Key takeaways from the Microsoft Digital Defense Report 2024
Introduction
Every year Microsoft releases their Digital Defense Report which provides a comprehensive summary of global developments in information technology security over the past year. It includes both high-level management insights and detailed technical analysis based on data collected from Microsoft and third-party intelligence services. This post is your TL;DR 😉
1. Social factors 👥
The report covers technical initiatives, but it’s also important to understand the bigger picture of cybersecurity. This includes social factors like global crises and conflicts between nations, each following their own interests. (also including USA and companies like Microsoft) Adversaries continue to evolve, exploiting security measures and leveraging the latest technology and psychological tactics to harm victims, primarily for financial gain.
2. Emerging threats 📈
Like in the past, threats continue to rise on the horizon, both in complexity and volume. These are increasingly prominent and present new challenges:
- Traditional
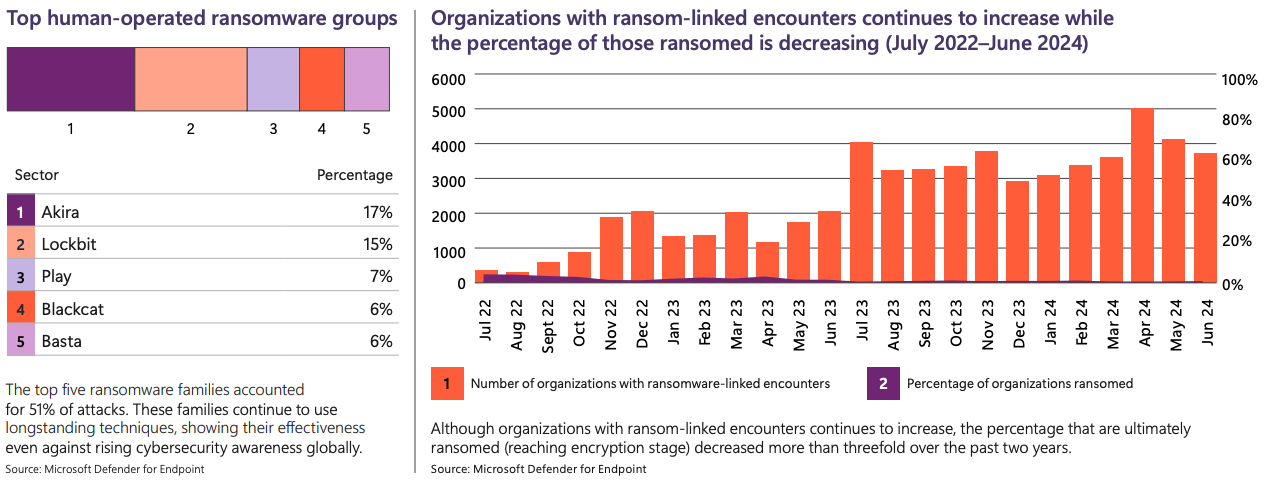
