Intune best practices
Introduction
This post is a summary of brief descriptions to technical Intune best practices. To deliver a true modern workplace these topics may be considered. You may also be interested in one of my other posts:
- Tranisition to modern Endpoint Management
- Intune challenges
- A full series on everything about Intune
Topics
Universal device management
Intune allows to manage all types of OS, from Windows, iOS/iPadOS, Android, MacOS, Linux and Chrome OS. Platform support is given for all of them, resulting in the fact that you only need one product for all. Intune is the state-of-the-art mobile device management in the cloud. It only makes sense to shift all your device workloads to be managed with Intune.
Windows 365
Virtual machines can be served through Azure Virtual Desktop or Windows 365 in Azure. Windows 365 is a subscription-based cloud PC that is provisioned and managed through Intune. This means that you can manage all devices (physical/virtual) in just one console. This benefits the operations, user experience, security and costs.
Governance
- Intune roles (custom) - general role-based access control (RBAC) to grant different users different permissions. Custom roles can be created to define individual permissions.
- Scope Tags - granularly control access to a subset of Intune objects. (In large Intune environments this helps to restrict access to e.g.: a department or location of the company)
- Multi Admin Approval Public Preview feature that allows a request/approval process for Intune objects. This is a dual control mechanism.
- Privileged Access Groups Preview to manage Intune custom roles with the functionalities of privileged identity management (PIM).
Deep dive into these topics: Intune scope tags and role-based access control explained - Nicola Suter
Updating
Windows Update for Business
When talking about Windows Update for Business, you should know the following technologies:
- Windows Autopatch - an Intune feature to automate the update deployment on your clients. Microsoft does an evaluation of your environment and registers endpoints automatically in update cycles.
- Windows Update for Business deployment service - the cloud-service in the background that allows to control Windows Update (essentially, if you configure a WUfB policy anywhere, this will leverage the deployment service on the endpoints)
For a proper update management, you will have to consider the following:
- Deployment schedule
- Feature updates are now only coming once per year.
