Microsoft Defender: a review
Defender
The history of Microsoft Defender is an interesting one. Originally, it was ridiculed by security experts as an incompetent operating system antivirus that was usually shut down right away. However, Microsoft made a decisive move and added the power of the cloud. So, in addition to real-time protection based on a heuristic system (making adequate decisions in the shortest possible time with little information), there is cloud-based protection added. Through big data and a massive amount of information and security related events that Microsoft has collected on its operating systems. In this position with as much information and power as Microsoft has, they can use it to further develop and design their products.
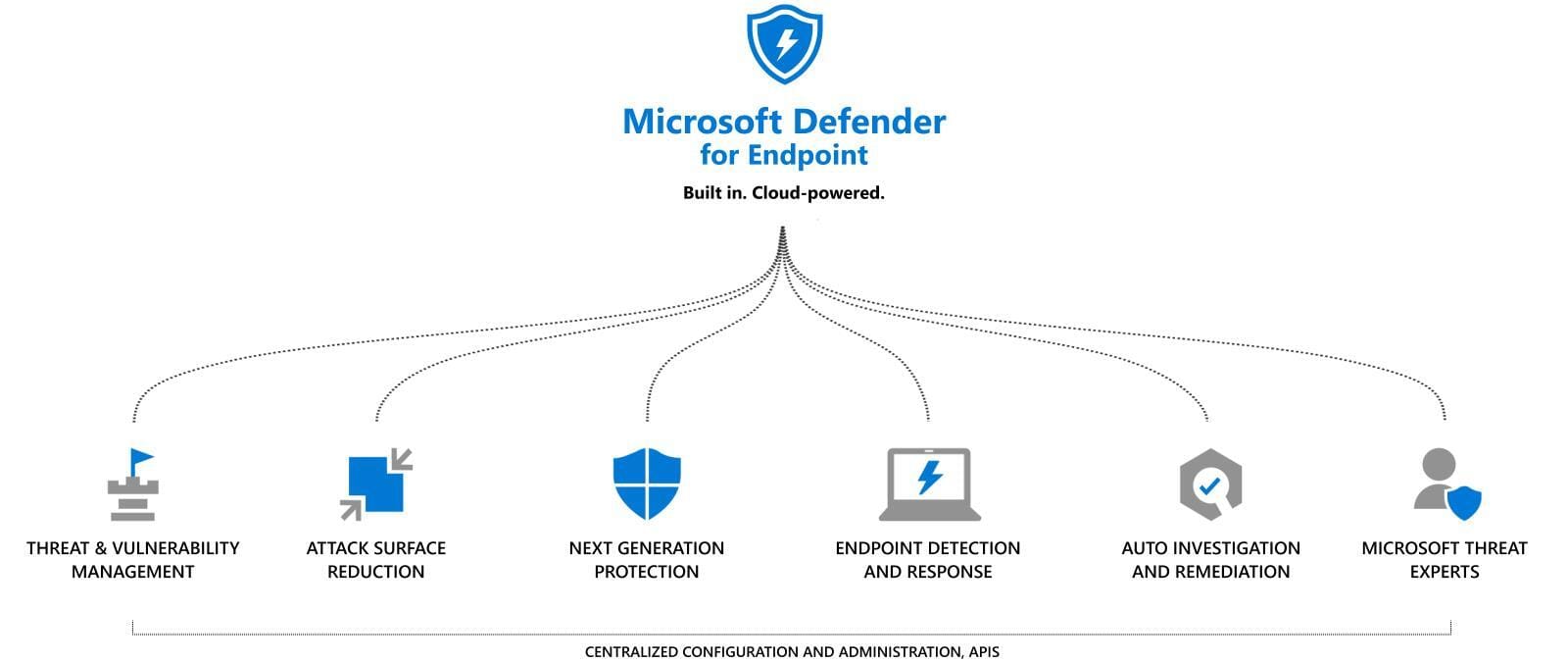
Defender for Endpoint
Defender as a standalone product against potentially unwanted software, together with cloud-based protection performs its main task on an ordinary system. However, in a networked and multi-faceted security landscape, it is often desirable to collect more information and enforce measures for daily operations. This is where Defender for Endpoint (formerly Microsoft Defender Advanced Threat Protection) comes in, helping organizations prevent, detect, investigate and respond to threats.
To use Defender for Endoint, a sensor will be installed on the endpoint, which transfers data to the individual Microsoft tenant. This deployment process is called "onboarding". Later on, the full amount of information including all events, processes, applications and data on the device is regularly captured, as well as uploaded and then graphically displayed in the Security Center (https://security.microsoft.com/). From this data, analyses can be made efficiently and quickly in the portal by an IT employee and further steps can be planned.
