Intune - a reference to Kiosk/shared PC mode
Introduction
Windows is an open platform that allows users to install applications, customize settings and work on files of several different types. At the same time there are some use cases where a limited or restricted app or Windows platform environment is needed. These are called single-use, Kiosk or shared device scenarios and in this post we are going to take a look at both of these solutions.
Use cases
- Self-service devices or public terminals/kiosk
- Digital signage
- Education or industry specific
Benefits
- Easy management - dedicated or independent workloads/apps can be provided easily without the circumstances of providing a device, access, credentials
- Maintenance free - non-persistent or session-based experience
- High-reliability - dedicated to one single use
Windows Kiosk mode
Windows kiosk mode serves an experience that is limited to apps and is completely independent of any user affinity.
Windows shared PC mode
Whereas shared PC mode lets you utilize the whole Windows platform, but is thought for shared-/mutli-user devices.
Solution comparison
| Kiosk | shared PC mode | |
|---|---|---|
| General | Built-in feature that restricts the Windows experience to single- or multi-app (Windows 11 currently only supports single-app) | Windows will have no direct user assignment/affinity and usually non-persistent sessions |
| Technology designs | Single-app: public browsing sessions (intended for users to access the web), Digital/Interactive Signage (InPrivate fullscreen display of site) | Guest account will be used, that is newly created on each sign-in |
| Use cases | Corporate owned single use (COSU), that requires a fully locked down and app-limited experience (perfect for dedicated Kiosk scenarios or digital signage) | Provide a corporate or non-corporate non-persistent Windows platform |
| Limitations | Only apps can be used, the Windows platform is not directly accessible + Windows 11 only supports single-app kiosk | Full Windows experience |