- Quality updates arrive on the Patch-Tuesday and feature updates once per year.
- Security updates often come out-of-band or quality updates need to be expedite -> use targeted Quality update deployment.
- Testing
- Usually tests are done to guarantee general functionality and compatibility with the business before rolling out an update.
- Tests are most often shifted to stakeholders and pilot users, the IT department only does minimal (first) testings.
- Feedback collection is key to take actions. Think about Microsoft Teams channel to group and address issues that users identified.
- Safeguard holds are a built-in mechanism for secure & reliable update deployments.
- If any major issues are detected during testing, the update channels can be paused for 35 days maximum.
- Rings
- There should be at least 3 update rings, where quality and feature updates are deferred.
- Ring population
- The ring population can include device or user groups. A mixture is generally not recommended. There are pros and cons for both of them, but I prefer the user groups since they better address a staged deployment mindset.
Windows Update for Business reports
WUfB reports is a must to keep track on all the update deployment status of your endpoints.
Edge & Office updates
The integrated Microsoft applications should also have controlled update policies.
- Edge is recommended to be in the Stable channel. Below you can see my recommended policy. (Channel overview)
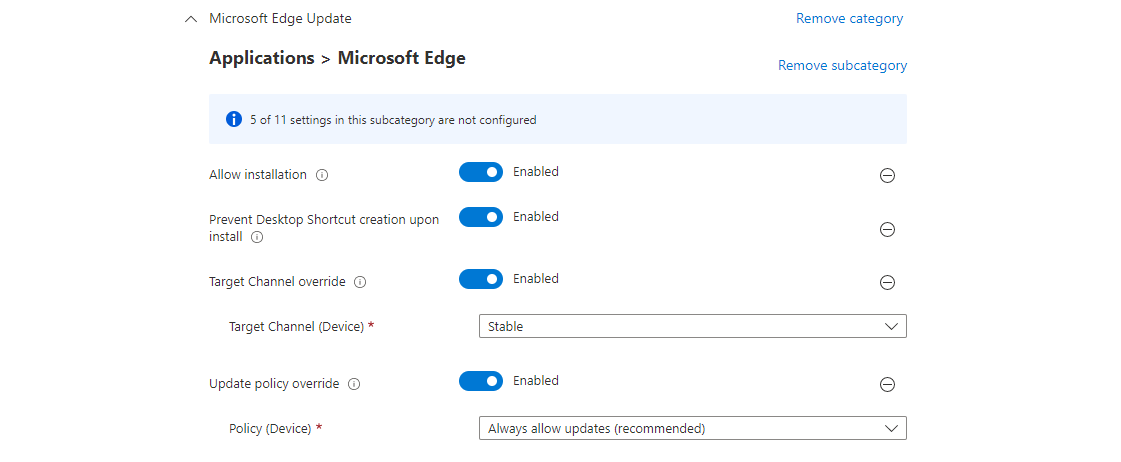
- Microsoft 365 apps/Office also offers different channels, where the recommendation is to be in the Monthly Enterprise Channel. (Channel overview)
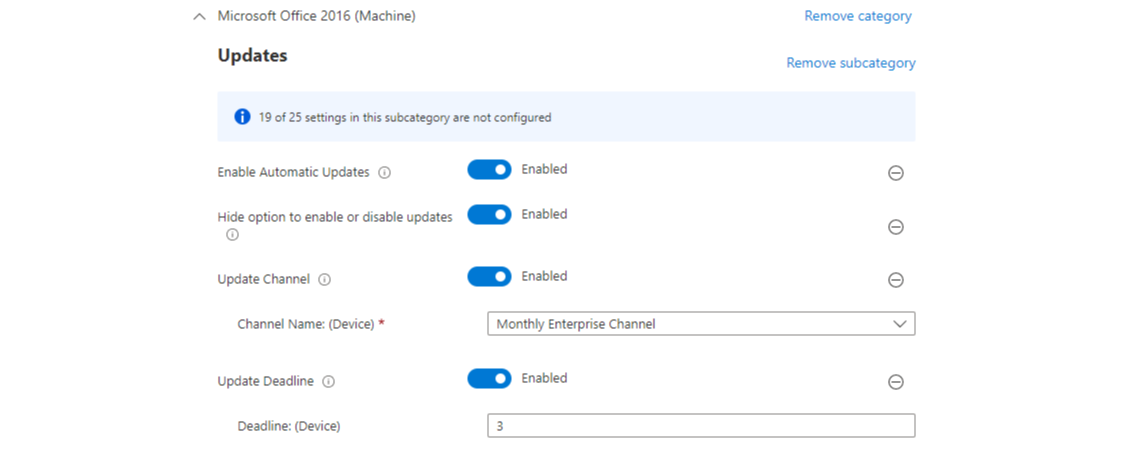
Third-party app updates
Of course also third-party apps need to be updated. The following approaches are found on the field:
- App has auto update integrated. This is theoretically the best option, but you may not have as much control over tests & deployment.
- Microsoft Store apps. The familiar updating process for Microsoft Store apps will automatically install new versions in the background. Nevertheless the Store should be configured to private only, to prevent arbitrary software installations.
- Winget update. Winget has the capability to update packages that are stored in the winget repository, though this must be manually triggered and is not included with Intune yet.
- Third-party tools like PatchMyPC. Other tools may source a dedicated repository with applications that are regularly updated. This is the most common approach at this time.