- Ransomware - Malicious software that encrypts a victim's data or locks them out of their systems, with attackers demanding a ransom payment in exchange for restoring access
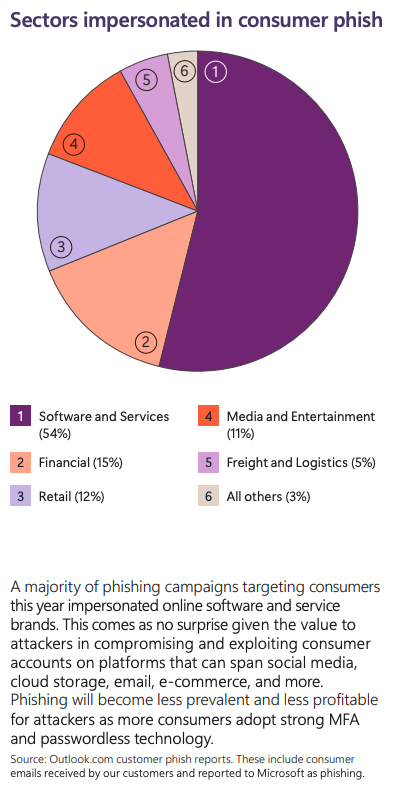
- Phishing - Tricks to fool people into giving up information, aka social engineering
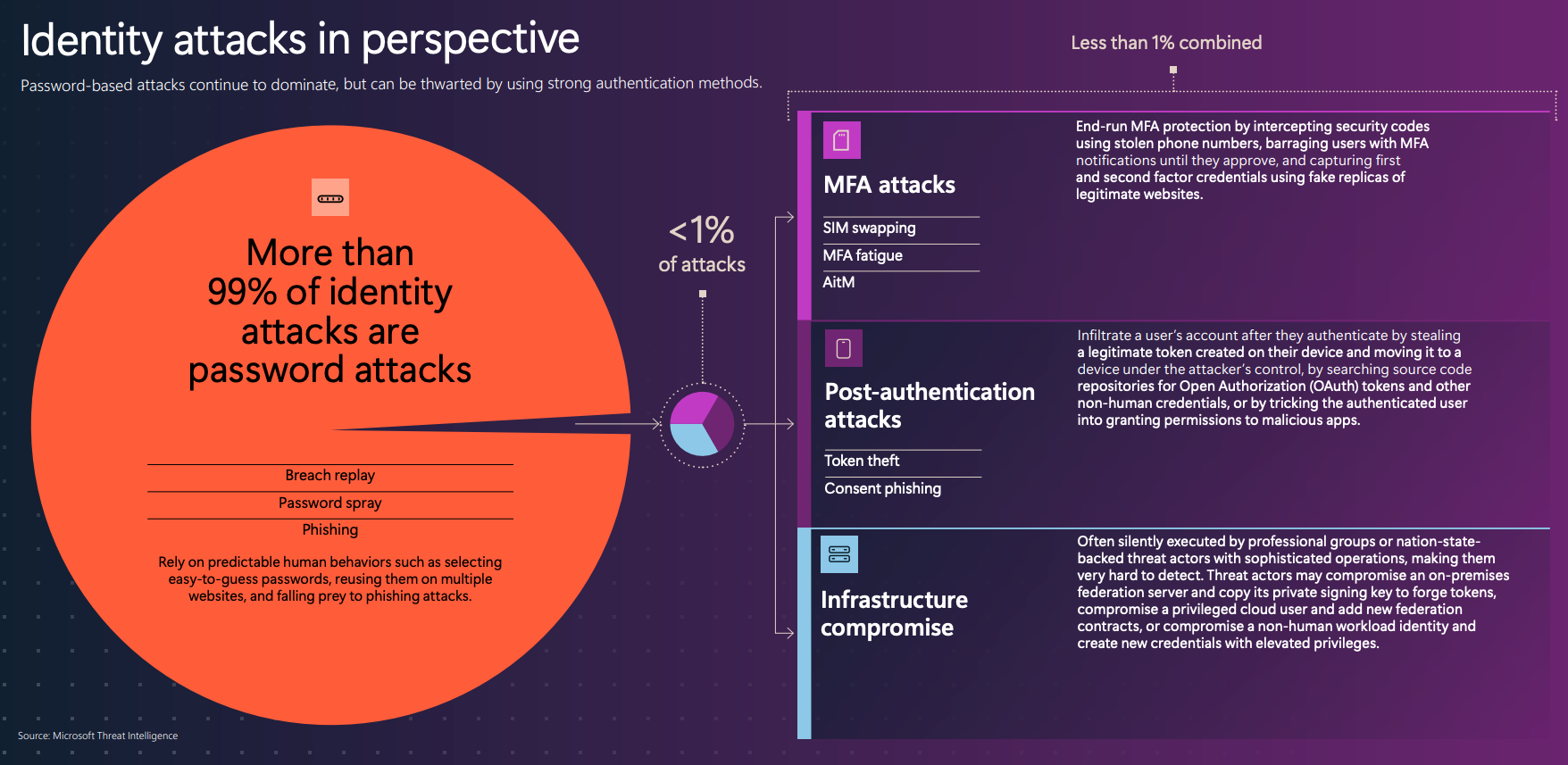
- Identity-based attacks - Exploit stolen or compromised or harvesting user credentials to gain unauthorized access to systems, networks, or sensitive data
- Emerging
- AI-driven attacks - Attackers leverage artificial intelligence to improve their tactics: faster and broader reconnaissance, data processing, anomaly detection and abuse, or automation capabilities
- Supply chain vulnerabilities - Abuse weaknesses in the networks of suppliers, vendors, or third-party service providers to impact major organizations or institutions
- Deepfake technology - Uses artificial intelligence to create highly realistic but fabricated audio, video, or images of individuals, used to impersonate people for fraud, disinformation, or other deceptive purposes
3. Cybercrime and Threat actors 🚨
Cybercrime is increasing too, especially with more ransomware and financial fraud. Criminals are improving their ability to bypass security systems and steal data or cause harm.
