Local admin/privilege management with Intune
Introduction
Most operating system know two levels of user interactions. Standard or elevated, also known as administrator. For Windows in the enterprise segment, the users most often work with standard permissions. The IT has access to administrator accounts that can modify the system, install applications, make manipulations and changes to the whole system. The technical control on Windows is found in the "Local users and groups management" console - here we can find a dedicated Administrators group,members are granted full admin permissions.
Organizations that manage their devices with mobile device management frequently manage the local administrator privileges under the subject of account protection. It is a recommendation of the Microsoft Security Configuration Framework to keep systems secure.
Security notes
From the security perspective this is a huge topic, because adversaries have full access on the OS once they obtain local administrator permissions.
Additionally you absolutly want to prevent the usage of local administrator accounts that have the same credentials for multiple devices. This represents a massive vulnerability for all of you systems to get compromised. Access to one account with such permissions means access to all of your devices, called lateral-traversal attacks.
Approaches
For the management and control of local administrators you can follow one or more of these common approaches:
- Azure AD roles - assigned user roles that are local admin on all AAD joined devices
- Intune account protection policy - Intune endpoint security policy that configures local group memeberships to targeted and assigned groups
- Endpoint Privilege Management (EPM) - Run defined programs with elevated permissions, controlled through Intune policies
- Windows LAPS - the new Local Admin Password Solution (LAPS) that supports Azure AD only joined devices
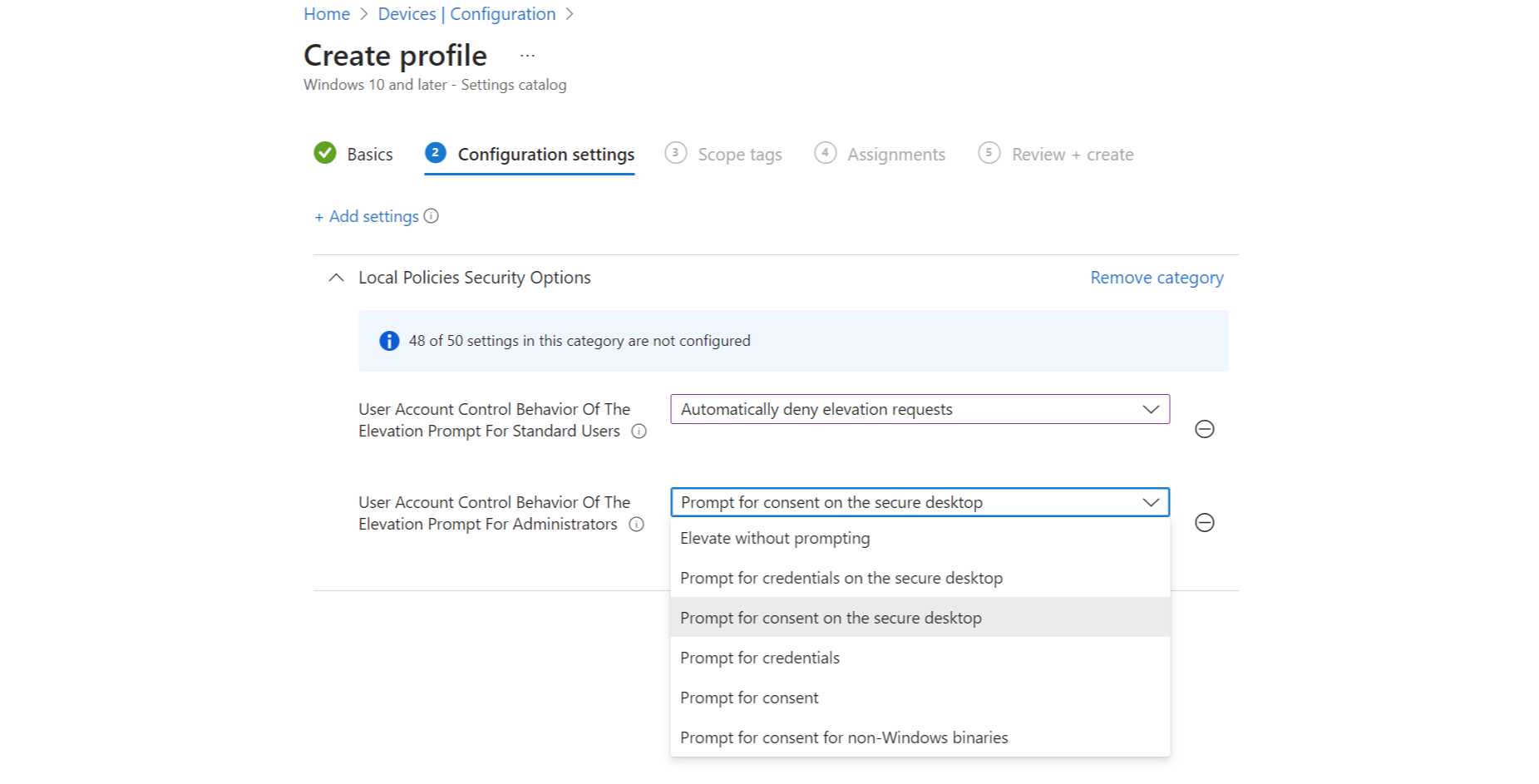
Default behavior policy
The Microsoft Security Configuration Framework (Level 1) states the following security baseline configurations:
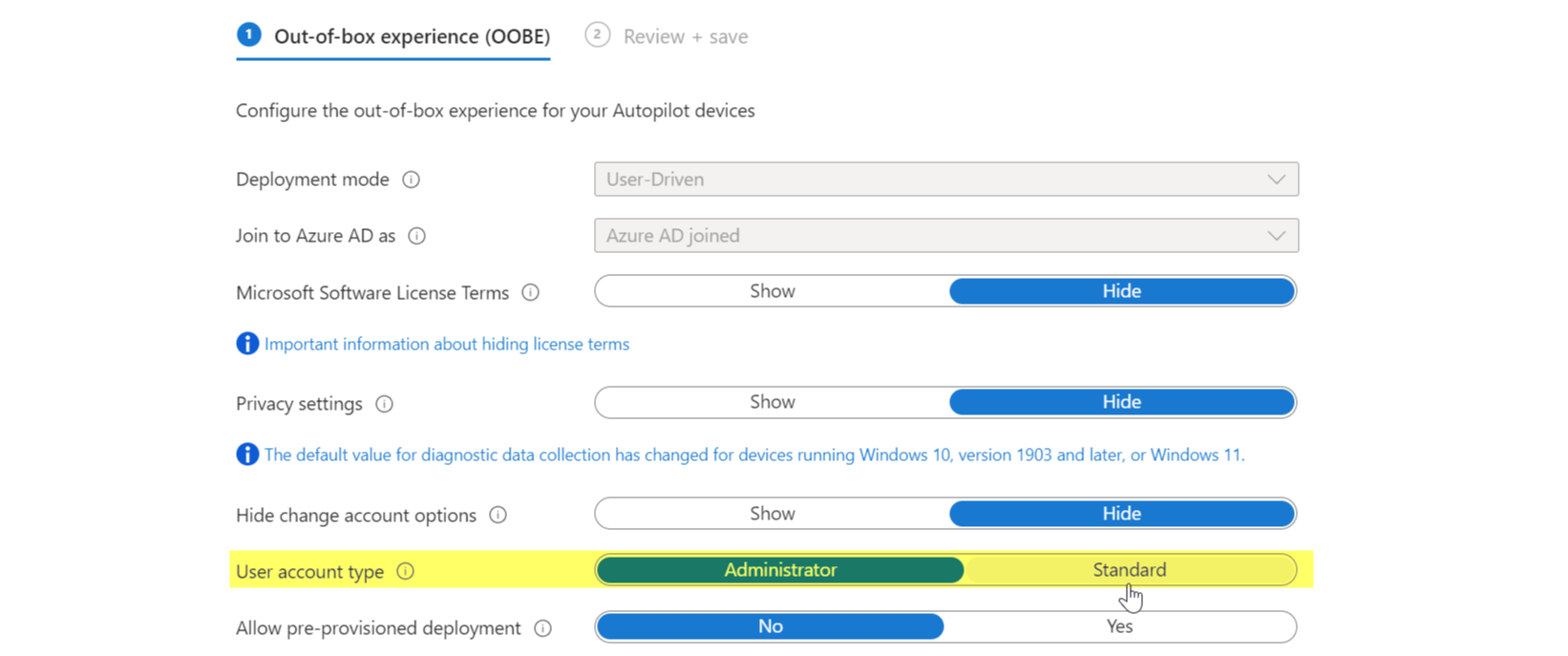
Autopilot deployment profile
There is also an option related to this in an Autopilot deployment profile. Specify whether users are administrators or standard users on the device.
