Microsoft Cloud Security: Top 10 low-hanging fruits
Introduction
Almost every modern organization, regardless of startup or established enterprise has Microsoft 365 or Azure services in place to fulfill IT requirements and operations. The most common services include:
- Microsoft 365 Apps (Teams, Outlook, Office etc.) for collaboration
- Entra ID for the user accounts, identity (resources)
- Azure platform hosting computing resources
What to expect
In this post I want to share my experience for small & medium businesses (SMB) as well as large enterprises when it comes to Microsoft Cloud Security. The target audience are especially managed service providers (MSP) or internal IT administrators who aren't experts on the Microsoft Cloud subject and want to have an easy to understand guide. This is it 😉
List of low hanging fruits
I define a "low-hanging fruit"🍒 as:
Easy to implement control that elevates your security posture immensely, without disturbing processes.
In my daily work I have insights into a lot of Microsoft 365 and Azure infrastructures and their usage. Regardless of large enterprise or SMB, most of the low hanging fruits are equal. BUT an SMB is more agile and can implement those faster and is easier with adjustments. Large enterprises should host an internal IT department with more budget for security.
Challenge: How to start?
There are endless of security measurements that you could take to make your digital infrastructure more secure. However, resources are limited and we want to achieve the highest possible security. In this post I will make a list of topics and key considerations and provide a description to them. Those are based on industry standards, personal experience and common security knowledge.
Defining the goal
We want to focus on topics that:
- 🚀 Bring in the most obvious security and protect the largest attack surfaces
- ✅ Are easy to implement and operate
- 😡 Don't mean end user drawbacks or high negative impact on productivity
In my definition, cybersecurity is about:
Ruin the potential attackers return on investment.
Means: Security technologies and controls should be as effective, that the attackers effort isn't worth the return. (Return in this case would be access to accounts, data or digital infrastructures.)
Surprisingly, this is achievable by basic security hygiene and simple configurations. Based on the Microsoft Digital Defense Report, basic security hygiene protects against 99% of the attacks. Sounds like a good deal, if we can achieve the basic security hygiene 🤝.
Overview Top 10
This is my personal list of top 10 security controls that should be implemented in every organization.
| Title | Security area | Involved products | Recommendation |
|---|---|---|---|