- Manual process with line of business apps. For any internal or business apps that have local installations, you often result in manual packaging effort. These should be regularly updated, if the vendor publishes a new version.
Automation
Architecture landscape
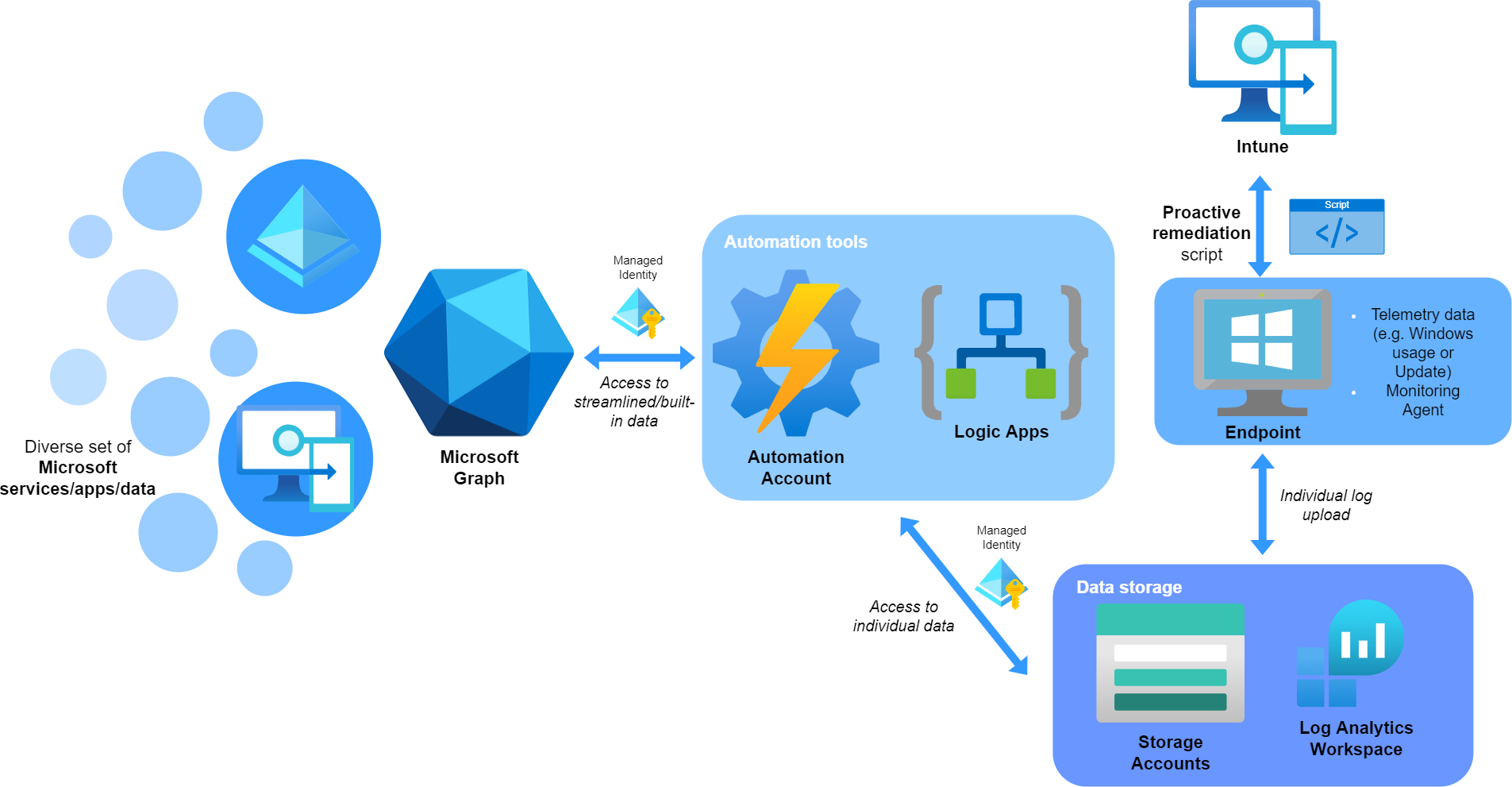
So for any use case that is not covered through built-in tools, you may take a look at a combination of the following products:
- Proactive remediation - an Intune feature to deploy PowerShell scripts that detect and remediate issues. The results are reported to Intune, but sometimes it makes sense to write local log files or store information to an Azure Storage Account.
- Graph API - the central Microsoft data & intelligence service Read my basic blog post about it
- Automation tools
- Azure Automation - to automate tasks with mostly PowerShell scheduled scripts
- Logic Apps - include low code process flows with various connectors Read my blog post on it
- Data storage
- Storage accounts - storage data blogs, files, queues and tables and make the data available
- Log Analytics Workspace -Read my blog post on it
Secure identity principals
Managed Identities provide secure access within Azure resources. Whenever you start to develop a (cross) solution on Azure, you should implement them.
Security
Baselines
Endpoint hardening is an essential component to a modern workplace. For the Windows part, there are integrated baselines. My advice is to configure the endpoint security topics manually. Orientate with the Security Compliance Toolkit or with other institutional security frameworks like CIS. A few general tips can be given although:
- Make sure the baselines are applied to any endpoints and avoid exclusions
- Regularly update the baseline version to align with the product
- Monitor the security configuration profiles and/or apply Intune governance
- Implement a process for exclusions and changes that involve a security role
- Document any deviation or change to a security baseline
Authentication with Windows Hello for Business
Windows Hello for Business raises the security and benefits the comfort for the end user.
All modern deployments should include a Cloud-only/Hybrid Cloud trust. Read more
Defender for Endpoint
Now for extended detection and response (XDR) Microsoft's Defender for Endpoint ideally complements with a native integration to Defender Antivirus and Intune. There are two license plans:
-
Plan 1, included in Microsoft 365 E3 and therefor eligible for many customers enables centralized management and next-generation protection.
