Autopilot White Glove Hybrid AzureAD Join
Recently Michael Niehaus has posted an article Digging into Hybrid Azure AD Join. He is explaining concepts of (Azure) Active Directory join's. Unfortunately he didn't mentioned Autopilot White Glove Hybrid AzureAD Join while on corporate network, which is my usecase. So I decided to comment my question so somebody can help me out. Good news: Michael Niehaus wrote me personally. Well besides I feel very honored he also served me the answer to my question. I will now give some information about this process in this post.
First we have to clear some definitions:
- Azure AD (Join) - this is a pure Cloud based Active Directory with no on-premises authority
- Active Directory (Join) on-prem - this is only offline with just a domain controller that is the main authority for directory services
- Hybrid Join - the best from out of two worlds. AAD (AzureAD) and on-prem AD is able to manage the device (e.g. device is enrolled with Intune and has local GPO's)
- Offline domain join (ODJ) - domain join over the Internet without direct connectivity to domain controller. Intune Connector generates an ODJ policy from DC, then sends it to Intune which will afterwards send it to the device, so for this the action Intune Connector is required
- Autopilot - the whole process of Windows deployment with Intune
- White Glove - in OOBE (Out of the box experience = remember the screen when receiving a new device with language settings, keyboard, EULA and (luckily not anymore) Cortana) to do a administrator pre-provisioning.
Source: Microsoft | this is accessible by pressing the Windows key 5-times in OOBE
Technical flow of Autopilot White Glove Hybrid AzureAD Join
- Any kind of registration for the device (with the distinct device id) to the individual tenant
- Device is in-house and in OOBE, subsequently Autopilot provisioning starting
- Device contacts Intune for configuration profiles (only for the device, because it doesn't knows any user, unless you already assigned a user in Intune)
- Due this is Hybrid Join and a device configuration profile with Hybird Domain Join Intune will first require an ODJ (offline domain join) from the Intune Connector
4.1 Intune forces all settings/apps on the device to apply these - Device launches query to find SCP (service connection point) to get AAD tenant information. Described in the post of Michael Niehaus.
5.1 DC delivers AAD tenant infos
5.2 Device updates attribute userCertificate with self-signed certificate to be participant of the next AAD Sync - & 6.1 Azure AD Connect Sync from on-prem to Azure
- Device is ready for reseal/provision and User specific OOBE (now fully Hybrid AAD Joined)

Visual Concept of Autopilot White Glove Hybrid AzureAD Join
Next steps for the User
- Now with the device ready, user will attempt to start up the device and get into Lockscreen of Windows or OOBE.
- Kerberos Credentials are checked against Domain Controller
- User Enrollment Status Page contacts Intune with user relayed settings/apps and downloads the content to the device
- Device finally setup in Windows, ready to use (as soon as no ESP error occurred ;))
- Any user which signs in will get a primary refresh token (PRT) from Azure to authenticate with Azure AD services.
-Make sure that device is synced to Azure, otherwise Azure won't provide a token
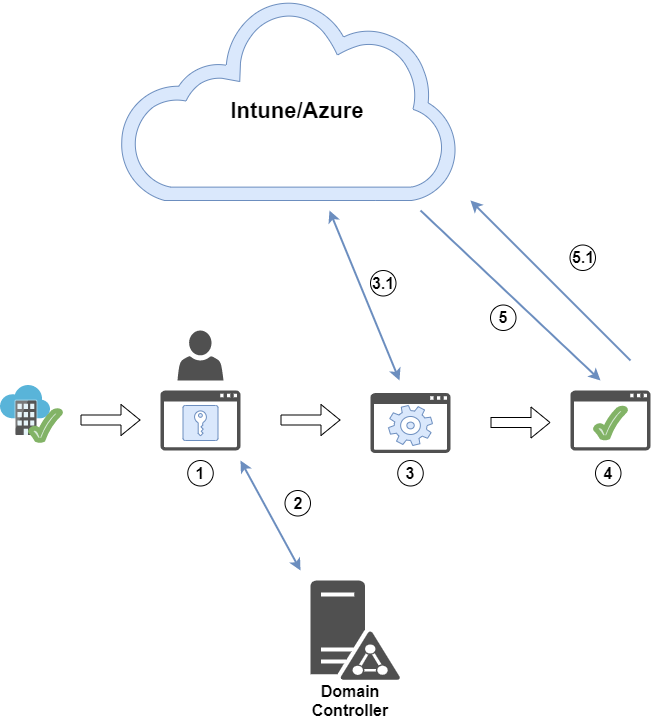
Visual Concept for technical flow for the enduser
Definitely check out Michael Niehaus' Out of Office Hours Blog, where much information comes from.