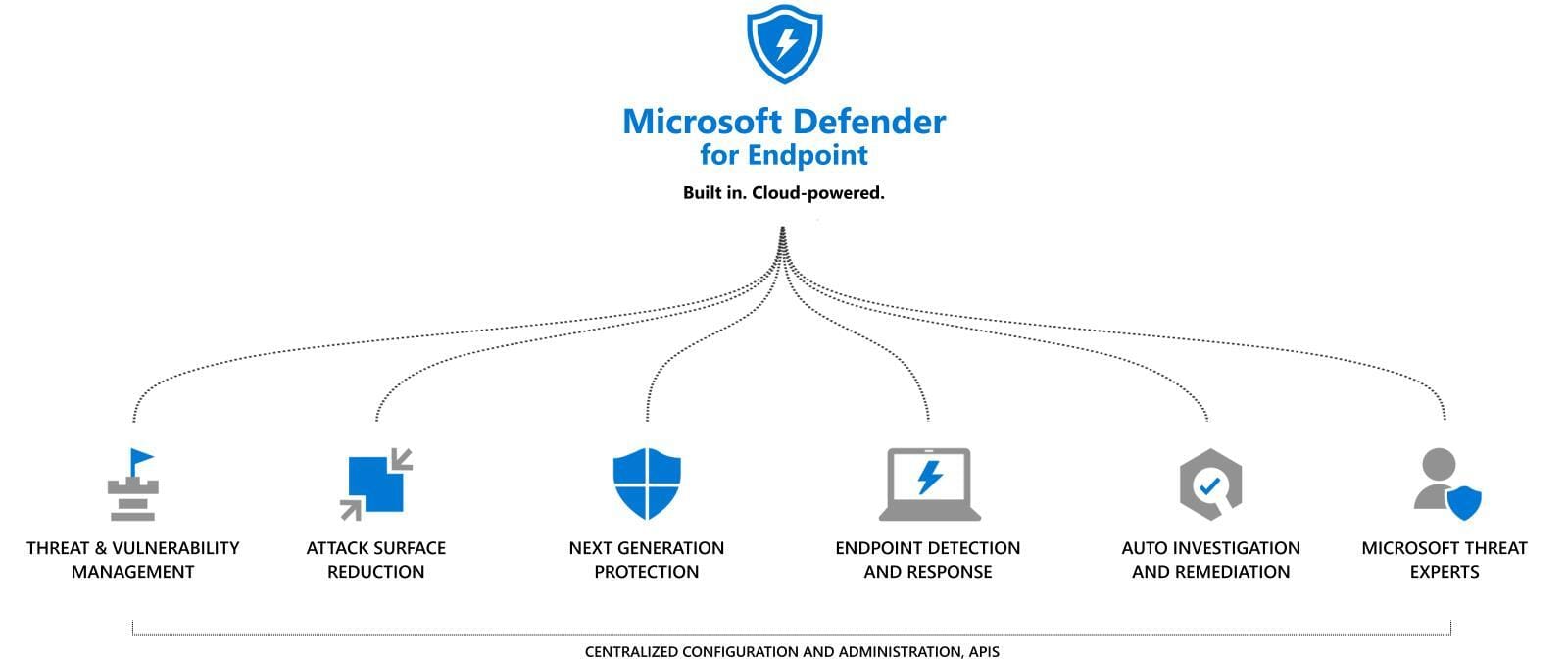
What does Defender for Endpoint do?
Threat & Vulnerability Management
The main task of DFE (Defender for Endpoint) is to detect and manage potential threats and vulnerabilities in an environment.
Attack surface reduction (ASR)
In the field of security, the term "hardening" is often used. The meaning of this is to control a system and set up restrictive configurations so the overall risk is minimized and the attack surface is reduced.
Next-generation protection
Next-generation protection relies on real-time analysis of the behavior of a user's or the system's activities. This can prevent zero day attacks and advanced threats.
Endpoint detection and response (EDR)
The concept of EDR describes all security-related actions performed on an endpoint device to combat malware that has bypassed previous security perimeters.
Automated investigation and remediation
Investigations of threat conjunctions are automated by the DFE, which can help reduce manual work through an employee.
Microsoft Threat experts
Microsoft works with over 3,500 security experts around the world who accurately help identify and respond to threats.
Why Microsoft?
The Hybrid Capabilities. It's a fact that about 80% of Fortune 500 companies are already using Azure and most of them came from a traditional Active Directory domain. Migrating from that position to Azure is simply the easiest and most convenient way imaginable. Service jungle; Microsoft's services help organizations digitize and simplify tasks from every angle. The last one is globalization & unification. Why should every organization have its own SecOps team? Why not leverage the immense capabilities of the Microsoft Cloud, which has so much security-related information, to counter global threats with full force.
Licensing
Microsoft's enterprise licensing plans for security based products are most of the time an elevated bundle of products. But there is a good message: the basic Defender preinstalled on Windows is completely free. But what about Defender for Endpoint? -From a license perspective we talk about Microsoft 365 E5 Security, that is included in the step-up Enterprise Mobility + Security suite. I recommend M365maps for a complete overview.