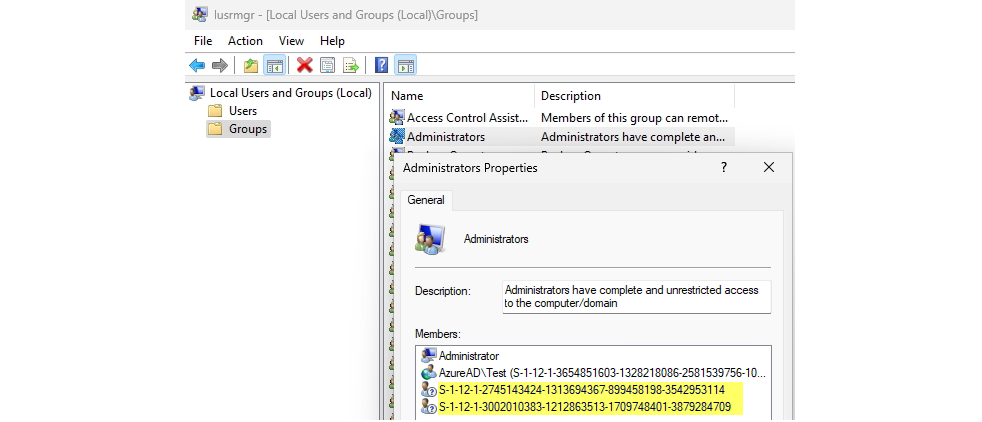
Azure AD roles
Users assigned with one of these two roles are member of the local administrator group on every Azure AD joined device from the tenant.
On the Windows client side we can see this in the local users and groups managment:
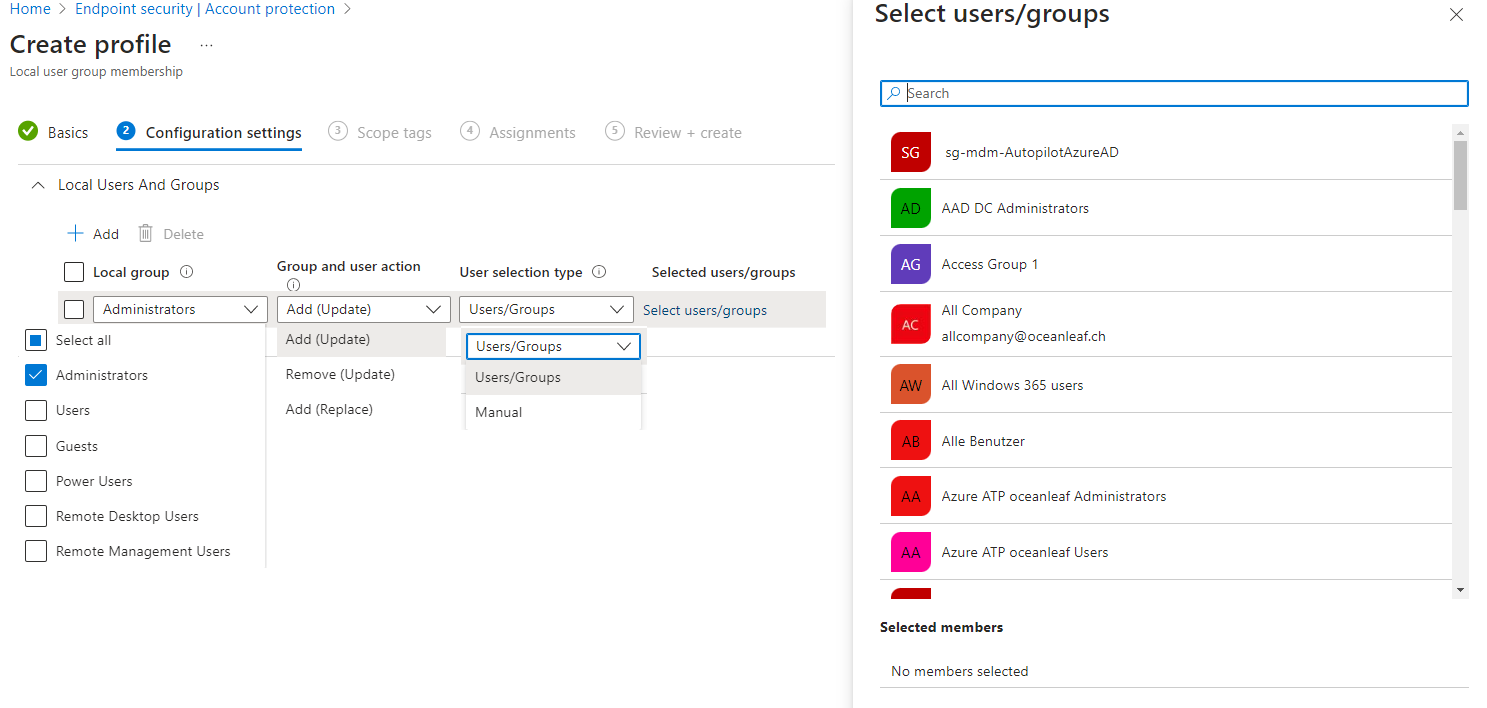
Intune account protection policy
Under Endpoint security>Account protection you can create a Local user group membership policy. This is a suitable option to update, remove or replace on of the known local groups (Administrators, Users, Guests and so on) with Azure AD users and groups. A "manual" update is also supported for Username or security identifiers (SID), instead of AAD identities.
Endpoint Privilege Management
Disclaimer At the time this blog post was written (April 2023), Endpoint Privilege Management (EPM) is part of the Intune Suite license and in public preview. My colleague Fabrizio published a good post on it.
Functionality
With EPM policies in Intune, elevation policies and rules can include a set of attributes that are tied to an application or file that can be elevated for default users. There is an integrated justification process.