Threat actors (nation-state)
Nation-state actors are becoming more prevalent, and Microsoft observes hundreds of criminal groups motivated by geopolitical objectives, targeting critical or valuable infrastructure of other nations or interfering elections. Noteworthy are the war in Ukraine and Russia as well as the Israel-Hamas conflict.
Increasing attacks during hybrid warfare on operational technology have been observed on internet-exposed, poorly secured OT devices that control real-world critical processes.
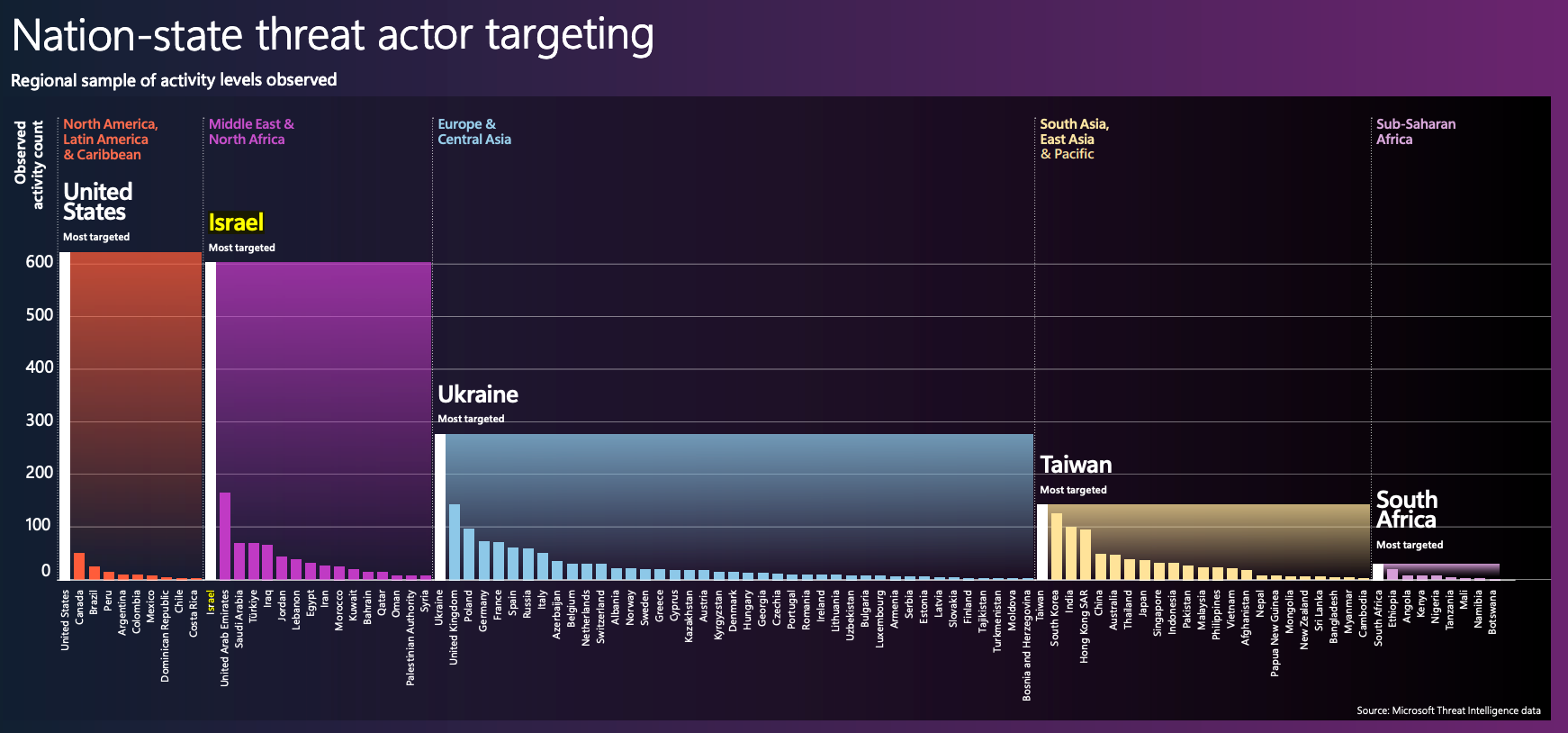
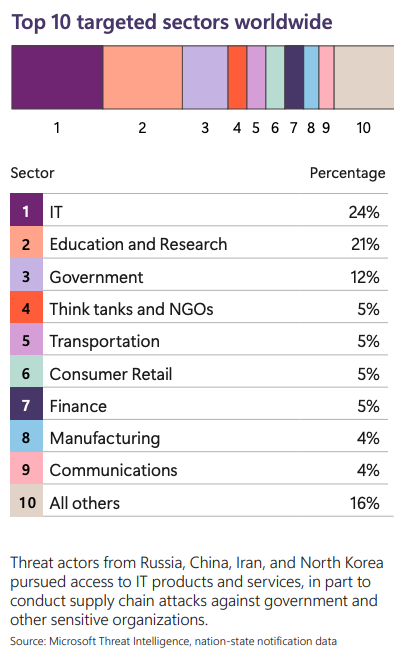
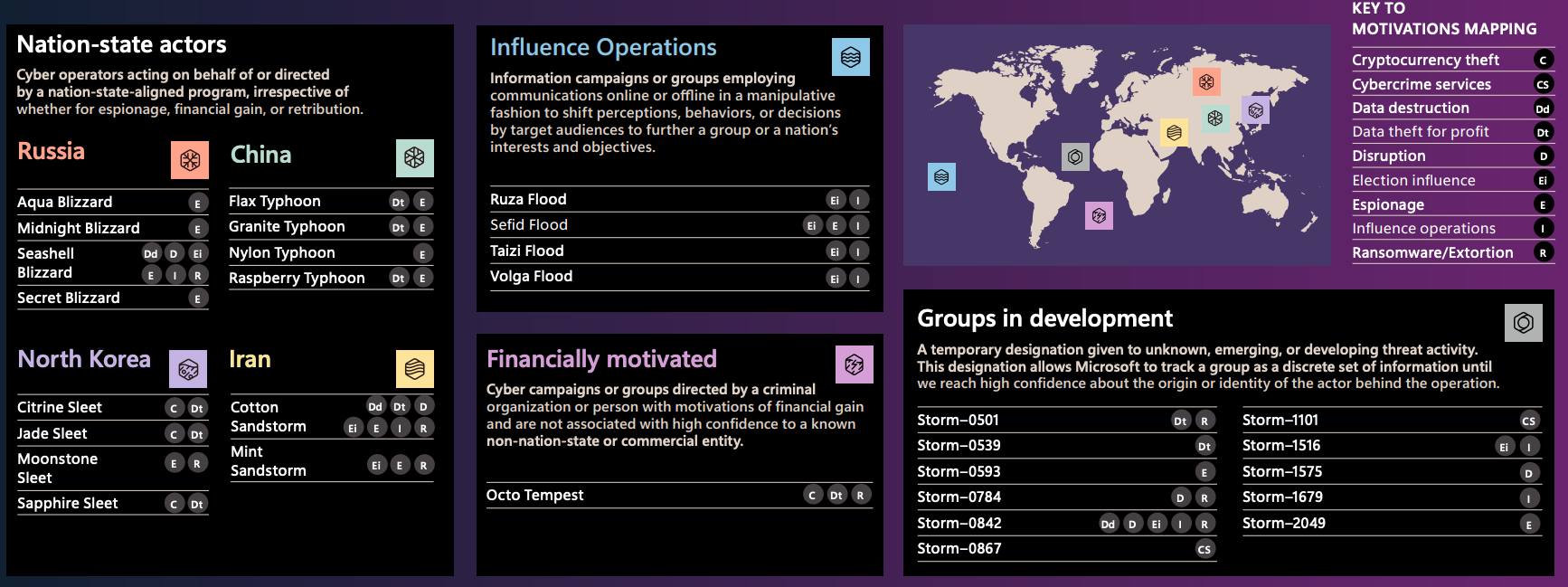
The report also holds various "Cyber Point of Views" that features different countries on their viewpoint and initiatives towards cybersecurity.