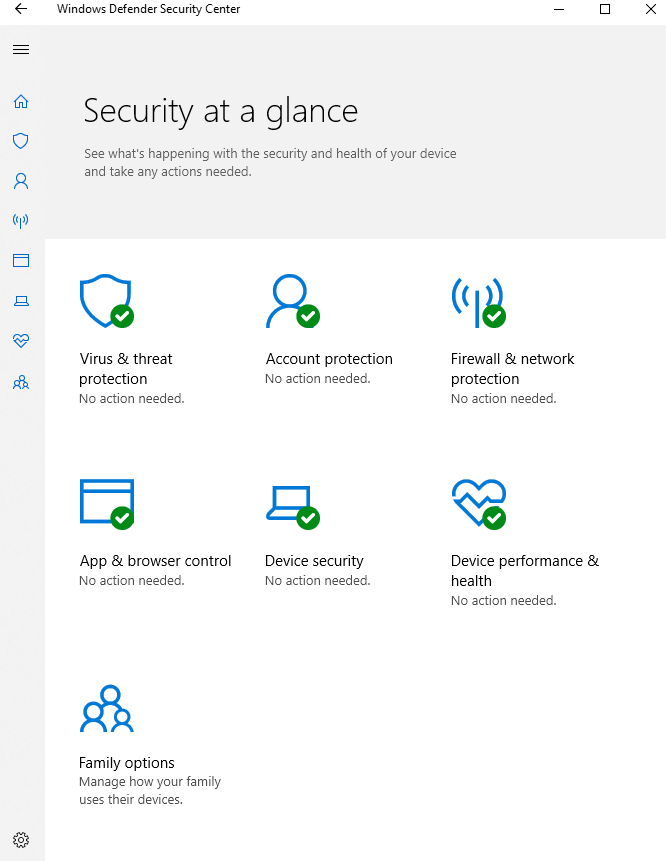
Defender configuration
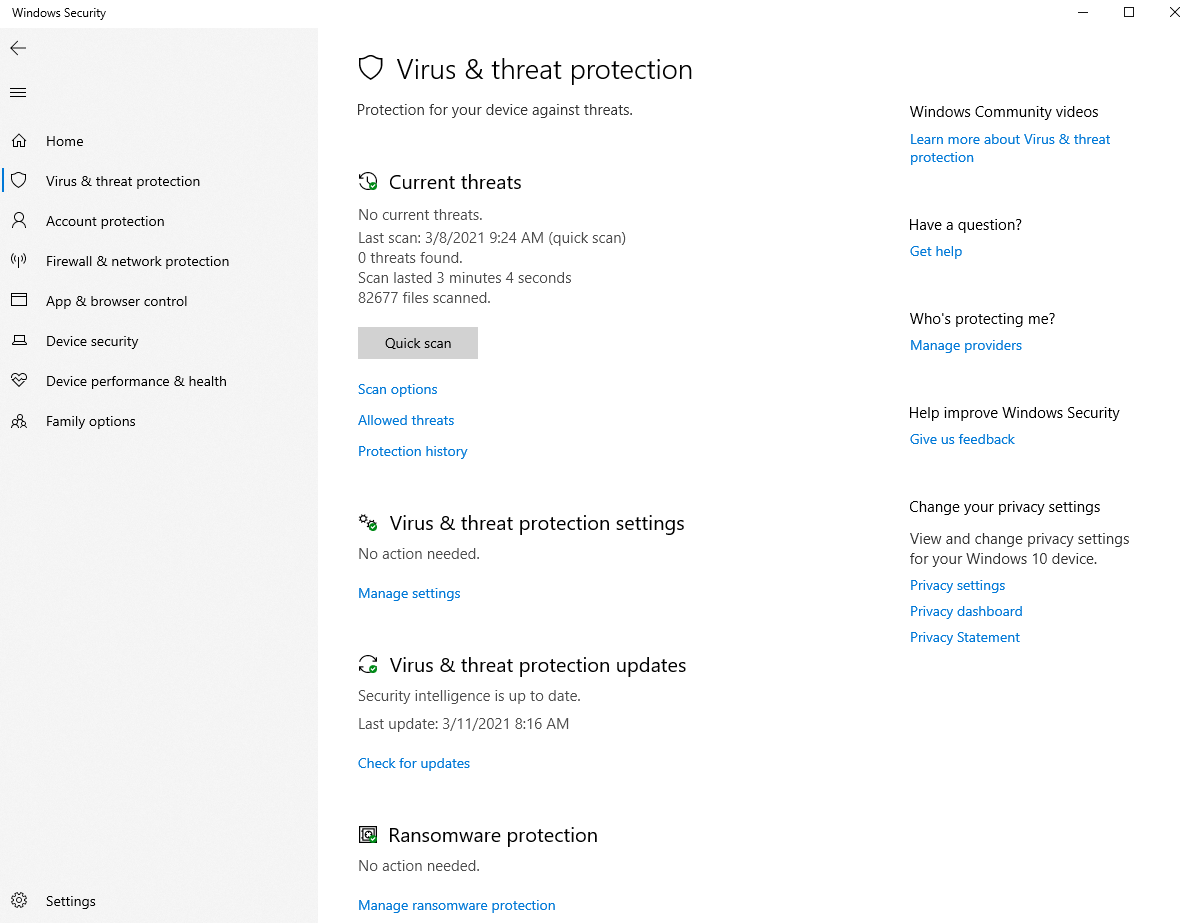
Virus & Threat Protection
Virus & Threat Protection focuses on the core tasks, such as antivirus protection on the system. This is where scanning options, information about detected threats, and basic settings and updates are managed.