| Enable multi-factor authentication | Identity & access control | Entra ID | Enable MFA for all users so their authentication is strong and an attack would need both 2 factors to get access. |
| Stay up to date | Process and technology | - | Enable auto-update services in everything - Windows Update, app updates and service updates. |
| Use endpoint protection software | Threat protection | Microsoft Defender (for Endpoint) | Enable and configure Defender (for Endpoint). Make sure you control the settings via GPO or Intune so a user or potential attack can't modify it. |
| Review role assignments and RBAC | Identity & access control | Entra ID | Review your role assignments, make sure to only use least privilege needed. Split roles and permissions based on job role and responsibility. |
| Activate Conditional Access template policies | Identity & access control | Entra Protection Conditional Access | Enable all recommended or template Conditional Access policies to ensure access control based on signals. |
| Ensure tenant security settings | Identity & access control | Entra ID | Review your tenant based on best practice frameworks and make general security configurations. |
| Implement modern mail protection | Threat protection | Microsoft Defender for Office 365, Exchange Online Protection | Review and adjust your mail protection policies like Defender for Office 365 to protect from spam, phishing and malware, attachments and links. |
| Set up notification on alerts | Threat response | Microsoft Defender XDR | In case of a detected incident it is important that you get notified. In Defender XDR you can set up alerts for incidents. |
| Awareness trainings | Awareness | - | Create awareness for your employees by trainings and attack simulation trainings. |
| Evaluate new technology | Mindset | Any | Once new technology is released, evaluate it and check potential implementation cost and value. |
1. Enable multi-factor authentication
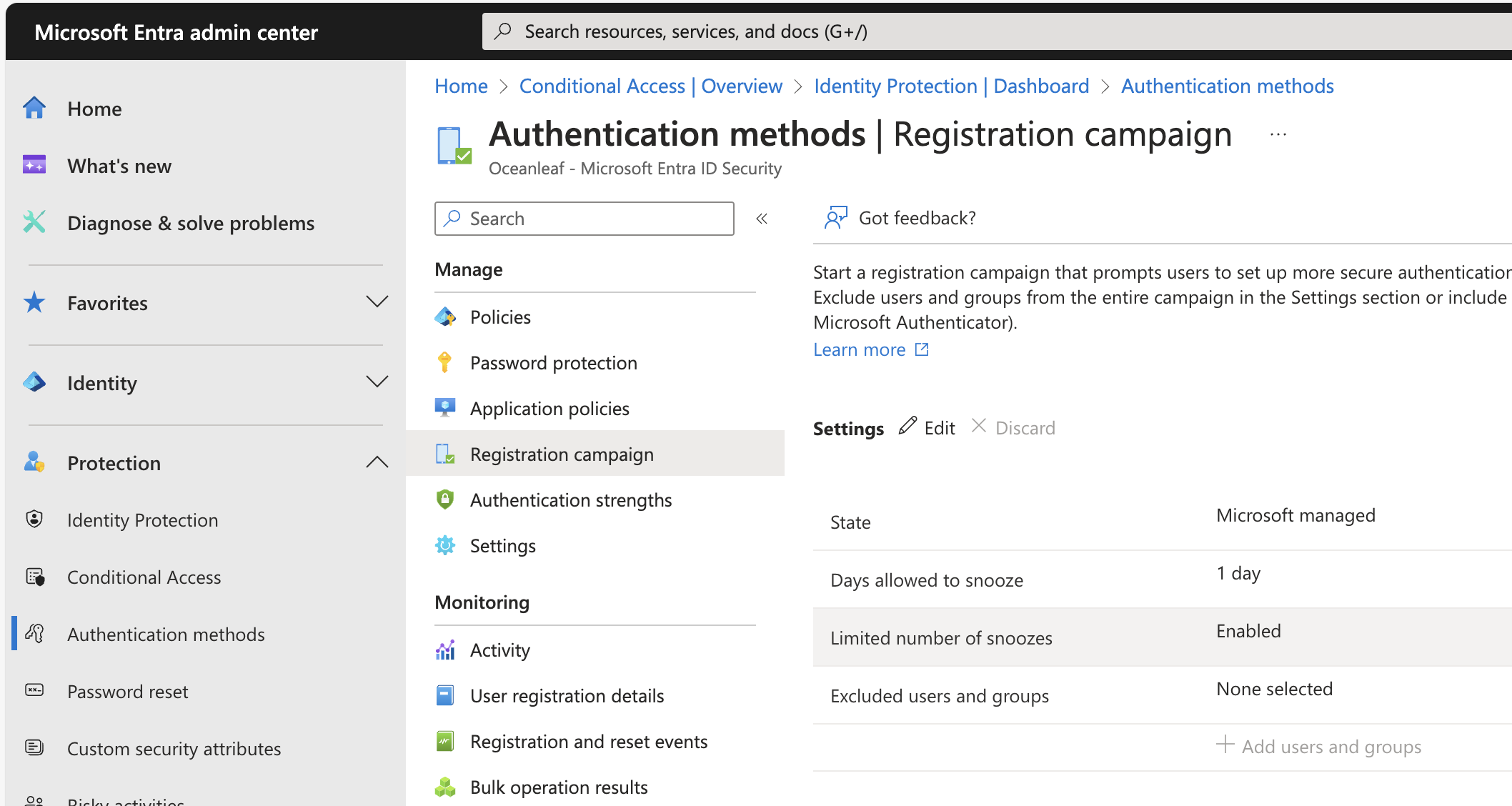
Multi-factor authentication is the best and easiest way to elevate your security. It protects your identities by requiring two factors to authenticate. Modern MFA methods that should be used are the Microsoft Authenticator App, FIDO 2 keys and passkeys or a Temporary Access Pass. You can start enforcing MFA with a registration campaign in Entra ID Protection:
2. Stay up to date
Up-to-date software ensures that vulnerabilities are patched directly by the vendor of the software. If you mainly use SaaS (Software as a Service) apps in the web, you are released from this challenge. But if you have client installations or any operating system, you should ensure that those products automatically update themself. Ensure auto-update features are enabled or regularly update the version manually. There are also tools on the market that do auto-update for you.