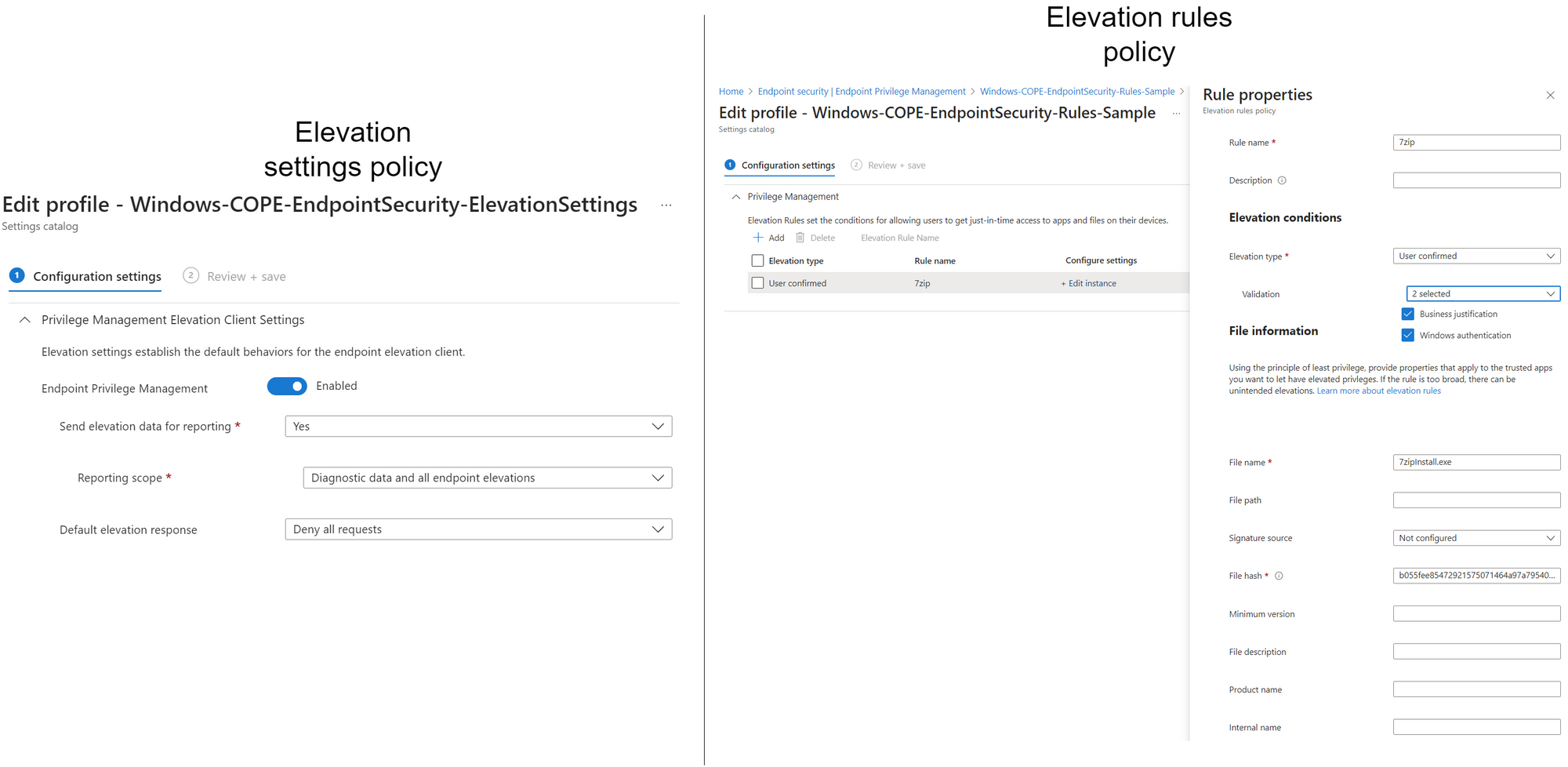
Use cases
For the moment I see EPM only applicable for a few special use cases. It is particularly recommended in my opinion for elevating apps that are static and always the same.
