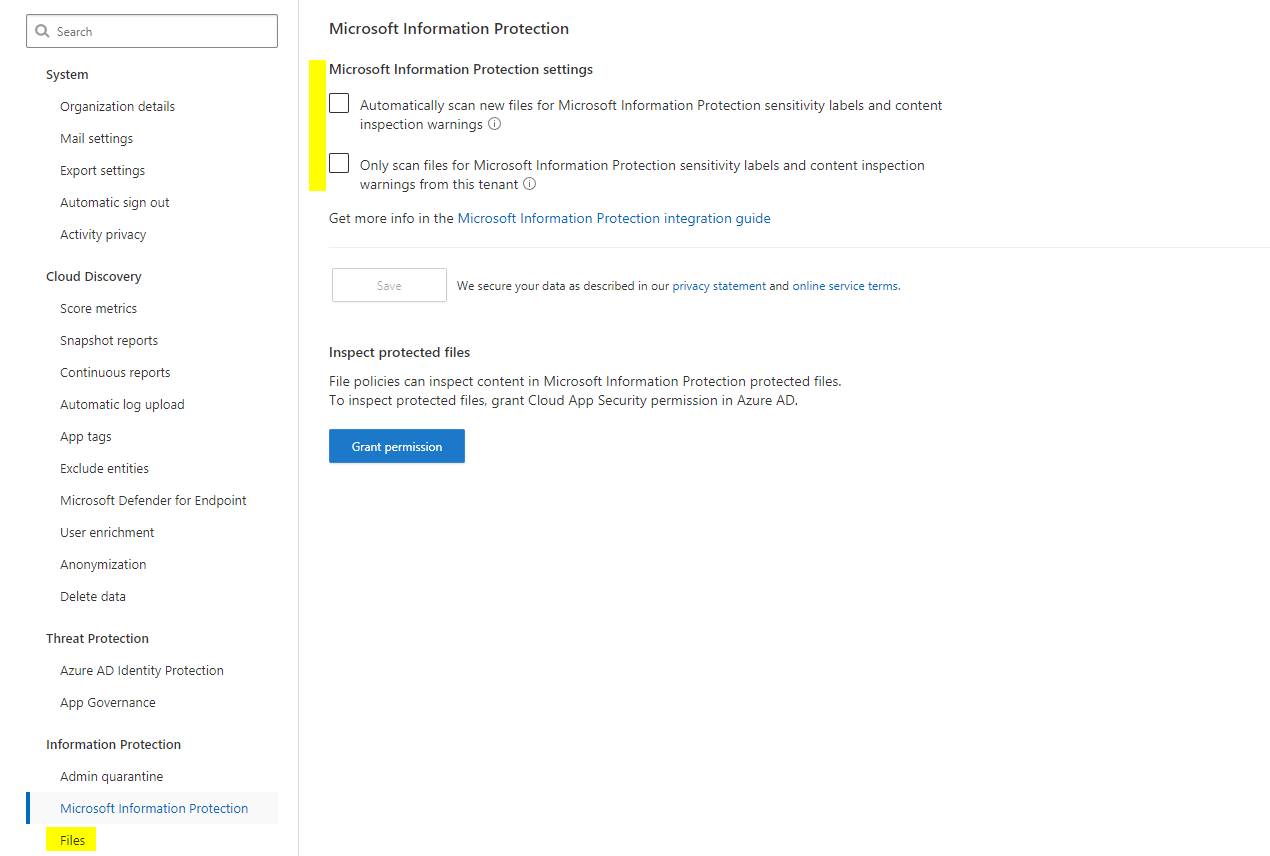
Information protection & file monitoring
CAS can also handle information protection content. Things such as sensitivity labels will have an impact. File monitoring, which is the section below this one, enables the inspection of Office 365 files.
Conditional Access App Control
This is really an advanced security function. The big thing a cloud app broker should take care of, are session controls. Conditional access as a familiar product only handles requests during the authentication of an identity. Combined with Defender for Cloud Apps, it can operate after that, within the session. For example: data downloads and uploads or authentication context on sensible tasks. But this needs an URL replacement. Learn more about it in my dedicated post.