-> Bascially mandatory in my opinion if you do not have a third party antivirus. It will give you a focus on security, for especially the centralized management and (manual) response actions on endpoints from the security portal, but has clear limitations. -
Plan 2, included in Microsoft 365 E5 (security add-on) delivers the full endpoint protection suite with features like device inventory, threat and vulnerability management, automated response and advanced hunting.
-> The full set of functionalities to perform security operations. This requires more expertise to maintain and operate, but will equip you to do nearly everything from a security perspective.
More about licensing in the world of M365
Apps
The modern app deployment with Windows is named winget. This is the built-in package manager tool for any widespread used applications. Integration to an own repository is also possible. Essentially there are two app types in Intune:
- Winget (source)
- Winget repository or vendor specific - winget packages (find with 'winget search') from the winget repository
- Microsoft Store (also known as Universal Windows Platform - UWP)
- Win32 - custom packaged applications and deployed with Win32 content prep tool + Intune
Logs - Azure Workbooks
Your Intune operations can strongly benefit from forwarding events to a dedicated Log solution. This enables to query all inventory data with KQL or leverage powerful Azure Workbooks that give insights. By default audit data is stored for one year in Intune. The platform solution includes:
- Requires the Intune platform data to be sent to a Log Analytics Workspace (LAW)
- Azure Workbooks are visualization of queries to the LAW data - Take a look at my Intune change tracking workbook
Certificate deployment
In a modern world, you have certificates for authentication. This may be either device- or user-certificates. The most common approaches are:
- SCEPman - a cloud certificate authority (my recommendation, in especially greenfield situations)
- Active Directory Certificate Services with NDES & SCEP
Comparison
| SCEPman | NDES & SCEP | |
|---|---|---|
| Infrastructure | Azure resources only (may generate costs) | Public key infrastructure, NDES server with webserver and proxy |
| Use case | Cloud only environment that mostly holds AAD joined endpoints, rather no local resources | On-premises domain based environment + AAD joined endpoints |
| Operation | Service updates of SCEPman | OS patches, service updates on the servers |
| Costs | This is a third-party solution that generates license costs | Run & maintain local servers |
Profile management
Targeting & assignment
General facts
- There are many different profile types, from configuration, compliance, security, proactive remediation, updating rings to apps
- Targeting can be made to device or user groups - but there are generally no user or computer configurations like in GPO's
- Inclusion and exclusion groups can be assigned / group nesting is possible
- Filter are tenant wide evaluations to target a limited set of devices
- There is no native integration for development, integration or production profiles
- Scope tags and Mutli Admin Approval (described above) bring a layer of governance to Intune profiles
My recommendation
- Keep it as simple as possible!
- Define a naming convention and adhere. (e.g.: DeviceOwnership-Profiletype-Name-State - COPE-ES-Antivirus-Prod | COSU-DCP-Kisokdefault-Dev)
- Leverage Azure AD dynamic groups to populate groups, especially from imported Autopilot identities, e.g. GroupTag - Official docs
- Mostly, i prefer device groups to distinguish different device workloads for any sort of profile or policy. For some more specific assignments that is dependent on the user, you may go for user groups. Also for these profiles, user profiles may be more applicable: Windows Update rings, apps, compliance policies
- Define a set of base configurations and apps that are mandatory and applied to all devices/users
- Serve apps as available to promote the self-service company portal experience
- Make excluded groups distinctly. Name them equally to the config profile to retrace exclusions more easily.
- Name all profiles that are not used productively special and implement a cleanup process to delete unused profiles.