3. Use endpoint protection software
Threat protection and endpoint detection and response systems should be installed on every endpoint. My recommendation is to use Microsoft Defender Antivirus and Defender for Endpoint for cloud-powered protection. Make sure to enable these products and configure them accordingly. Find more information here:

4. Review role assignments and RBAC
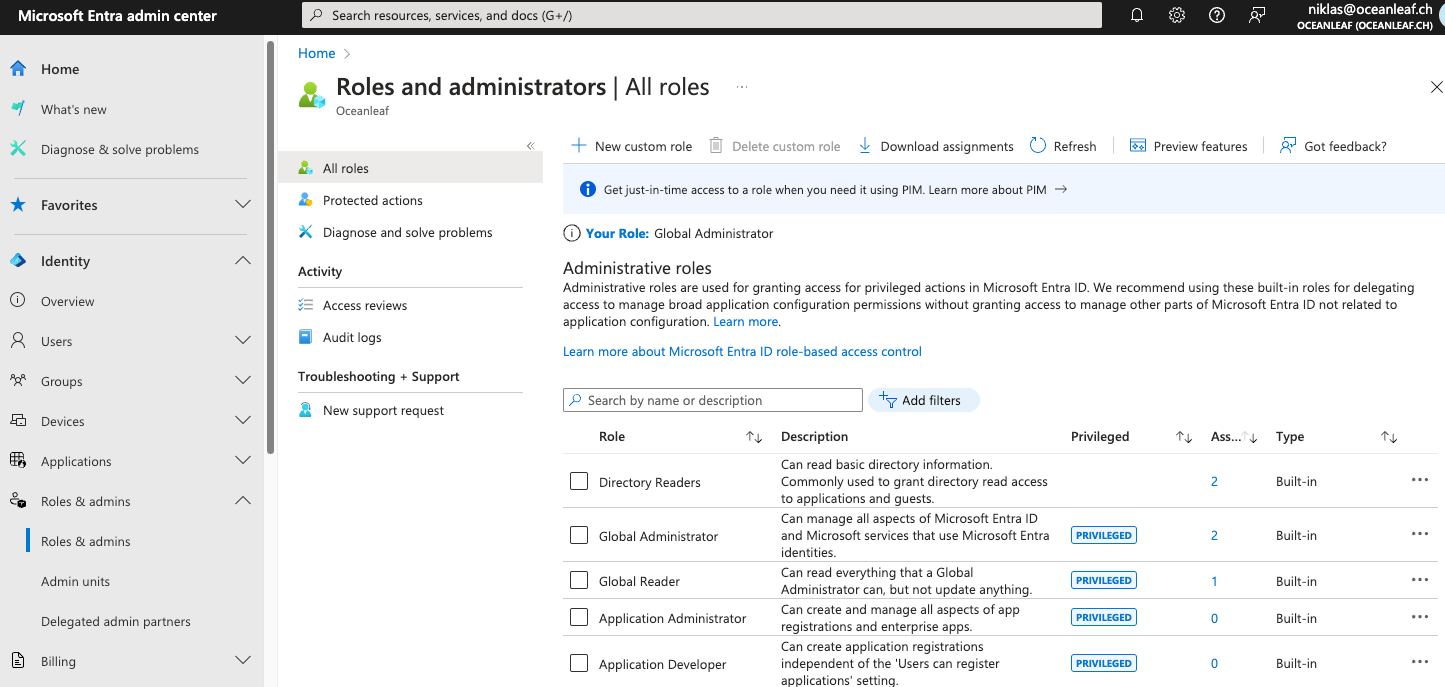
Roles are user with special permissions like administrators in your environment. Role-based access controls should be implemented to adhere the least privilege principle that states that should only be able to perform actions that you need to do based on your job role. With every tenant that I touch, I have a look at the roles blade in Entra ID:
5. Activate Conditional Access template policies
Conditional Access is the heart of every Microsoft tenant when it comes to identity & access management. This is one of the key products to implement and use. It lets you define signals like geographical location, device state or risk level to define access requirements. Micorsoft equips every tenant with a set of recommended template policies. You should review them, estimate the impact and set them live.