| Account model (sign-in) | Autologon, Local user account, Azure AD user or group | Guest and/or Domain |
| Enrollment & join type | Intune Endpoint Management + Azure AD join, User-driven with a generic account or Self-deploy does not require any credentials | same like Kiosk |
| Device security | Already restricted environment, Security Baselines + Defender for Endpoint can be applied (some breakout methods) | Security Baselines + Defender for Endpoint can be applied, depends on how much the environment should be restricted |
| Applications | Applications must be installed, available is: Browser, Store App, Win32 or AUMID | Applications can be installed through various sources (user session profile only or for all users) |
| Windows Update | Use Windows Update for Business and put it in a fast or production ring | same like Kiosk |
More information / hints from the field
Enrollment in Intune
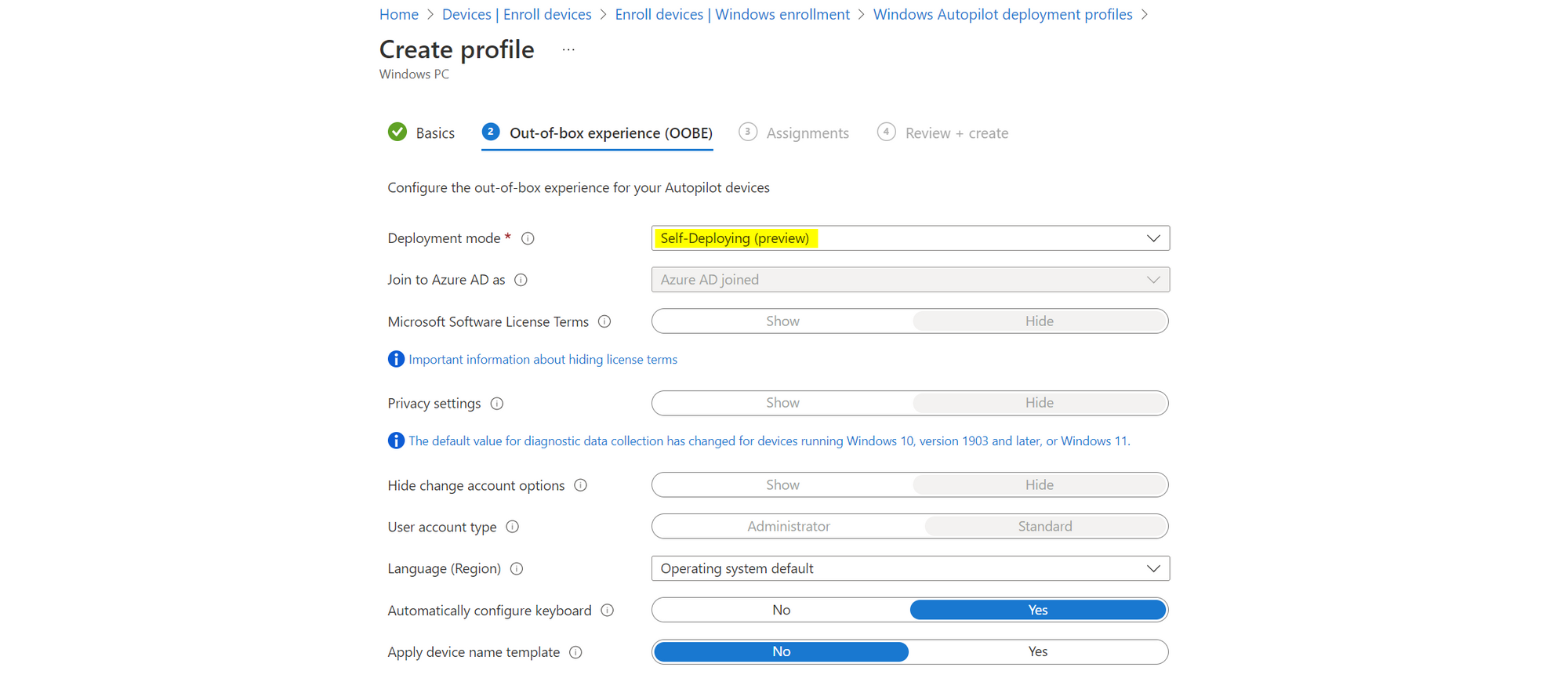
Create a new deployment profile and switch it to Self-Deyploing (Preview). Once a device gets assigned to this profile, it will directly start with the provisioning process and show the enrollment status page (ESP). The only thing to set up a device is internet connection, credentials are not required.
Configuration profiles
Lets take a look into the Intune device configuration profiles for Kiosk and shared PC. I just want to give an overview of all available settings, but not explain every single option. Here you can find all Kiosk settings and here are all shared PC mode settings.
Kiosk - templates
Kiosk experience can be configured from a template only at this time.
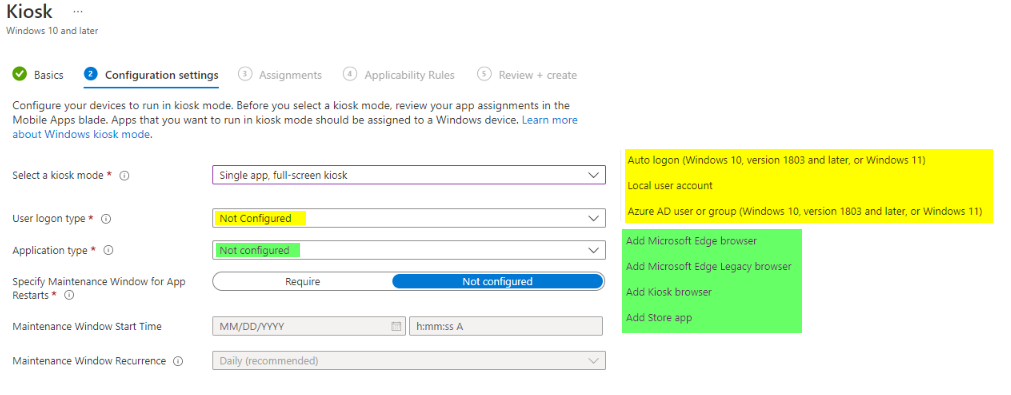
Single-app
Choose a logon type and select one application type. Since it is only one app in single-app mode, you can only specify one type.
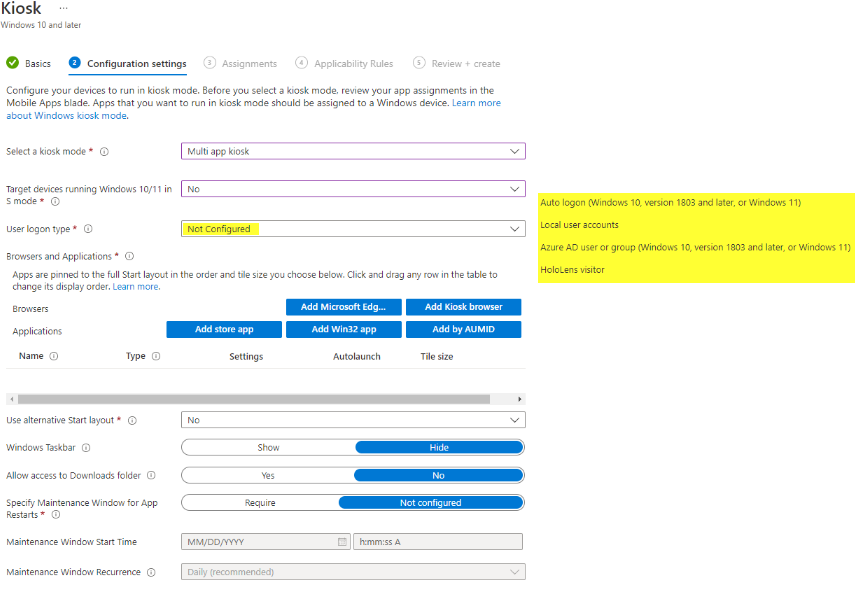
Multi-app
Similar to single-app, choose a logon type. But for multi-app you can add multiple application types (Microsoft Edge, Kiosk Browser, Store App, Win32, AUMID).
