Intune change tracking (Azure Workbook)
What is it?
Intune offers a variety of configurations and functionalities, namely talking about configuration profiles, applications, scripts and also operational tasks like managing a device. (enroll, sync, delete etc.)
It can be quite a challenge to keep track of all the changes and operations, and the audit logs don't show the big picture on what is happening in Intune.
This is why I created Intune change tracking (current version: V2) - as an Azure Workbook to:
- Richer analyzation of Intune Audit logs by providing filters and search options
- Find Intune events at a single pane of glass
- Grouping of information types so that you can find the relevant information faster
- Understand how you run your Intune service find details on actions
Related sources
GitHub file to Workbook source code
Intune change tracking
The Intune change tracking Workbook has 4 sections:
- Overview - General Audit event information & visualizations
- Search profile types - Audit events for specific Intune profile types and contents
- Device Identity - Audit event information to device to tenant assignment
- Device opeartions - Intune administrative tasks Audit event information
![]()
Overview
The Overview shows most important log information of your Intune environment.
- Intune Audit event types, An overview of different Audit event types, filtered by custom time range.
- Intune method, An overview of the most common Audit event methods, filtered by custom time range.
- Recent Audit events, A table of all Audit events, based on the selected time range.
- Intune Audit event count, A count of Audit events over a fixed time.
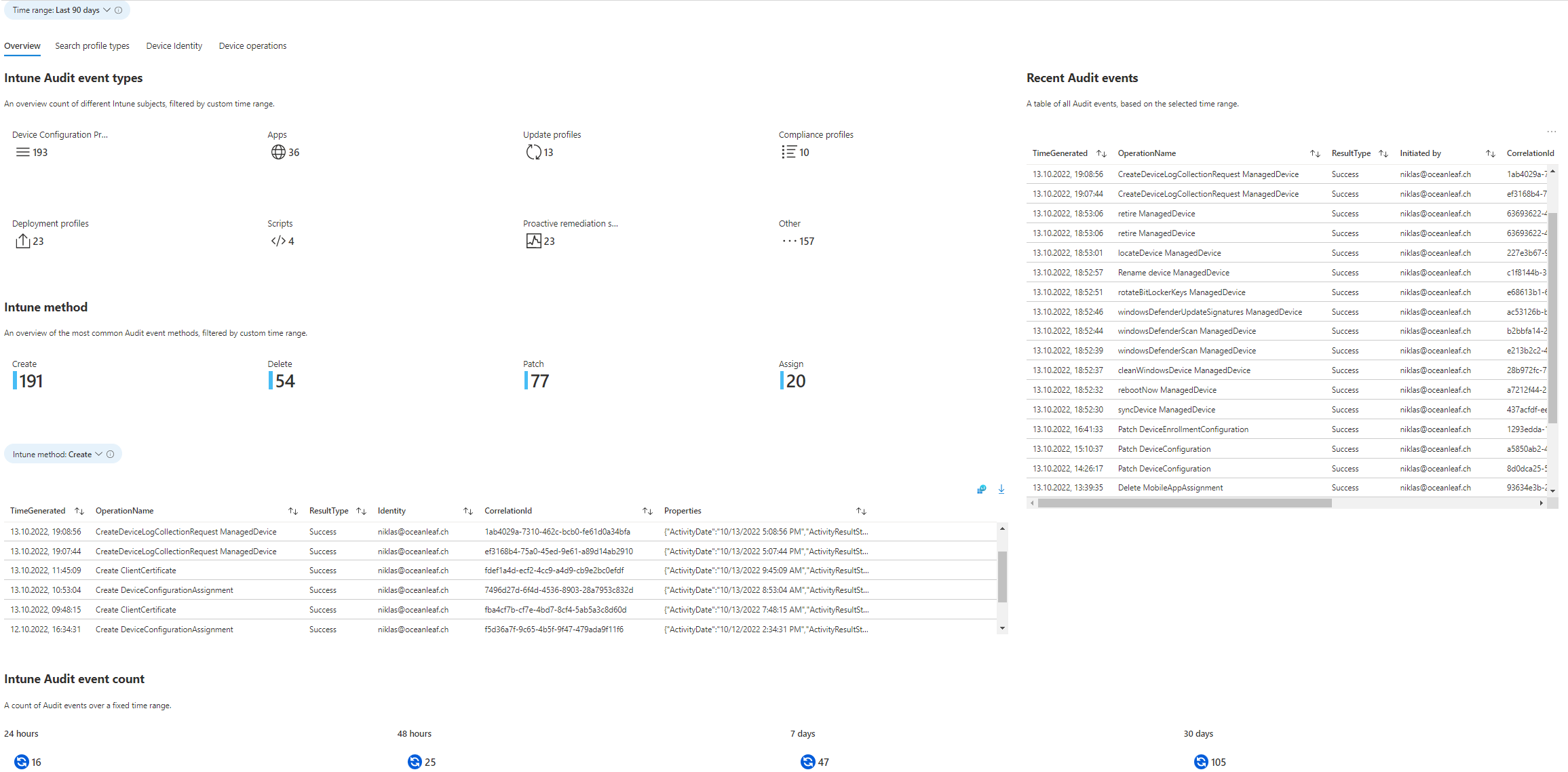
Overview
Search profile types