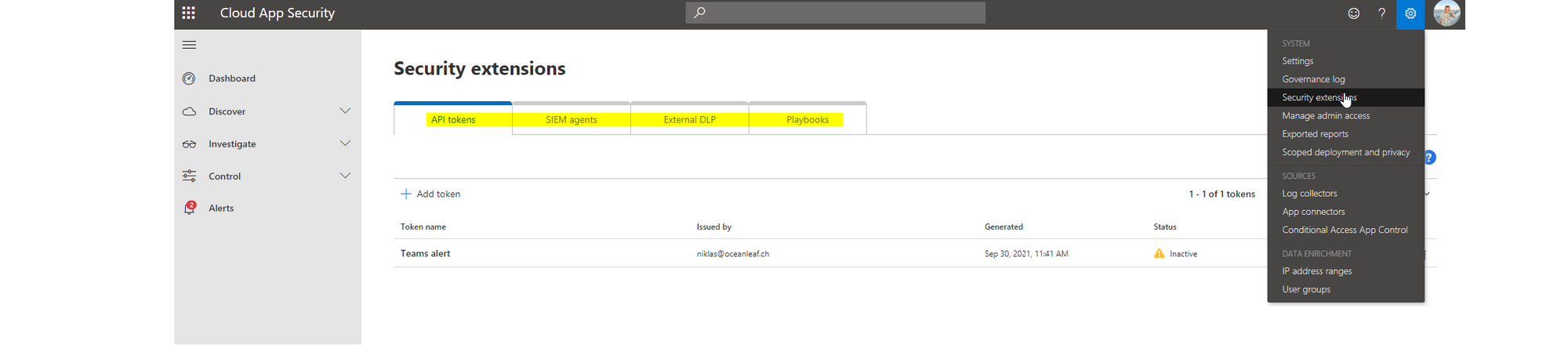
Security extensions
For even more sophisticated operations, we have security extensions in CAS.
- API tokens, are integrations to any kind of other workload, that needs to interact with CAS
- SIEM agents, security information and event management agents is the native connection to Azure Sentinel or a generic SIEM
- External DLP, data loss prevention connector
- Playbooks, are some sort of automated tasks through Power Automate within CAS or beyond it's domain (an example from the field)
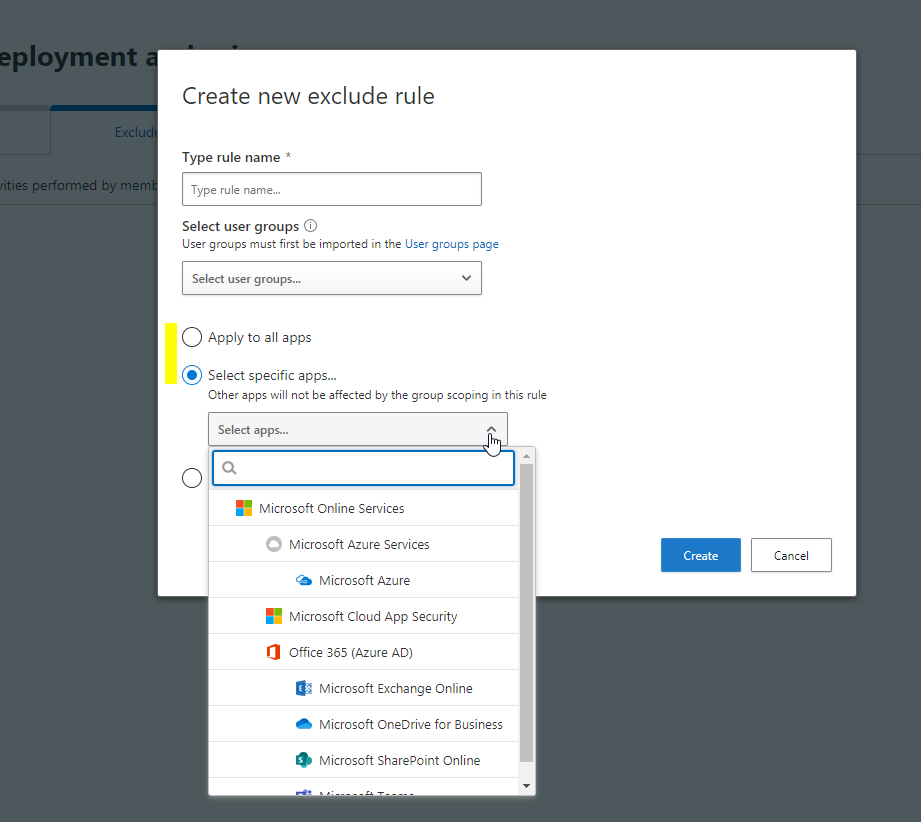
Scoped deployment and privacy
Now scoped deployment and privacy is also located at the top right and may help you with (license) compliance challenges. It assists when including or excluding specific groups is desired. The groups are CAS adoptions of AzureAD groups.
Log collectors and app connectors
How do you fill this instrument with data? Well with logs or connected apps.
-
Log collectors - one time or continuous upload (automated through a workload like Docker, that needs to be implemented manually) of log files from an appliance (usually a firewall or proxy) into CAS over network FTP or syslog. Personally I would not advice doing that, except you only have a Cloud Discovery license. Here is a list of supported appliances.