The main components of it are:
Real-time protection
Simply put, real-time protection prevents any installation or execution from being performed on the device at any time.
Cloud delivered Protection
When a security threat is found, it is automatically uploaded to the Microsoft Cloud, where it is reviewed. If it poses a real threat, then as much information as possible is collected and stored into the cloud. This leads into the big advantage of all other Defender users benefit directly. Due to an immense amount of active Defender installations with internet connection, this database is constantly growing, which contributes to the general security of Defender.
Updates
Windows Defender normally performs a daily quick scan. This is directly related to the scheduled updates. Defender always checks for new updates regarding security intelligence 15 minutes before a scan runs.
Automatic sample submission
In automatic sample submission, suspicious files are sent to Microsoft. There they are then analyzed by security experts and developers. The disadvantage here is that it can also send harmless files and basically generates more traffic.
Exclusions
In the exclusions tab we specify files, processes or also file types that won't be affected thorugh the Defender within it's work. These are then no longer scanned by Windows Defender and won't be interrupted, no matter what action they perform.
Enhanced notifications
In the enhanced notifications you can select whether Microsoft should send automatic messages with information about the health of the end devices. (Windows toast notifications)
Ransomware protection (controlled folder access)
Controlled folder access, protects user-configured folders from ransomware attacks that attempt to encrypt files. These accesses are blocked and the data at this location is secure.
Account protection
Account protection includes Windows Hello, the Windows integrated logon procedure and other options for unlocking Windows.
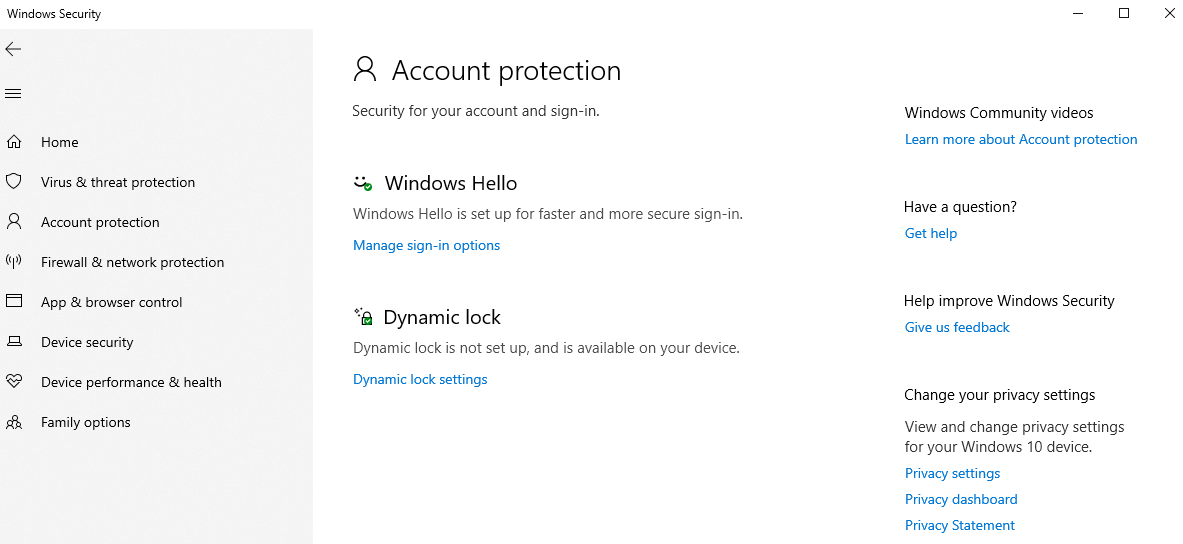
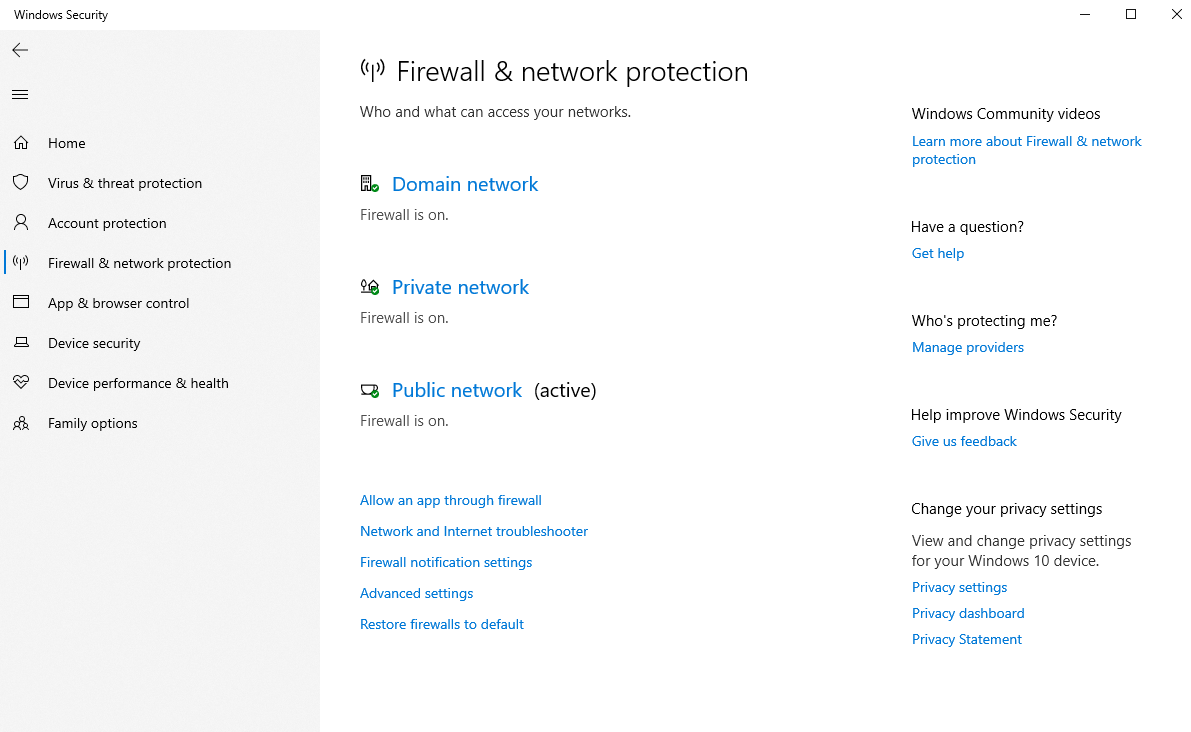
Firewall & network protection
The direct firewall, which is active on the device, is configured in this tab. It is mainly about the network types, like domain network, private and public network. Firewall rules for specific ports and protocols, for example, can also be managed here.
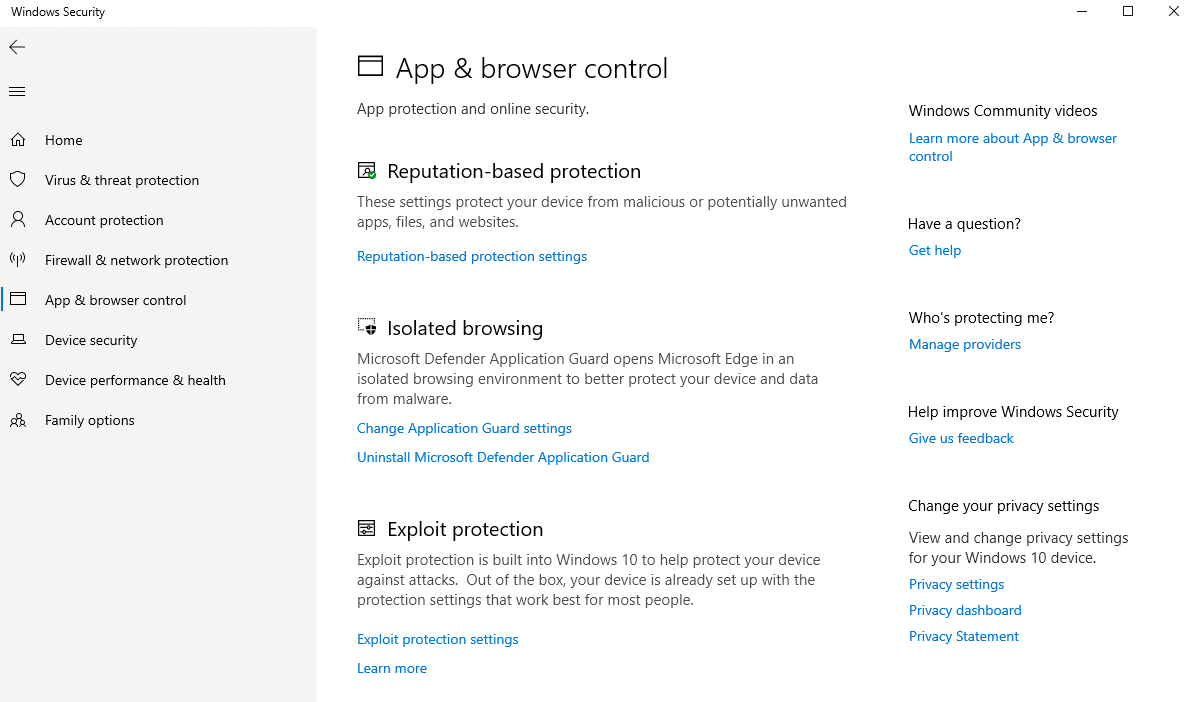
App & Browser Control
App & browser control includes some unique features of its kind. Smartscreen protects the device from malicious websites or downloads, isolated browsing via. Application Guard (virtualization is required) or Exploit Protection for system and program settings are well-known representatives.