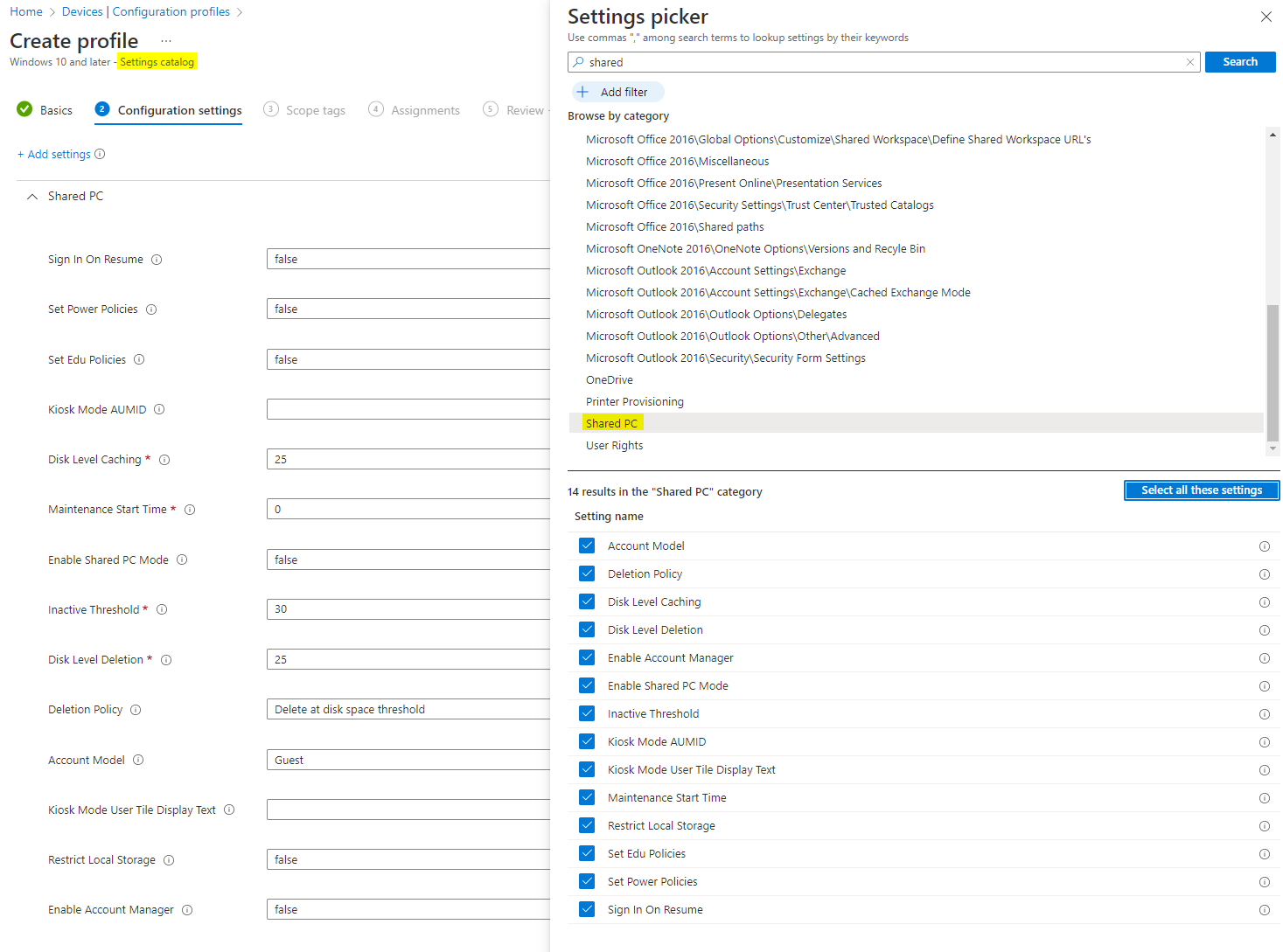
Shared PC - Settings catalog
For shared PC mode settings, I would recommed to choose the settings catalog and search for shared PC.