To further investigate the profile type events, consolidate this section, which provides a lot of different information, always filtered by a profile type.
- Profile type Audit events, Table output of custom profile type audit events.
- Search the Audit event by Correlation ID, Copy the correlationID from the query above to explore the event.
- Value changes, Find the changed Settings Name and compare old with the new values.
- Changes over time, This is a visualization of custom profile type changes, summarized per day.
- Top 10 modified profiles, Find the top modified profiles by profile type.
- Search events for profiles by a specific term, Please specify a term/name in the parameter below to search the Profile Names.
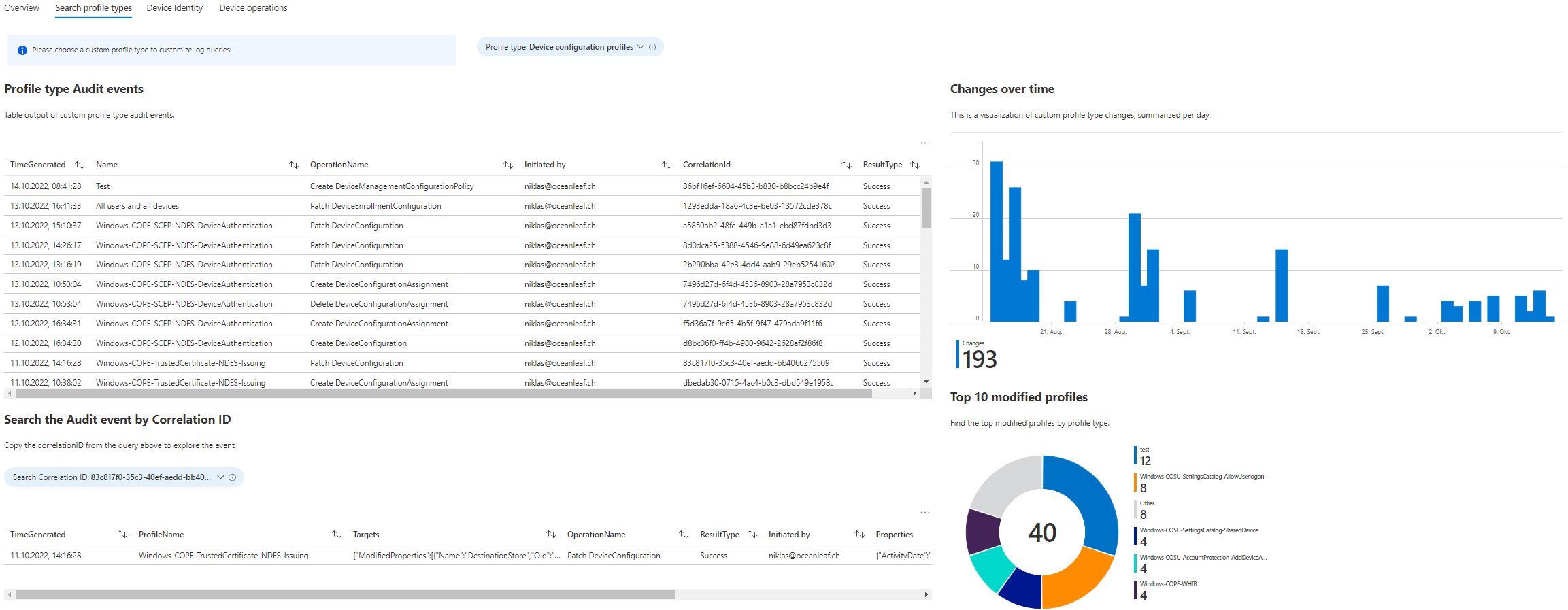
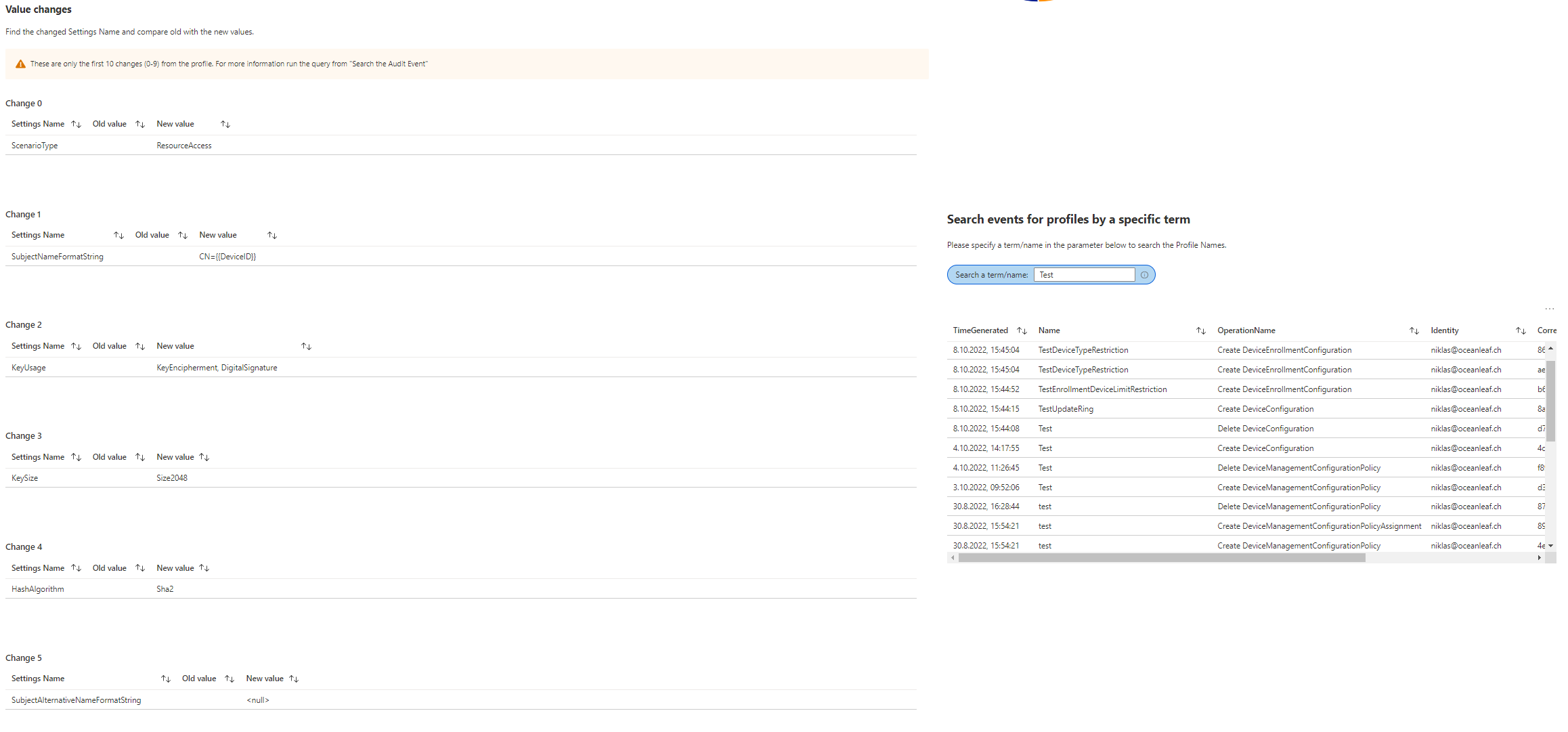
Search profile types
Device Identity
The Device Identity is intended to conduct Autopilot device hardware hash event logs.