Limitations and what's missing
- Only works on Azure AD and Hybrid Azure AD joined devices (Windows Server must be hybrid joined)
- No on demand approval for elevation
- Not supported on any VDI infrastructure
- SSL-inspection is not supported to the URL "dm.microsoft.com" which is used for EPM
- Unknown Internet or network files fail or require time before the elevation works
- Reporting does not work (in my and a few other environment)
- Company Portal could break after EPM deployment (Read more by Rudy Ooms)
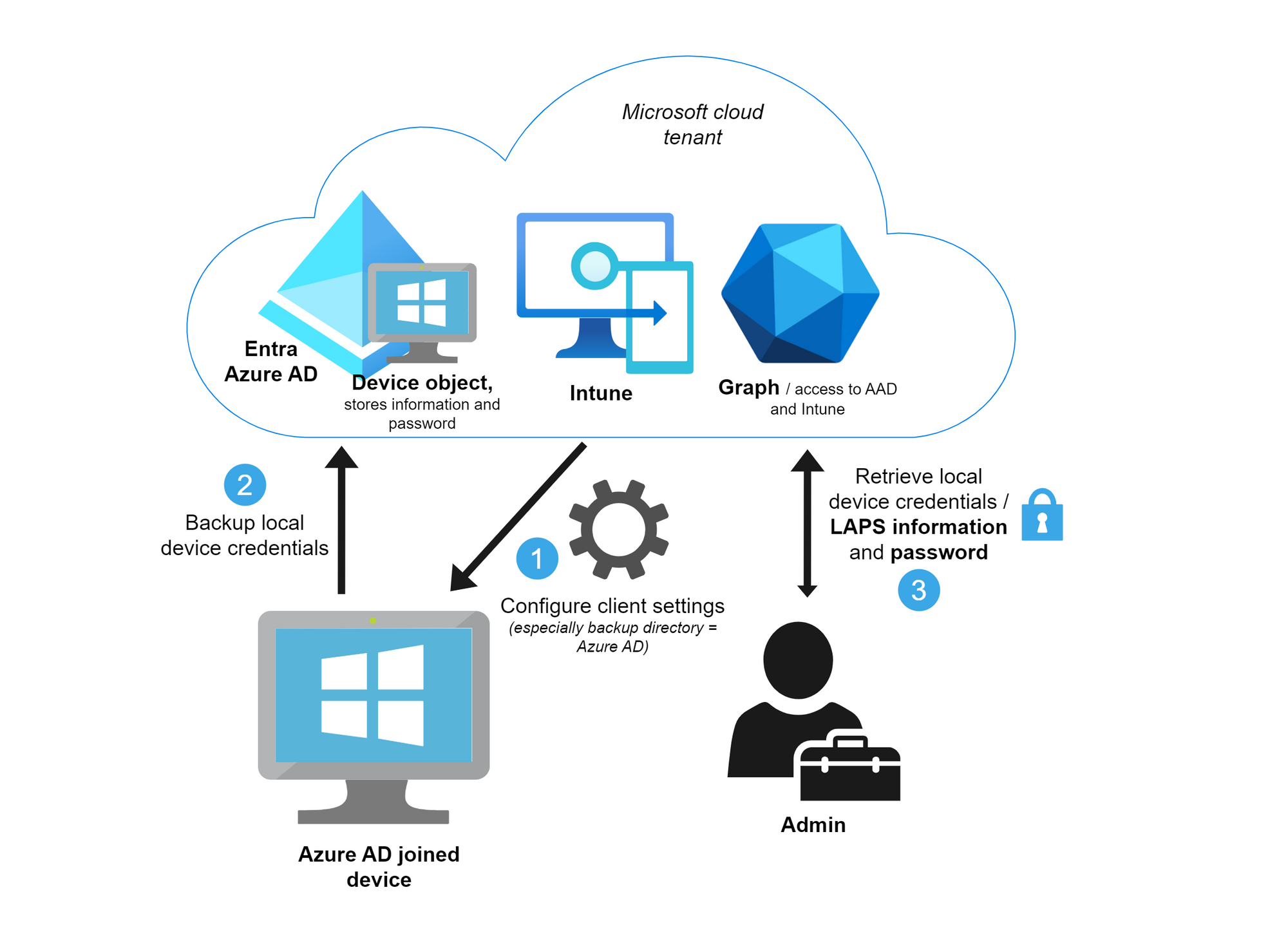
Windows LAPS
Windows local administrator password solution is the successor of legacy LAPS. It now also supports Azure AD only joined devices. The device local credentials (of the admin account) is stored on the Azure AD device object (alternatively also to the on-premises AD device object). An admin with the right roles/permissions can read the credentials through Graph API.
The big advantage of LAPS is that every device has a dedicated local administrator account, which regularly rotates the password. This eliminates lateral-traversal attacks and secures the workflow for support actions where elevated privileges are required.