Defender
Enterprise security solutions, cloud-based, intelligent and automated security responses for Endpoint, Identity, Office 365 and Cloud Apps. A full protection stack.
Defender for Endpoint
Handle threat and vulnerability events on endpoints to prevent malicious and harmful contents.
Microsoft Defender: a review
A review of Microsoft Defender + Defender of Endpoint (MDATP). Technical overview of capabilities, as well as my personal opinion.

Defender for Endpoint base configuration
This post is a part of a series where my plan is to focus on the implementation and operation of Defender for Endpoint. The product Extended detection and response (XDR) is the intentional purpose of Microsoft Defender for Endpoint. Meanwhile it can do a lot more and offers industry leading
Move to Defender for Endpoint: some personal experience
What to expect Microsoft Defender for Endpoint and my personal experience, thoughts and ideas to implement and operate with this product, is what you can expect. Based on a real scenario and from the field. I will cover topics from moving from a thrid-party endpoint security solution to Microsoft Defender

Defender for Endpoint security settings management summary
Introduction This post is a summary for Defender for Endpoint security settings management, also known as Unified Settings Management. It will walk through all necessary steps to understand, plan, setup and use the features. Furthermore I will give recommendations for field deployments, tips and more. There are already some good
Defender for Identity
Monitor on-premises identities and correlate activities with other cloud security products to get a deeper understanding of your environment.
Defender for Identity fundamentals
General Defender for Identity (DFI) is an on-premises agent which observes the entire on-premises Active Directory activity and sends it to the cloud for further analysis and correlation through other products. See the architecture topology: Source Microsoft It is not directly developed to respond to events, but helps to understand
Defender for Office 365
Secure messaging & collaboration, which is the biggest attack surface with native Defender for Office 365 capabilities.
Defender for Office 365 fundamentals
The use case In cybersecurity we consider the Internet and office applications as the biggest attack surface as most of us have interactions to these two matters, making them extremely comprehensive and diverse and unfortunately lucrative for attackers to try to breach in our actions. We try to counter them

Launching an attack simulation training
The idea Most enterprises use email systems to communicate with internal colleagues, other companies or customers. The exchange of information represents a potential security concern, as adversaries could use it to attack end users. Technical measures do not always provide sufficient protection, so competence and awareness in security is required

Defender for Cloud Apps
Discover and manage interactions with cloud applications across your tenant.
A tour through Defender for Cloud Apps
Microsoft Defender for Cloud Apps (CAS). A cloud broker - probably one of the most powerful tools regarding security and compliance in the cloud cosmos. If you are completely new to all these topics, I would suggest to read about the M365 security concepts before. Here is an official Microsoft
Defender for Cloud Apps: some concepts and how to get started
Beside Defender for Cloud Apps as a product, which is featured in this post, my intention is to give more operational insight and a guide to successfully understand, plan and run Microsoft Defender for Cloud Apps. Before reading this, I would highly suggest to read the first post. Solution overview
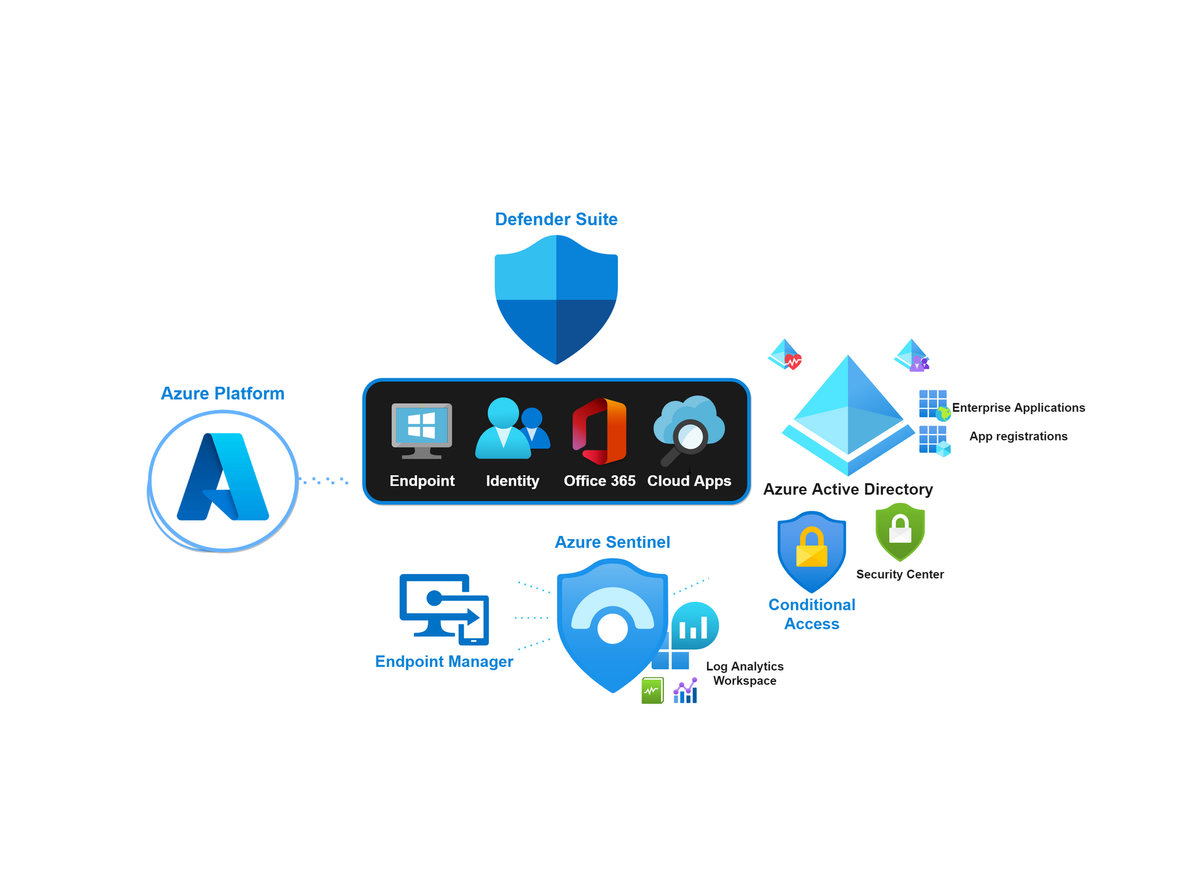
Correlation
Microsoft 365 Cloud Security correlation
If you ask me, Microsoft’s biggest advance and unique selling point in terms of security is the diversity of their feature offerings tied to the non-security products and the correlation between them. Always backed by the ability to retrieve all kinds of data from the past or in real time,
Reports
Security Reports in M365
This blog post is about reports from Microsoft 365 Security also known as Microsoft 365 Defender. As a prerequisite, one or, in the best case, several Defender products should be set up. The objective My initial objective was to obtain a high-level management summary of our Microsoft Defender cloud environment,