-
App connectors - this is the favored way of contributing data to CAS. App connectors is a predefined list of common cloud apps, that send data continually and are easy to activate. But you need to connect those on both sides. (also the counterpart app) What you get, is a very deep insight on how it's used.
Personal notifications
If you run small SecOps, you might consider personal notifications on alerts to your email or phone. Though, I would only activate this for alerts with high severity.
A guide
So, how do you get your daily work done, with it? CAP is a state of the art cloud SecOps tool. Either made for security engineers or cloud architects as audience. Though, it depends how much time you invest and how deep you want to go. Both ways are possible, but rely on the organizations size and their requirements.
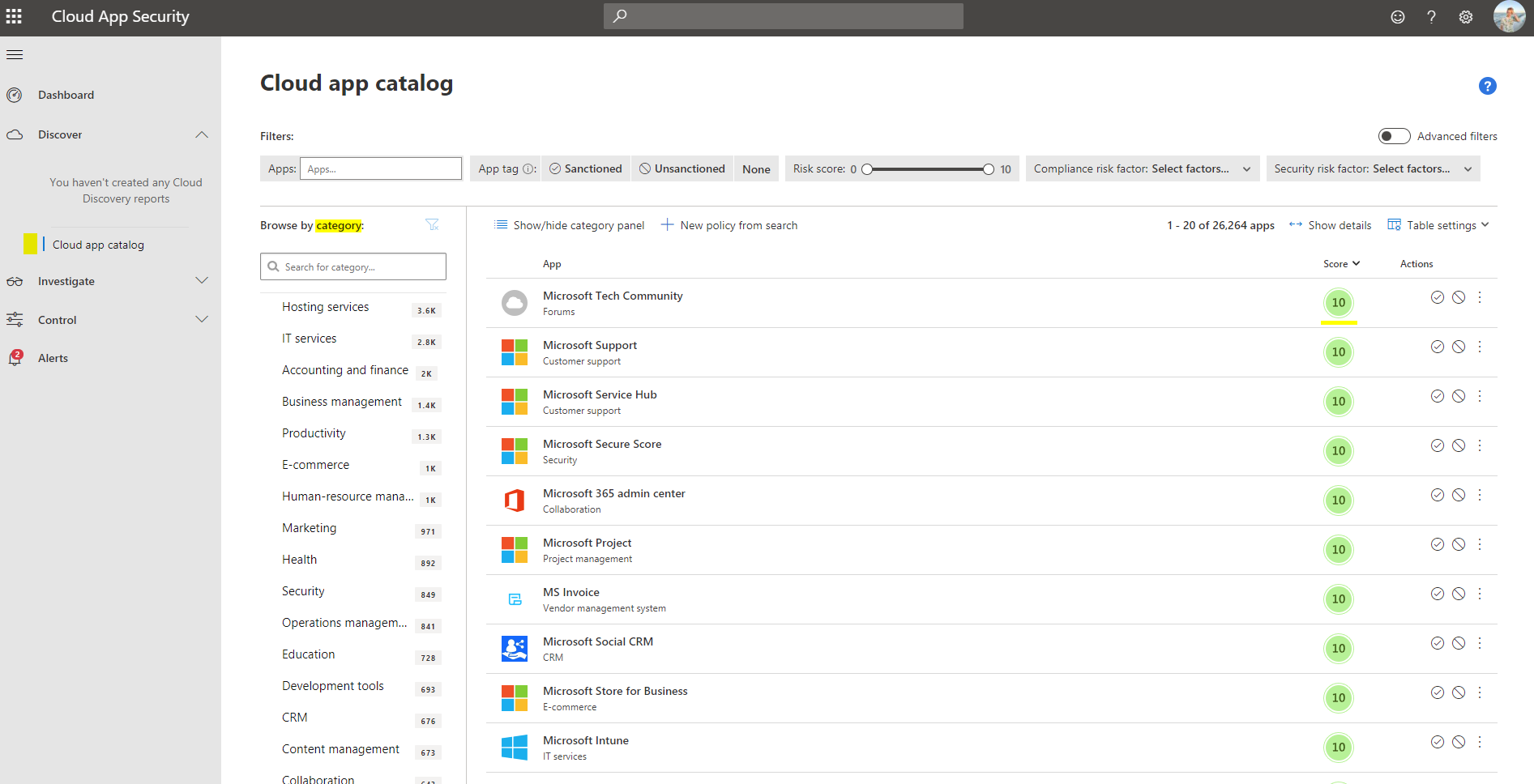
Cloud App catalog
The cloud app catalog (under Discover) is essentially a database of all Microsoft known applications from the Internet. They are grouped into categories and are scored by Microsoft. (10 is the best 0, the worst) Here you can directly (un)sanction the app.