Assignment strategy
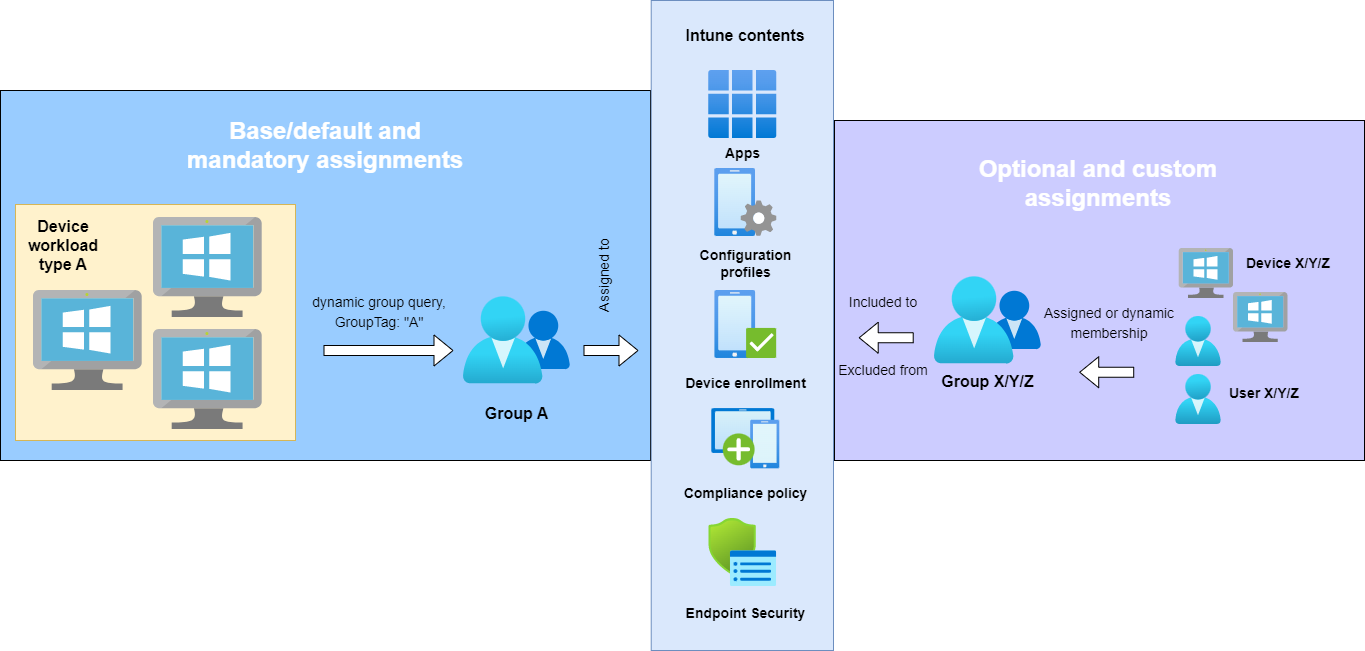
Compliance
Intune compliance policies ensure that endpoints meet organizational requirements. They should be used that way and ultimately block access for non-compliant devices - this can be achieved through Conditional Access. Regular compliance policies include Device Health, Properties, Security, Defender for Endpoint machine risk score. The more technical standards you can ensure on your devices, the more stable and secure they will be. Custom compliance with your discovery script and custom compliance settings allow for any configuration check you want.
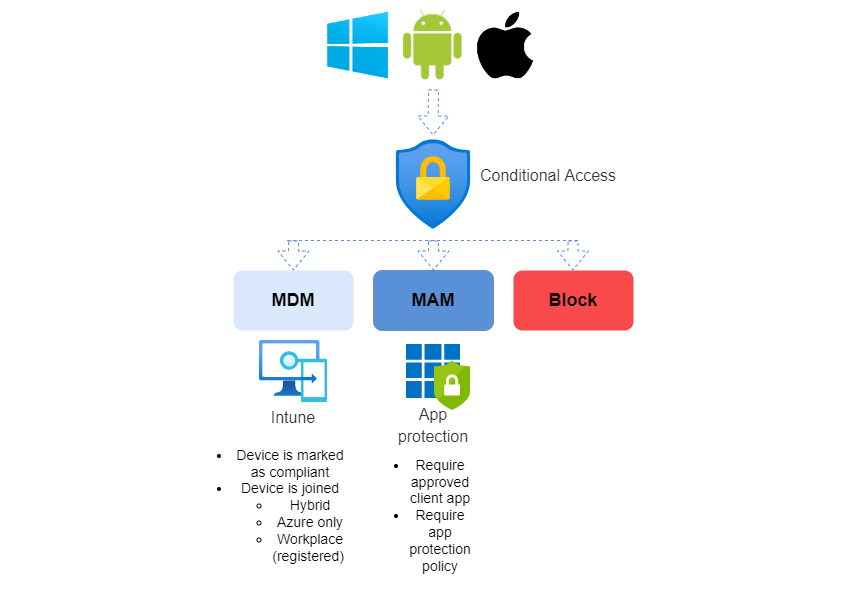
Conditional Access: platforms
Now to get all of your OS platforms under control, you may leverage Conditional Access. Understanding MDM & MAM is essential, and do not forget about browser access (Read about session controls). In the graphics below, you see the Conditional Access control set with the platforms and the settings to enforce. In the end it is all about a monitored and secure access to your data.


Some topics contain advisory from an exchange with Albin Klinaku - thanks!