4. Microsoft's unique vantage point 🧠
- 78 trillion security signals are processed daily by Microsoft from various sources, including endpoints, cloud infrastructure and other services (in comparison with 2023: 65 trillion signals daily)
- Microsoft tracks over 1,500 unique threat groups, including more than 600 nation-state groups and 300 cybercrime groups
- 34,000 full-time security engineers work on cybersecurity projects within Microsoft
- Microsoft partners with 15,000 organizations specializing in security
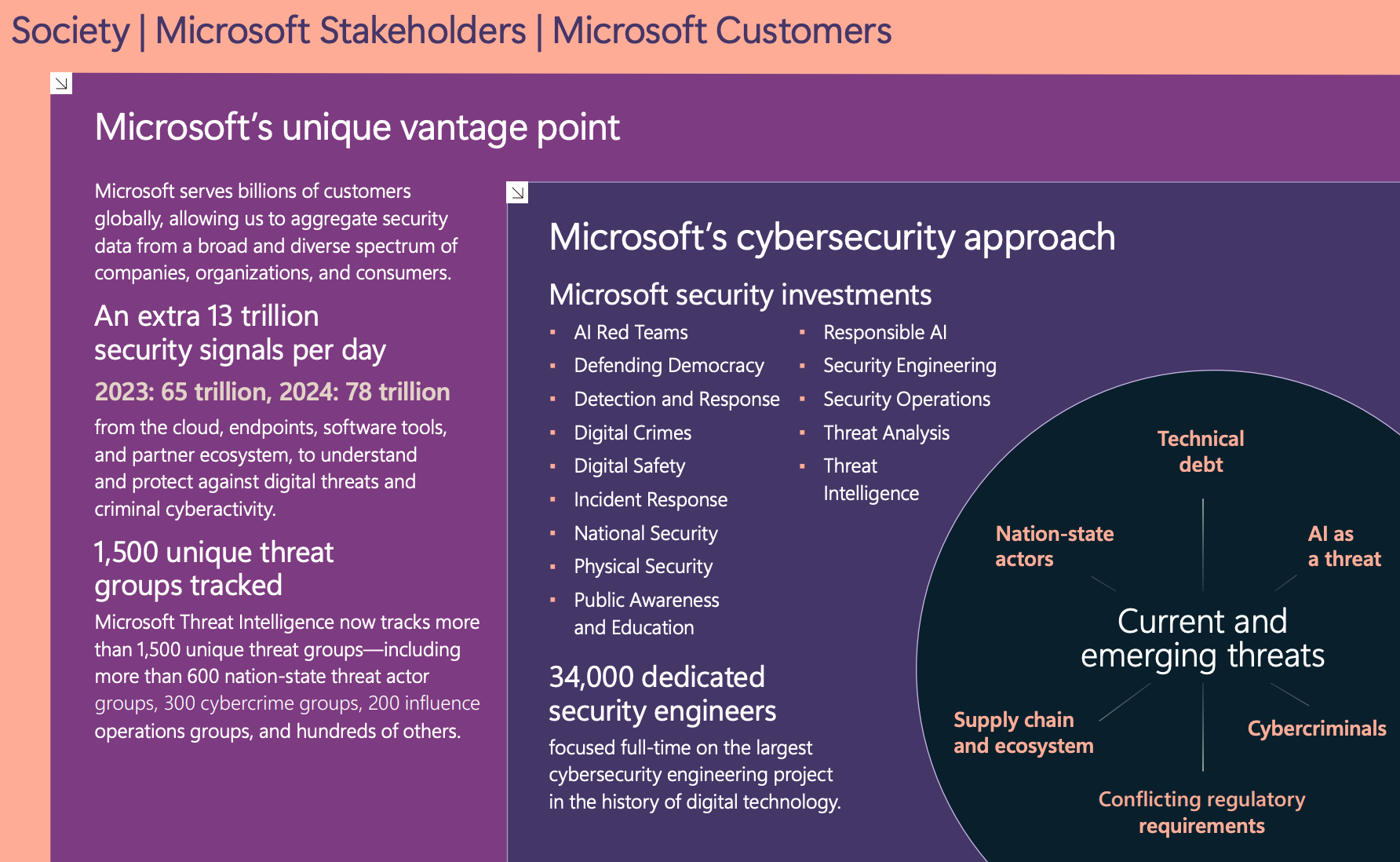
Furthermore, the Secure Future Initiative (SFI) focuses on making security a top corporate priority, strengthening defenses across Microsofts infrastructure.
5. AI’s impact on cybersecurity 💡
Artificial intelligence has a major influence on all aspects of cybersecurity. Microsoft highlights their Security Copilot, but on a broader scale, the following key aspects are also mentioned in relation to AI:
- AI-enabled human targeting threats will be more difficult to detect and defend against - even with AI tools
- Emerging techniques for both red and blue teams are on the horizon, nation-state threat actors are using AI for influence operations (manipulation of content)
- Implementing security in AI is pursued in different approaches for governments and industries
- Law and international law are no longer sufficient in the modern era, especially with foreign influence operations - therefore the United States, the EU and other legislative initiatives are driven
6. Attack methods 🥊
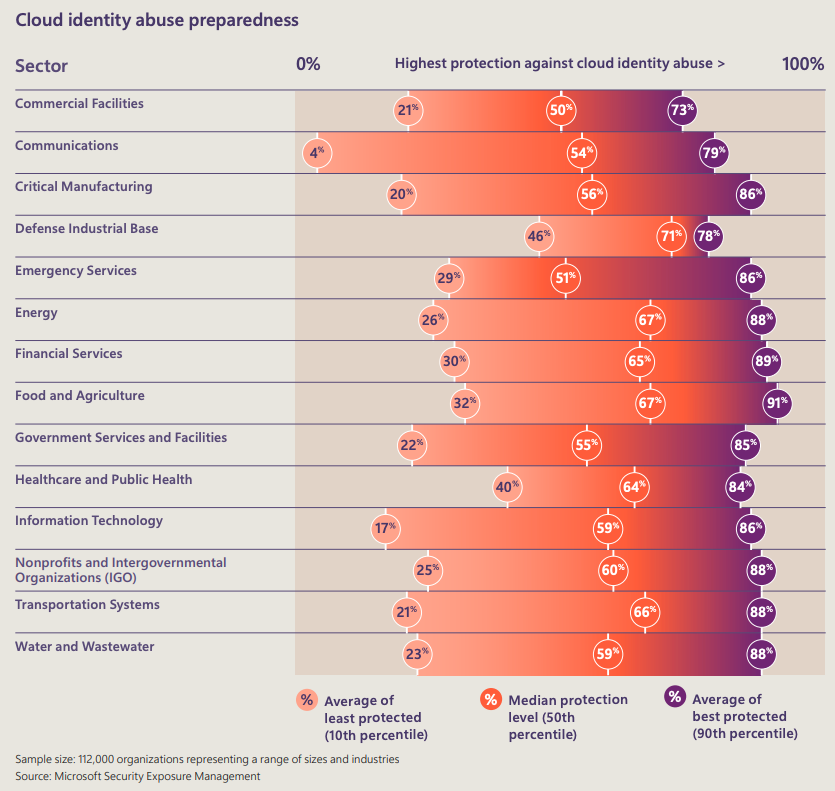
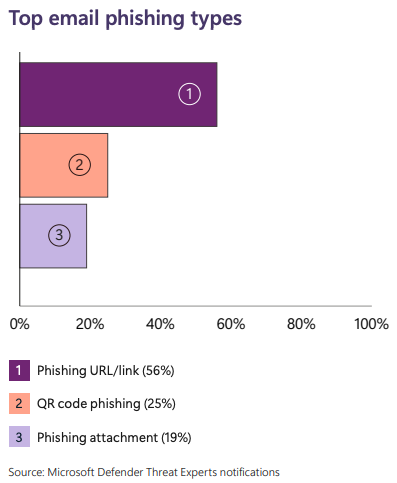
Get an overview of identity attacks, cloud identity abuse, the impacted sectors of phishing and types, as well as the top human-operated ransomware groups and common attack path insights.