Information - digging deeper
If you click on an app, you will see a ton of data regarding general information (founding date, headquarters, holding, data center locations, domain types and so on). The Security section hosts all relevant facts of the security posture (latest breach, encryption, MFA, certificate, authentication constructs). Compliance statistics are manifested (standardizations such as ISO 27001). Even Legal information is processed (GDPR, data ownership or retention policies).
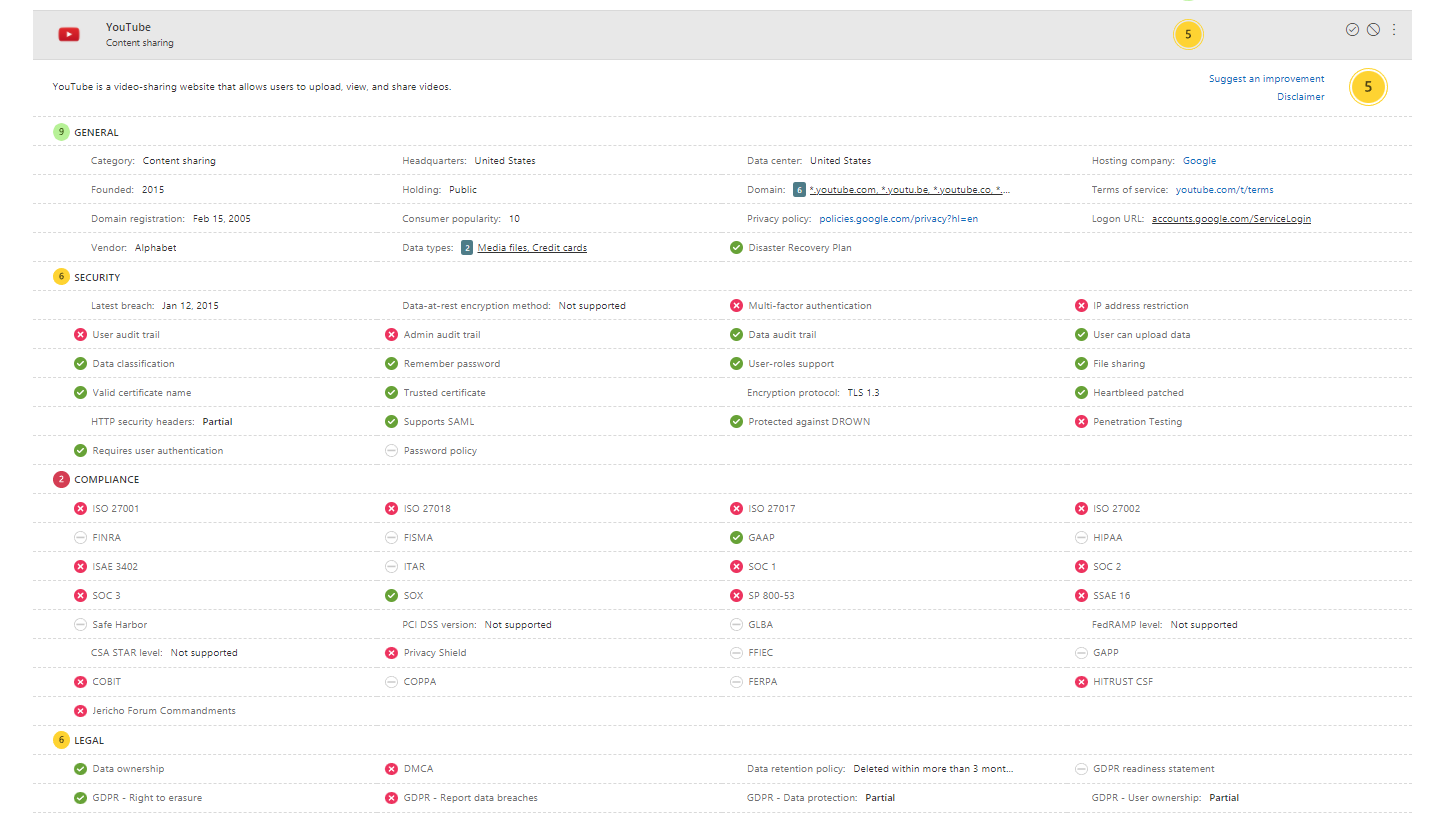
This is how future IT will work. CAS enables you to enforce policies (integrated or conditional access) of distinct organizational obligations when utilizing the cloud. For instance, if we would only be allowed to work with other companies that are ISO 27018 certified, we can make use of this. In past days you would need to gather this information by yourself or trust any source. Now it's all adopted through Defender for Cloud Apps.