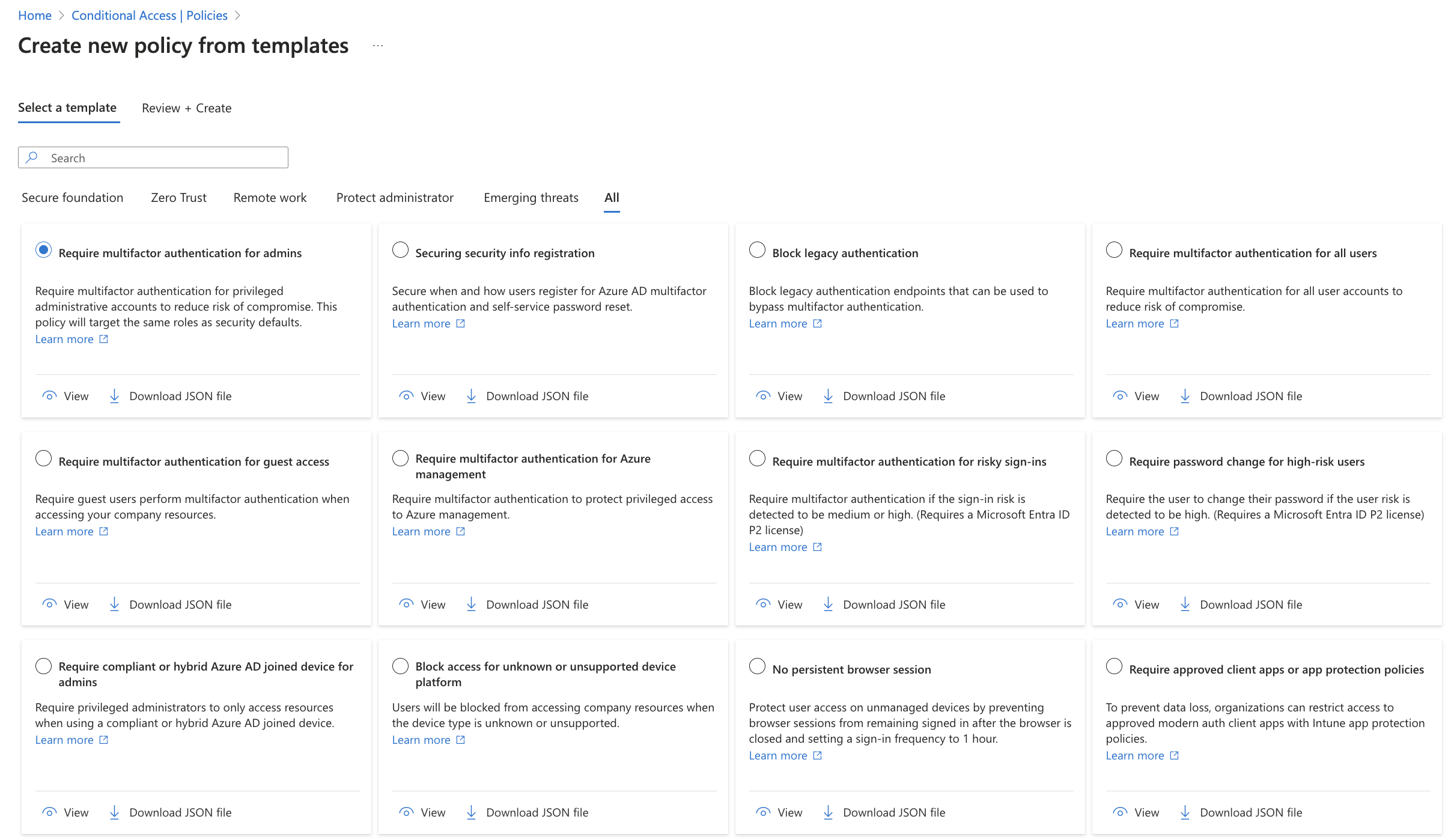
Read my blog post about Conditional Access:

6. Ensure tenant security settings
Tenant security settings build the foundation of your identity platform such as Microsoft Entra ID. There are many good frameworks to orientate which settings are important. Nevertheless, you should at least have a look at all the settings and know whats possible. I can recommend Maester as Microsoft Security test automation framework.