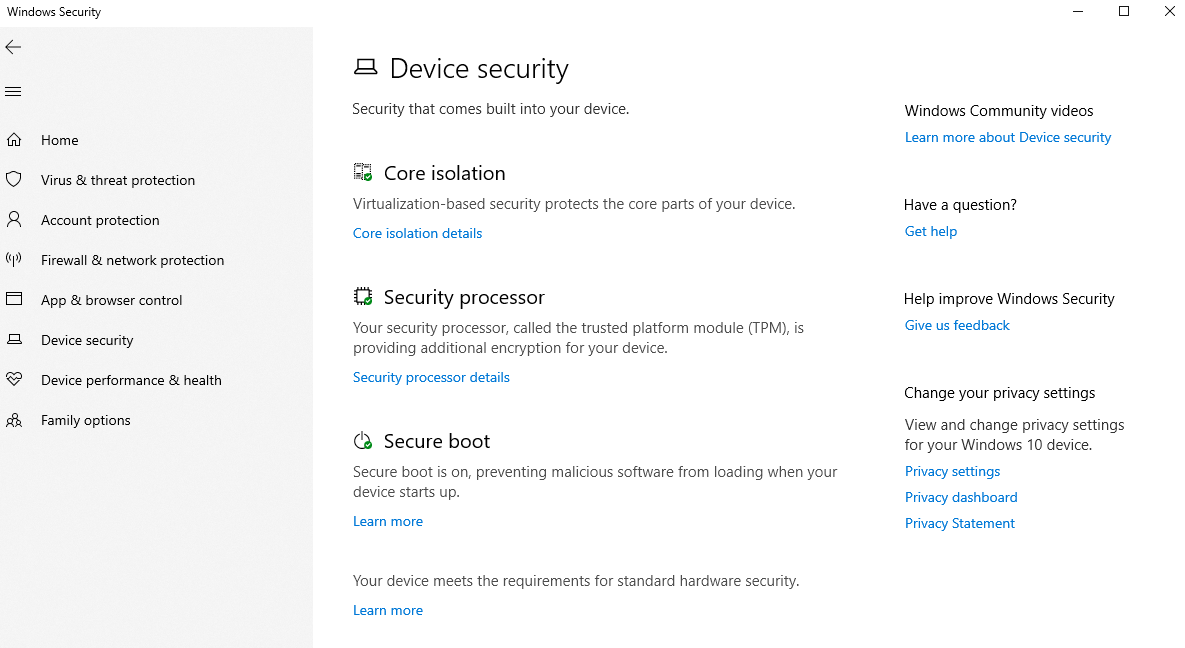
Device security
Technical and Windows-independent options such as the TPM (trusted platform module, which finds its use in Bitlocker, for example) or secureboot and other virtualization options.
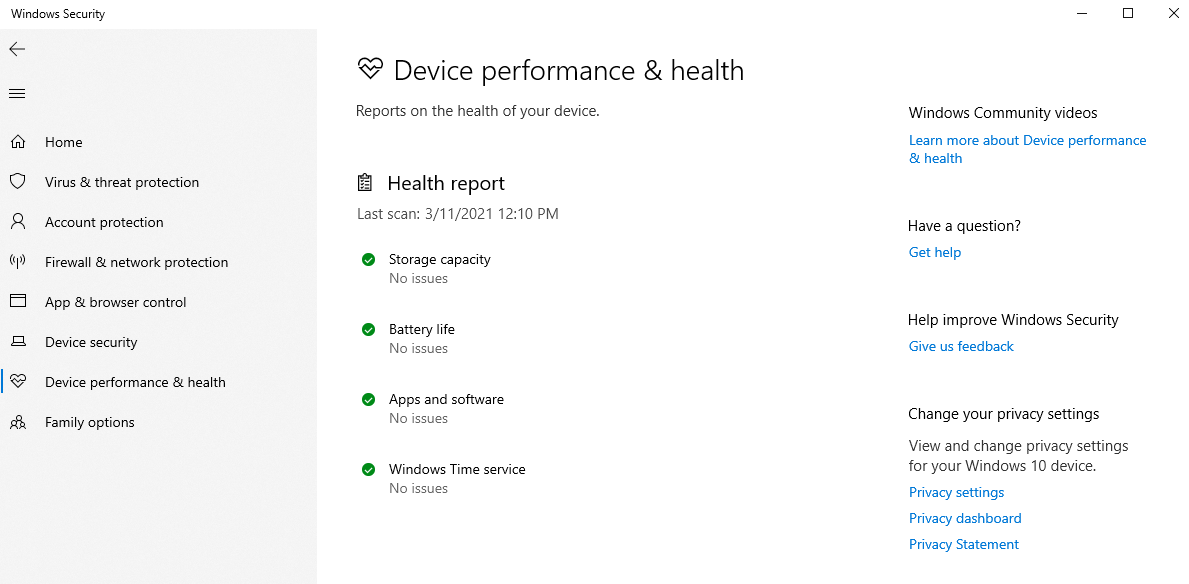
Device performance and health
An analysis of various services in Windows 10 is performed by device performance and integrity.
Family options
The family options provide further options for families and parental control in Windows 10.