Investigation
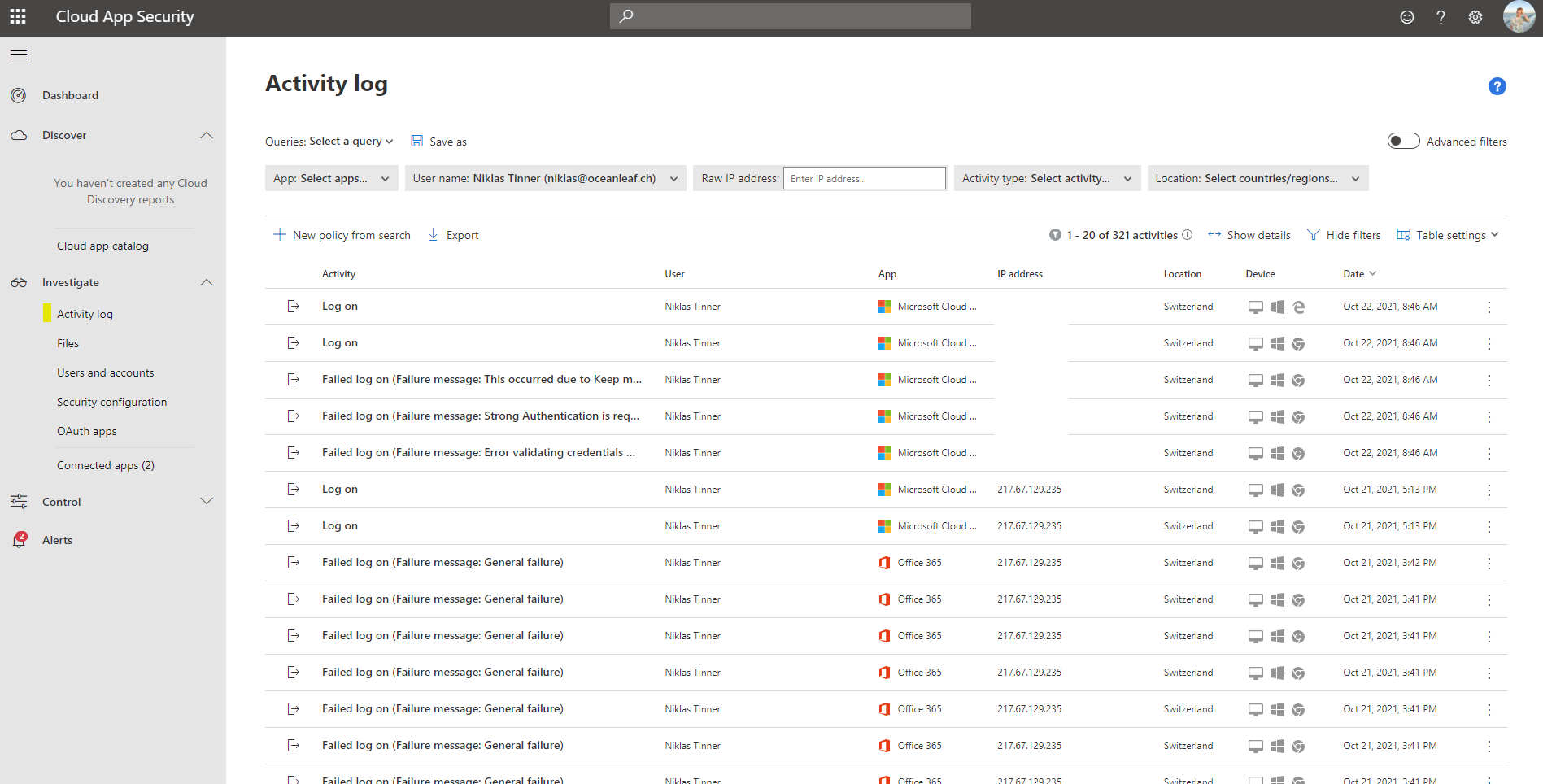
Investigation holds the primary logs of all activities. Activity log helps to understand all actions in your cloud env. Files monitors SaaS apps, that store your files. Users and accounts is a list of all principals and accounts in your tenant. The security configuration goes beyond Azure, to integrate Amazon Web Services and Google Cloud Platform. And OAuth apps indicates apps you are working with. Read more about OAuth and OICD.
Alerts
For the daily business, the alerts page is the only page you actively use. All current, past or future events of interest are collected in here. Displayed is the crucial info, involved entities, the app, a status, the severity + the date of which the alert occurred.