7. Implement modern mail protection
Mail threats are one of the most common attack methods. End users frequently interact with mails and mail content like attachments or links, that could be malicious. Defender for Office 365 provides adequate protection to those threats. Read more in my dedicated blog post:

8. Set up notification on alerts
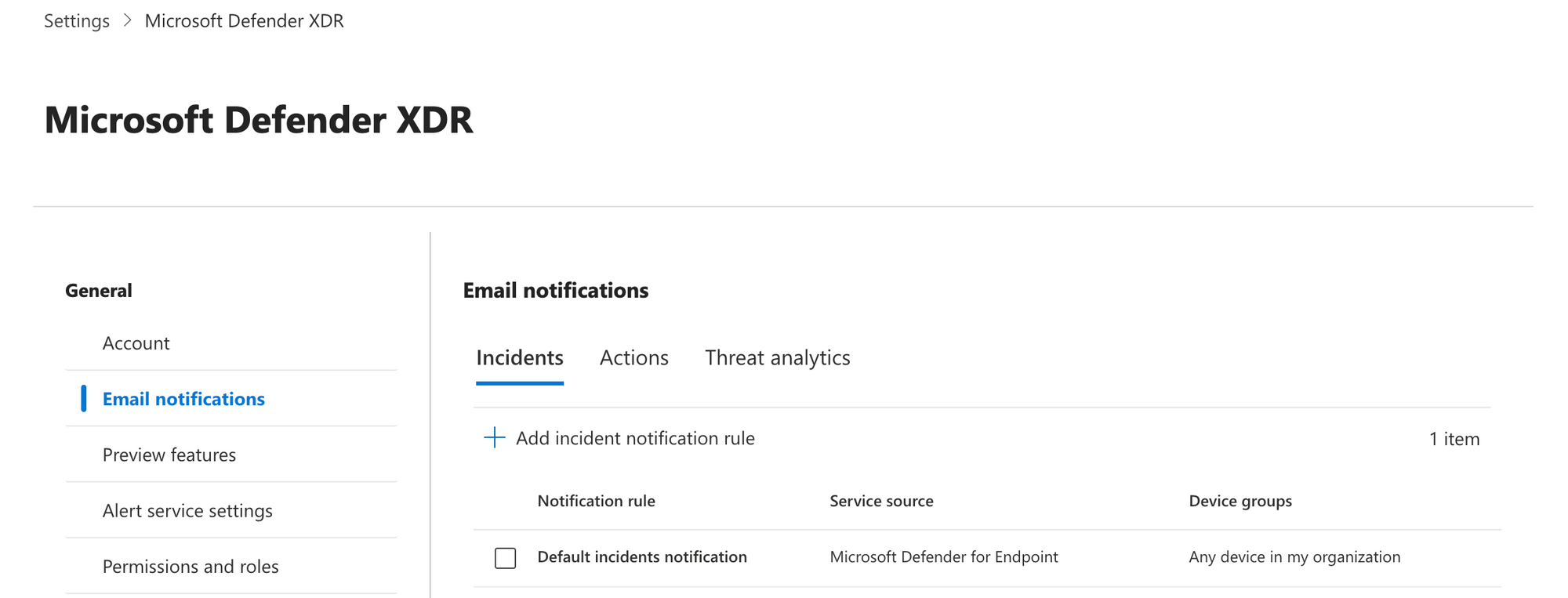
Notifications in Microsoft Defender XDR can easily be set up at security.microsoft.com in the settings. Set up alerts for Incidents (a group of alerts triggered, indicating for a security incident), Actions (tasks and operations that were started in Defender automatically or manually) or Threat analytics (Information on the cybersecurity landscape, provided by Microsoft.)
9. Awareness trainings
Last but not least I recommend to involve all of your users (including admins) to do awareness trainings. Those should raise the understanding and readiness for potential upcoming threats and how to treat them. From my experience, a personal workshop is always the best method to achieve this. But for sure it must be said, that you should not rely on the users decision, but make the security controls as effective as possible. Also you can consider the Defender for Office 365 attack simulation training.

10. Evaluate new technology and keep an eye on the market
This is probably one of the most challenging parts of staying secure. As adversaries don't stop developing their technology-related attacks, neither should you! Microsoft releases new features almost every day, and it can sometimes be hard to keep track. Evaluate new features regularly and check if they are worth implementing. This way, you will ensure not just to be safe, but to stay safe!
Oceanleaf is your one-stop Microsoft learning shop.
powered by Oceanleaf