- Device to tenant assignment, View stats for Autopilot device identity/hardware hash assignment to your tenant.
- Find Device Identity events, Search Device Identity events by action.
- Authenticated Identities, Pie chart about the used identities to register a hardware hash.
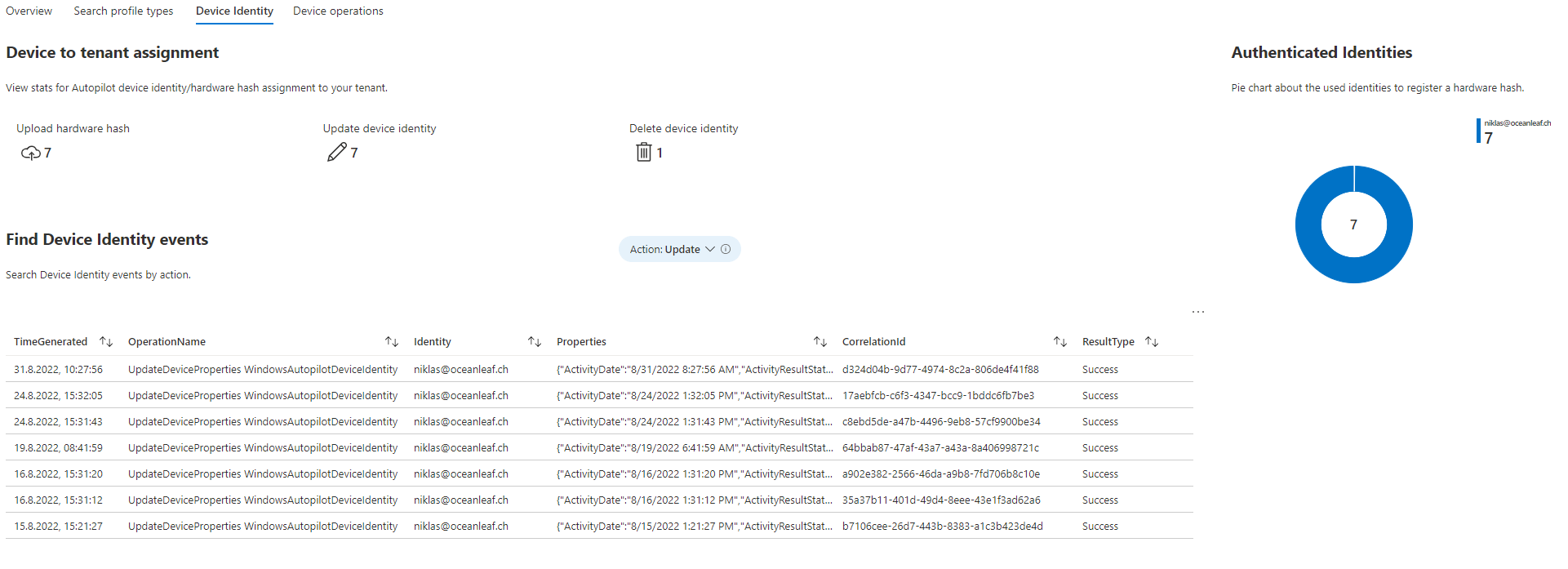
Device Identity
Device operations
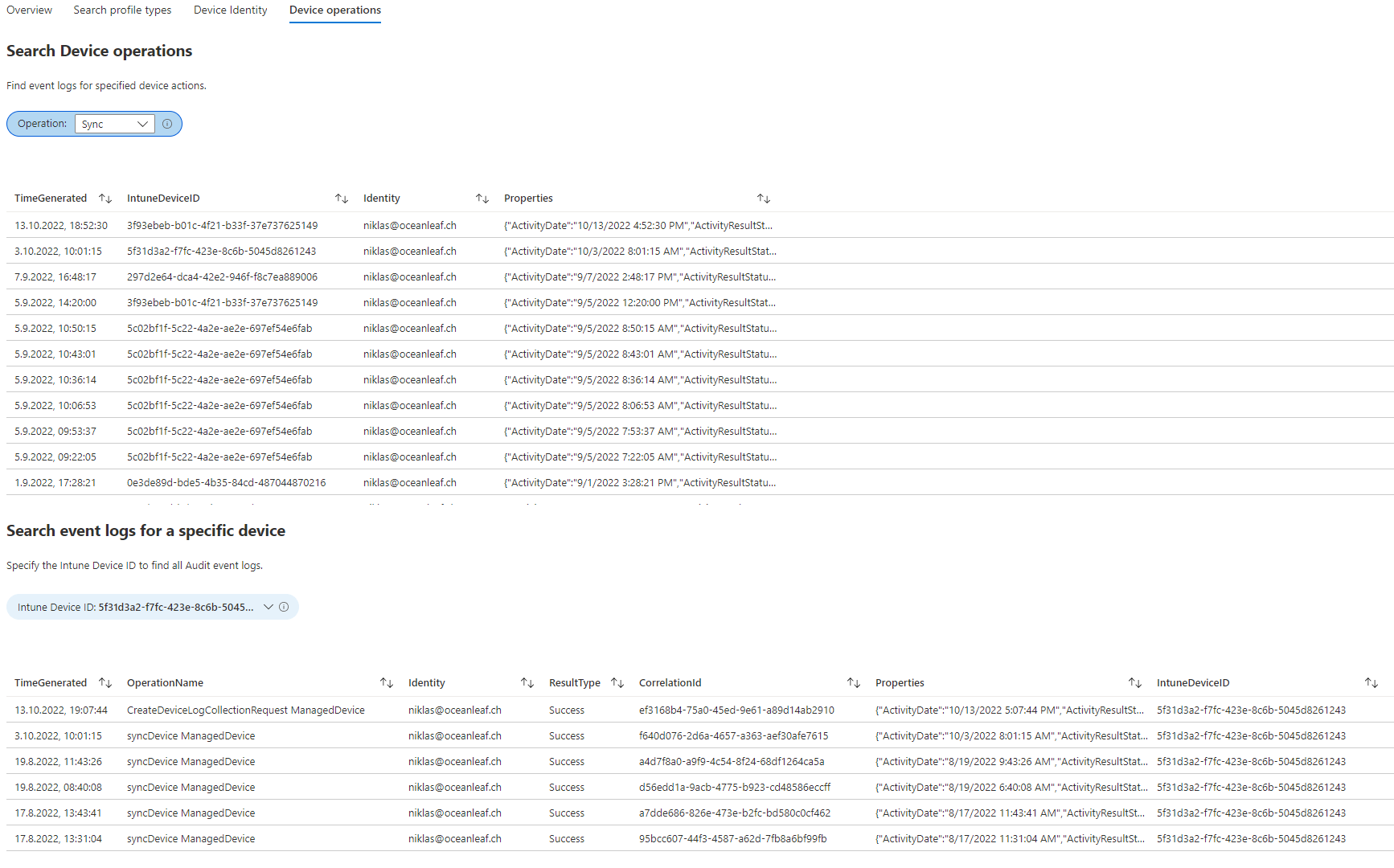
The Device operations allow to search Intune actions performed by Intune administrator roles.
- Search Device operations, Find event logs for specified device actions.
- Search event logs for a specific device, Specify the Intune Device ID to find all Audit event logs.
Device operations
Development and community edition
Intune change tracking is a free and open source Workbook by me, for the community. If you have any feedback or inputs to extend the feature set of it, please feel free to contact me or start a pull request on GitHub.