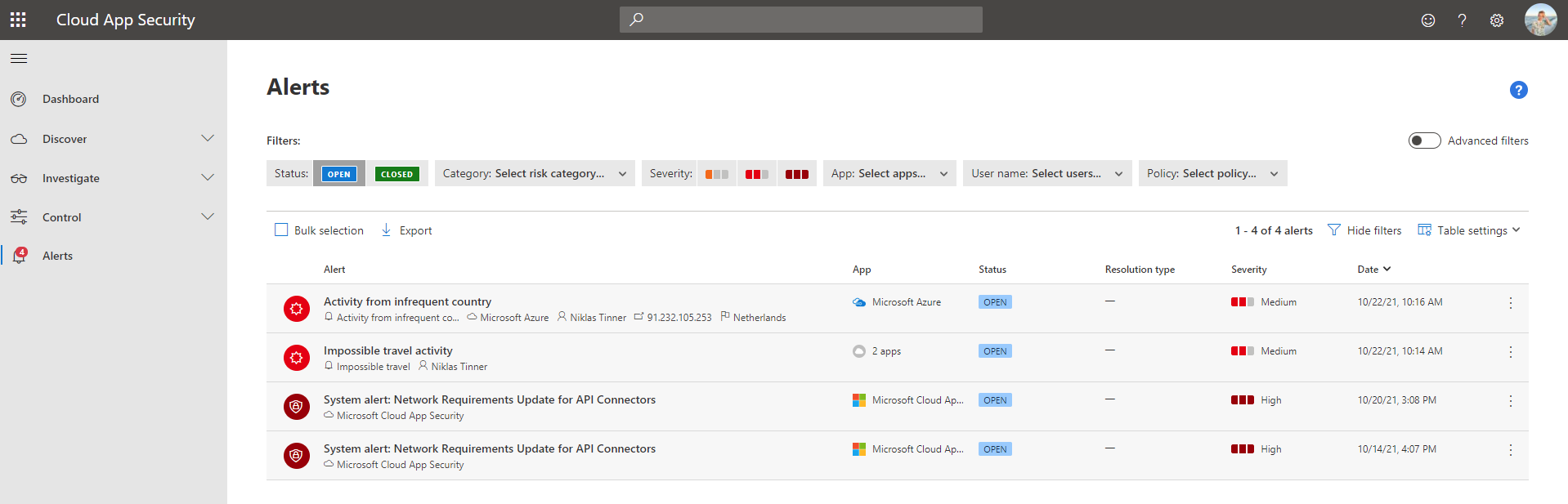
A SecOps investigation sample
I want to give some explanation on how to treat such alerts.
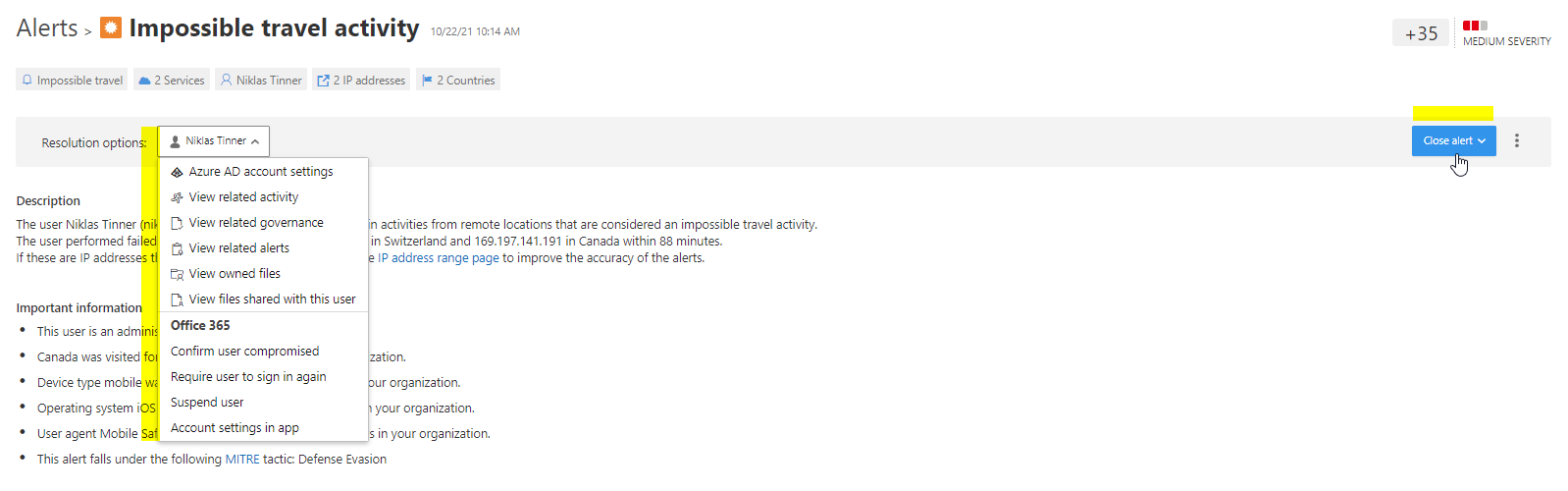
The Impossible travel activity is a common alert, that gets triggered, when a users signs in from two or more IP addresses, that are associated to a country, within a timespan that physical travel would not be possible. Something like this:
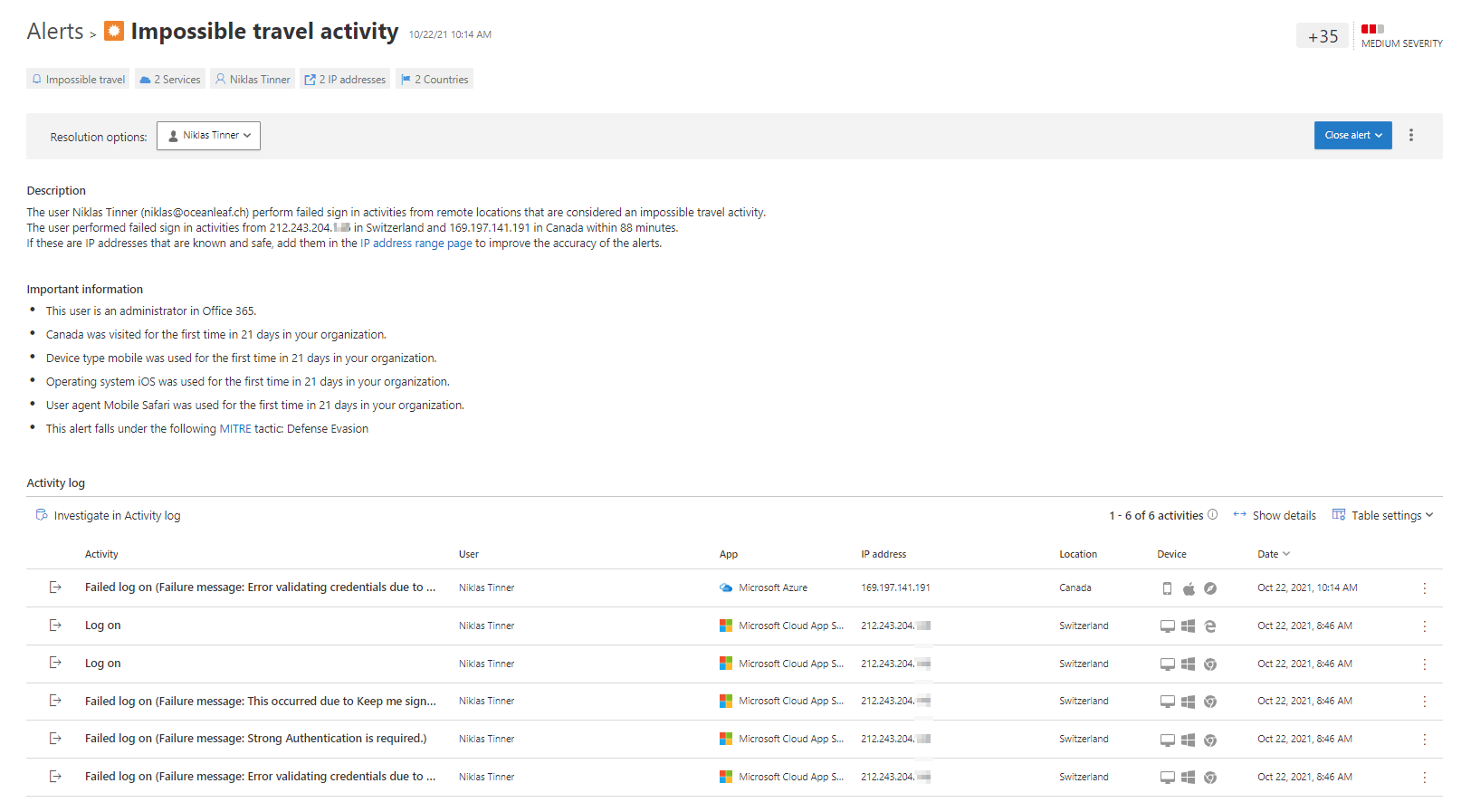
There is always a summary at the top, giving a short briefing what we are handling with. A description explains what happened in full sentences. On the other hand, important information tells you, why this activity was suspicious - here I logged in from Switzerland and Canada in a time period of 88 minutes. Canada was visited the first time in 21 days in my organization. It even addresses (if available) it to a MITRE (known attack methods, MITRE ATT&CK) tactic. Then, in the activity log you see each action, that it correlates to.
Responding to the alerts goes over resolution options or individual measurements. By default, there are some mitigations or advanced investigations recommended. Finally, close the alert and specify false positive, benign or true positive.
+
Another alert is Activity from infrequent country. Usually coming up, if a user logs in from a completely new location. Thats just rather rare, besides of vacation. We see the same structure again, just with other values.