7. Nation-state report ⚔️
Russia 🇷🇺 - Ukraine 🇺🇦 conflict
- Activities: Russian threat actors have focused on infiltrating Ukrainian military and infrastructure networks. They use malware such as USB-delivered worms (Aqua Blizzard) and pirated software to gain access.
- Impact: These attacks not only target Ukraine but also threaten global networks, as the malware can spread beyond intended systems. Russian actors also attempt to access Western organizations involved in supporting Ukraine .
China 🇨🇳 - South China Sea Region
- Activities: Chinese cyber actors, including Raspberry Typhoon, Flax Typhoon, and Granite Typhoon, have targeted IT, military, and government entities in ASEAN countries. They focus on regions of strategic importance like the South China Sea.
- Impact: Their operations aim to gather intelligence and potentially disrupt military activities, particularly during military exercises involving nations such as Indonesia, the Philippines, and the U.S. .
North Korea 🇰🇵 - Cryptocurrency Theft
- Activities: North Korean groups have stolen over $3 billion in cryptocurrency since 2017 to fund state programs. These actors, such as Moonstone Sleet, are also engaged in ransomware attacks like the FakePenny variant.
- Impact: North Korea's cyber operations have dual purposes: to fund their nuclear and missile programs and to gather intelligence, making them a persistent global threat .
Iran 🇮🇷 - Israel 🇮🇱 and Middle East
- Activities: Iranian actors have targeted Israeli companies and attempted influence operations in response to the Israel-Hamas conflict. Their attacks combine cyber operations with misinformation campaigns aimed at undermining Israeli military efforts and international support.
- Impact: Iran’s cyber activities are expanding beyond Israel, targeting nations such as the U.S. and Gulf countries, with broader objectives to influence regional politics.
8. Cyber Point of Views 🕶️
Japan 🇯🇵
- Cybersecurity Measures: Japan has recognized cybersecurity as a national security issue for the first time in its revised National Security Strategy. The country is focusing on Active Cyber Defense (ACD) and building a new Cyber Command with 20,000 personnel by 2027.
- Impact: Japan's efforts aim to strengthen its defense forces, protect government and civil society, and improve cooperation with international allies.
Australia 🇦🇺
- Cybersecurity Partnerships: Australia has launched the Microsoft-ASD Cyber Shield (MACS) initiative, a public-private partnership between Microsoft and the Australian Signals Directorate (ASD) to improve cybersecurity collaboration.
- Impact: This partnership has led to successful actions, such as identifying and sanctioning perpetrators of a major ransomware attack against Medibank. It highlights how public-private cooperation can enhance national cyber resilience.
Israel 🇮🇱
- Iranian Cyber Attacks: Following the outbreak of the Israel-Hamas war, Iran ramped up its cyber and influence operations against Israel. Iranian actors targeted Israeli companies and used influence campaigns to undermine international support for Israel's military operations.
- Impact: These cyber-enabled operations seek to degrade Israel’s strategic capabilities and project power through cyberattacks, while also attempting to destabilize Israeli society by influencing public opinion.