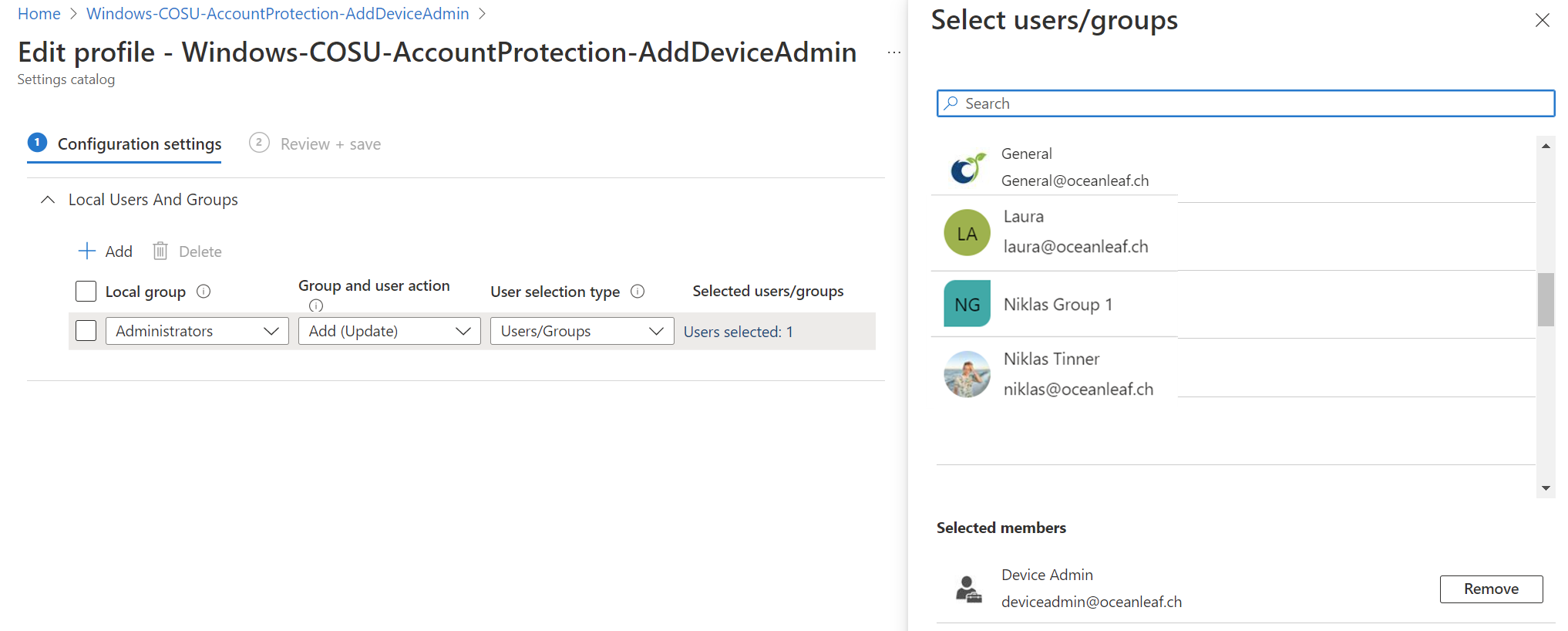
Local administrator
By default all local users are disabled for COSU. Although it is possible to modify the local group memberships on the devices through an account protection policy. There we can add AzureAD, domain or local users and groups.
Applications
Overview
Applications behave the following way for the two different options:
- Kiosk - limited to specified applications, no Windows platform installations
- Single-app:
- One single app only Browser or Store app
- In case of Browser usually SaaS apps are used
- Multi-app:
- Browser, Store App, Win32, or AUMID
- Single-app:
- Shared PC mode - apps can be installed on the Windows platform and are (non-) persistent
Deployment
In these scenarios we can use the following app deployment methods:
-
Computer-based installation
- Intune
- Apps that should be installed for all users does need local administrator rights, these installations are persistent
-
User-based installation (only applicable for shared PC mode) are apps that only install to the user directory, these will get removed once a guest user will sign-in again
- Apps from the Microsoft Store
- Apps that only install for a single user can be installed by a common user
Find the AUMID easily
You can find the AUMID of a application or if you need the AUMID of an .exe file that needs to be whitelisted with the following steps:
- Pin the application to the start menu
- Then through Powershell: Export-StartLayout -Path "Path\filename.xml" -UseDesktopApplicationID
- You will get the AUMID in the .xml file. Very handy if you have complex multi-app kiosks.
This is the way how Microsoft would do it.
Windows and Office activation
As there is generally no user license availible that directly activates Windows or Office online, we should utilize some tricks to stay compliant.
Office can be configured with the Office customization tool. Include a volume license/MAK key and export it. You will then get a .xml file that can be packaged and uploaded to Intune.
The Windows OS can be easily activated through a little powershell script with a multiple activation key (MAK).
slmgr.vbs /ipk XXXXX-XXXXX-XXXXX-XXXX-XXXXX
slmgr.vbs /ato