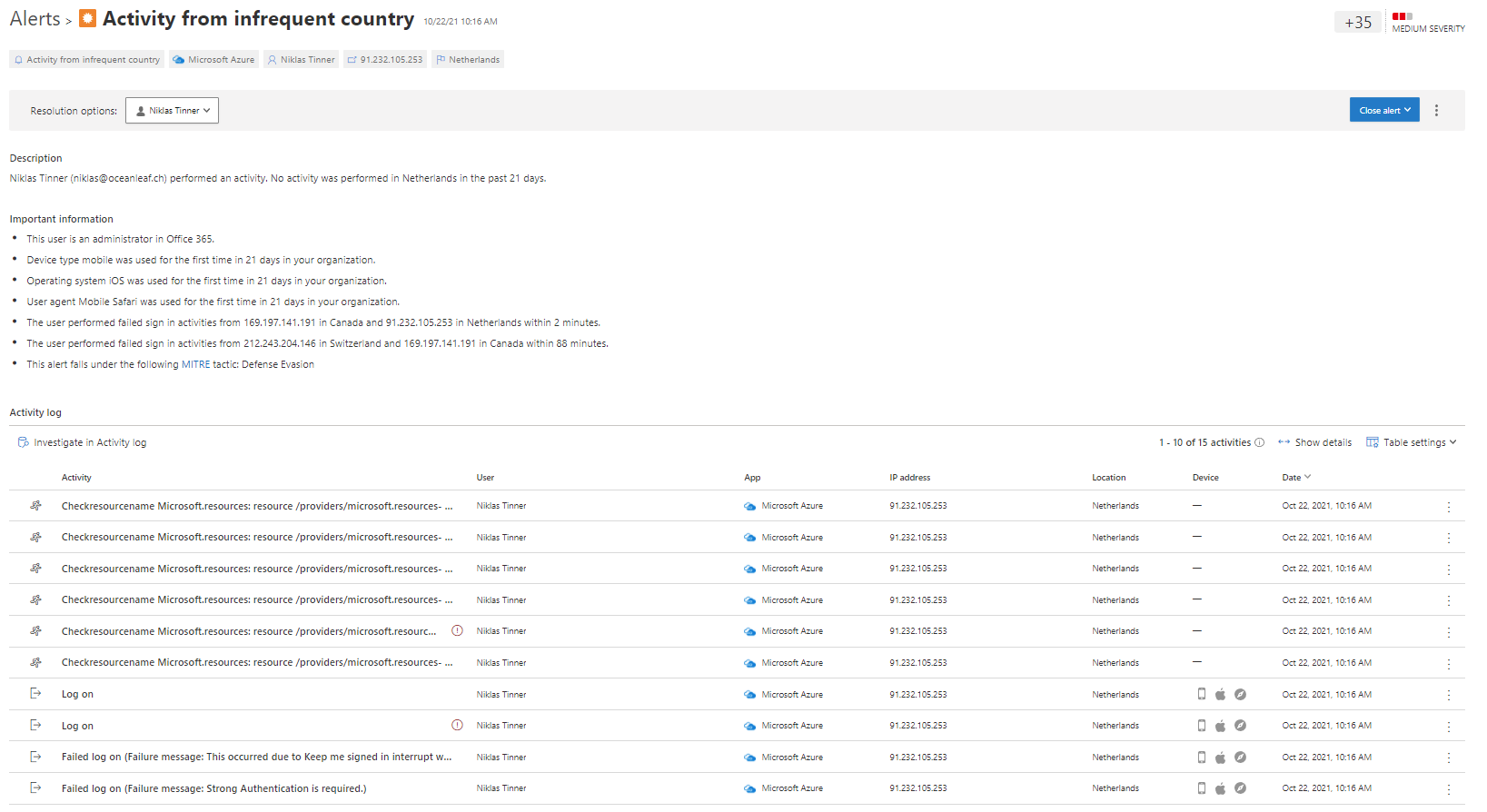
This time, the activity is also tied down to the session actions, such as Azure resources. The best way to learn operation with alerts, is generating some test alerts and clicking on the links to investigations.
Conclusion
Microsoft products work best, when they are connected to each other. I consider Defender for Cloud Apps as a substantial part of your security environment, when we talk cloud. Especially connected to AzureAD and Microsoft 365, in specific to Defender for Office 365 and Defender for Endpoint, it is very powerful. With a SIEM and SOAR even more - automation is key. And the cloud app catalog is something like a holy book in IT for cloud apps. Many game rules did and do change, and with CAS you are well positioned against threats and anomalies in your cloud posture. App connectors deliver an even greater experience for IT admins to govern interconnection and relationship to apps. Joined to Defender for Endpoint, web protection is on it's highest level, needing no physical management server hardware. Of course there are new challenges, awareness thoughts and boundaries, but I feel like, they are on advanced technological level. If you are cloud native or plan to be, this product is a must have! That's for sure.