United Kingdom 🇬🇧
- Cybersecurity Initiatives: The UK remains a prime target for nation-state actors, particularly from Russia, due to its involvement in global geopolitical affairs. The UK has focused heavily on enhancing its cyber defense capabilities, especially around critical infrastructure and public services, in response to the growing cyber threats.
- Impact: The UK is working closely with international allies to strengthen cybersecurity through strategic partnerships, aiming to improve resilience against both state-sponsored attacks and broader cybercrime activities.
United States 🇺🇸
- Supply Chain Attacks: U.S. organizations are often targeted in nation-state cyberattacks, particularly by Russian actors like Midnight Blizzard, who aim to infiltrate IT firms and government systems. These attackers use supply chain attacks to target downstream customers in North America and Europe.
- Impact: Such attacks highlight the critical need for securing supply chains and implementing robust cybersecurity measures to protect IT infrastructure and sensitive government data.
South Korea 🇰🇷
- North Korean Threats: North Korea continues to target South Korean organizations, especially in sectors like IT and finance, using tactics such as ransomware and espionage. North Korean cyber actors seek financial gain and intelligence collection to support state objectives.
- Impact: These attacks are part of North Korea’s broader strategy to fund its nuclear programs and maintain its cyber capabilities.
Sweden 🇸🇪
- Cybersecurity Focus: Sweden is increasingly focused on strengthening its cybersecurity infrastructure in response to growing threats from nation-state actors, particularly in the context of geopolitical tensions in Europe. The country has prioritized building resilience in critical infrastructure and improving collaboration with international partners.
- Impact: Sweden's proactive approach aims to safeguard its digital infrastructure and ensure its ability to counter sophisticated cyber threats, particularly those originating from Russian state-backed actors in the region.
Albania 🇦🇱
- Development: Albania has faced increasing cyber threats, particularly following significant political tensions. The country has been working to strengthen its cybersecurity infrastructure and resilience to handle future attacks, particularly from nation-state actors.
- Impact: The focus on improving collaboration with international allies and enhancing national cybersecurity measures is key to Albania’s efforts to safeguard critical infrastructure and defend against politically motivated cyberattacks.
9. Election interference 🔖
The election interference section in the report highlights how nation-states such as Russia, China, and Iran increasingly use cyberattacks and disinformation campaigns to manipulate elections. These efforts target both election infrastructure and public opinion, aiming to undermine trust in democratic processes and advance geopolitical agendas. By the end of 2024, nearly 2 billion people will be affected by these operations, which use cyber tools and influence tactics to sway voter behavior and create confusion around election outcomes. These actions pose a growing challenge for maintaining electoral integrity worldwide.

10. Contributing teams 🫴
An honorable mention goes out to the Microsoft teams and partners who provided key data and insights for this report. Here are some of the top contributors:
- Azure Edge + Platform: Responsible for Microsoft’s operating systems, IoT, edge products, and engineering systems.
- Commerce Risk Engineering Team: Protects transactions on Microsoft and Xbox through AI-driven risk management.
- Central Fraud and Abuse Risk: Detects and responds to fraud threats from nation-states, criminal syndicates, and hackers.
- Cloud Ecosystem Security: Secures Microsoft’s cloud platform with data security, compliance, and AI-powered threat intelligence.
- Core Datacenter Services: Ensures global availability and safety across Microsoft’s data center operations.
- Critical Infrastructure Networking & Cyber Defense: Provides safe connectivity and protection for Microsoft’s data centers.
- Customer Experience Engineering (CxE): Engages with customers to improve Microsoft security products.
- Digital Crimes Unit: An international team fighting cybercrime by disrupting global threats and protecting individuals and organizations.
- Enterprise & Security: Develops platform technologies to strengthen cybersecurity.
- Microsoft Defender Experts: Provides managed threat hunting and response services.
- Microsoft Incident Response (DART): Provides incident response services and strategic threat intelligence.
- Microsoft Threat Intelligence Center (MSTIC): Tracks and disrupts nation-state and financially motivated threat actors.
powered by Oceanleaf