Tests from the field
So how good is Microsoft Defender really? Let's run some malicious code and executables to see it's impact. I have a Windows 10 20H2 and a Windows Server 2019, with the latest patches installed (March 2021). Both with default Defender settings plus an onboarded Defender for Endpoint sensor and remediation options to "Full – remediate threats automatically". How to onboard Defender for Endpoint
EICAR
I am now going for a test virus from Eicar first. The file was only downloaded and has already tried to manipulate the system. Fortunately it got blocked instantly and sent a user notification that refered to the Windows Security center for further actions to take. We see very detailed information about the activity of the file in the Security Center (https://securitycenter.microsoft.com/) under the alerts of the machine.
Insight from the Security center
You can see directly that an "EICAR_Test_File" was detected as malware. An investigation was started automatically, which tries to provide more information and remediation options.
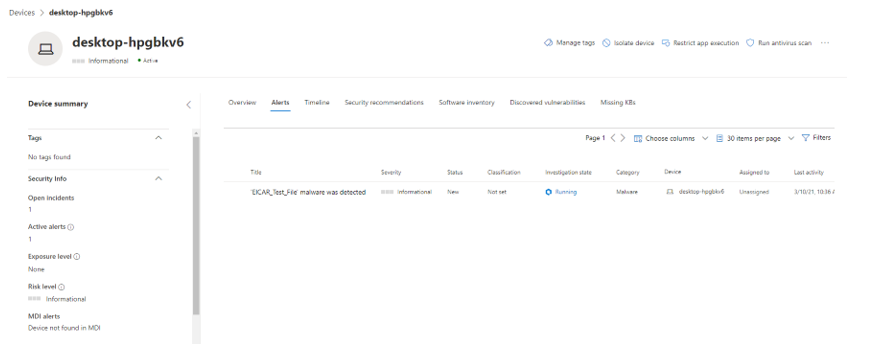
In this screenshot the complete trace is shown, including all files/processes and executables involved. The interventions started by a component of the Defender are written in red.
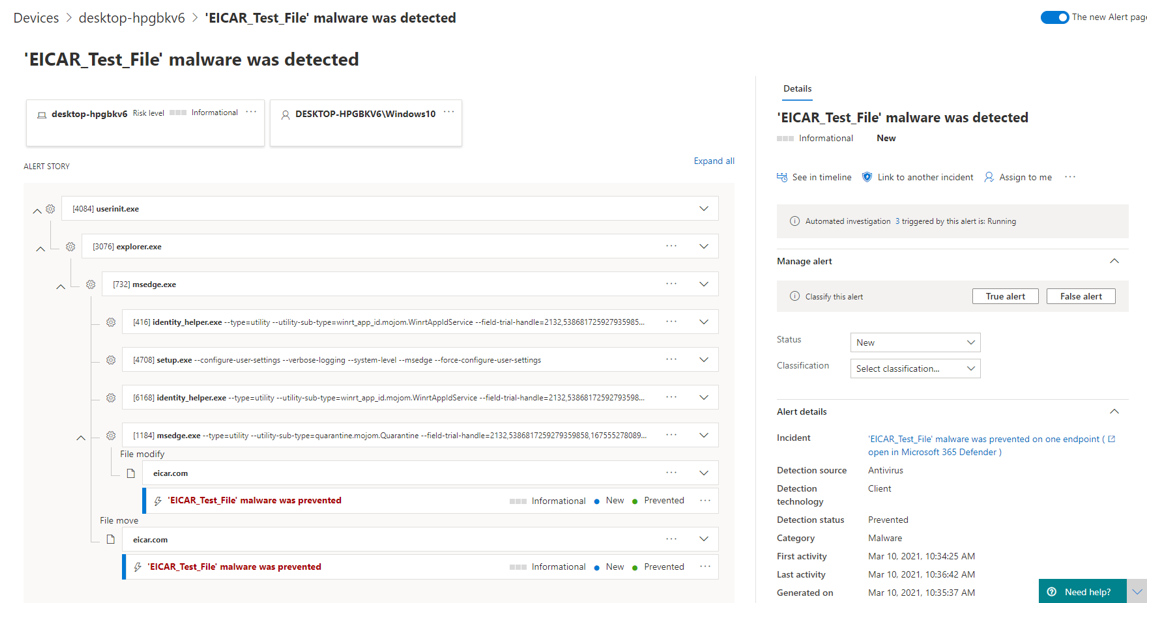
For the device, actions can be taken directly by an administrator. Isolate Device disconnects the device from any network communication immediately and without delay. This excludes communication from the DFE service. Run antivirus scan triggers a Defender scan on the device. Collect investiagion package collects logs and information from the device and uploads them to the cloud for more detailed analysis. Consult a threat expert would request a security expert at Microsoft for advice on this device and its concerns.
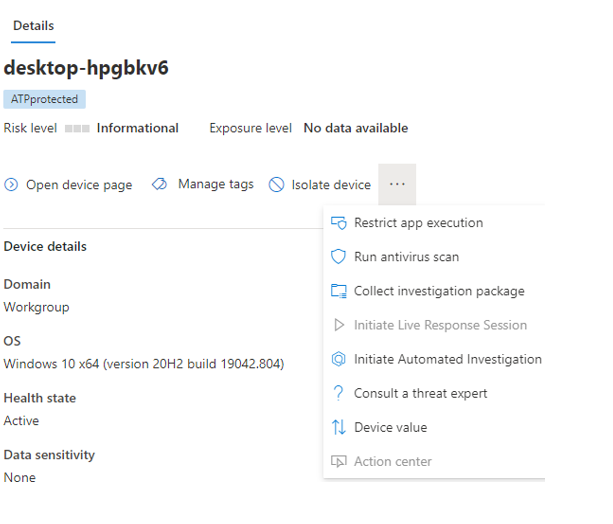
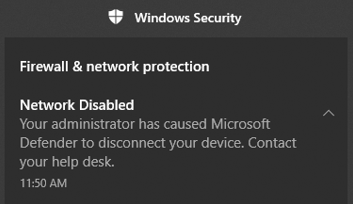
(The following message appears after the device is isolated. Network connectivity is immediately interrupted, it didn't even take a second after I clicked it in the portal).
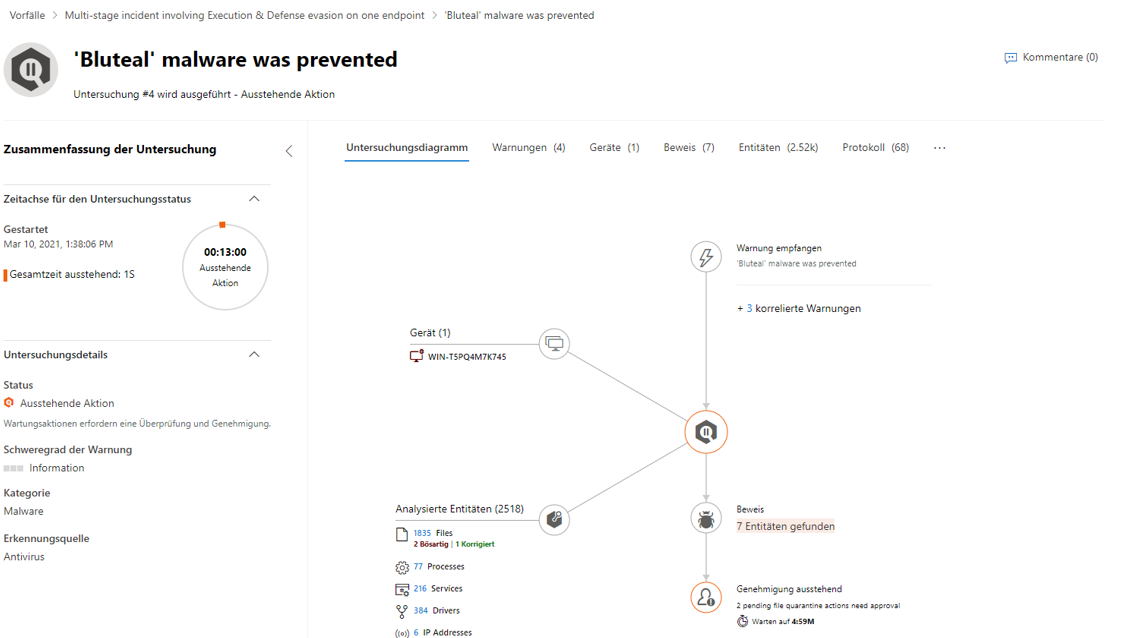
Investigation Graph
Because the context of one or more threats or malicious software is often very complex and chronologically difficult to understand, Microsoft presents an investigation graph with all the components and entities of a potentially dangerous activity.
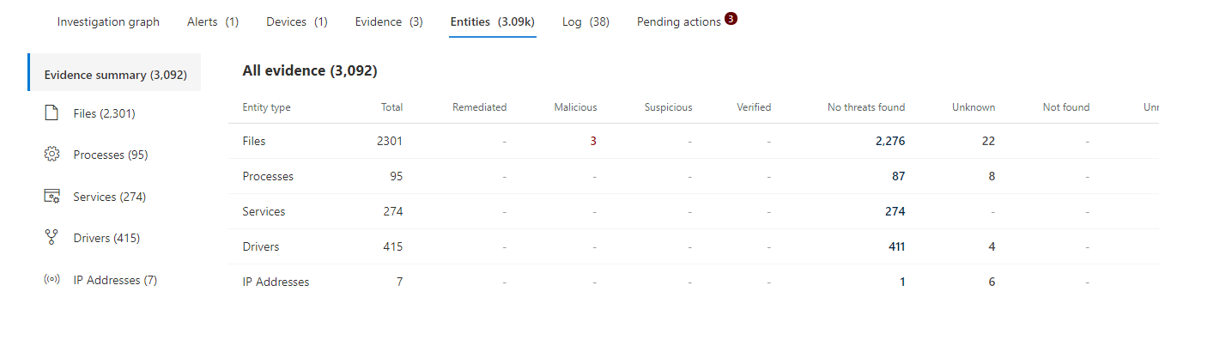
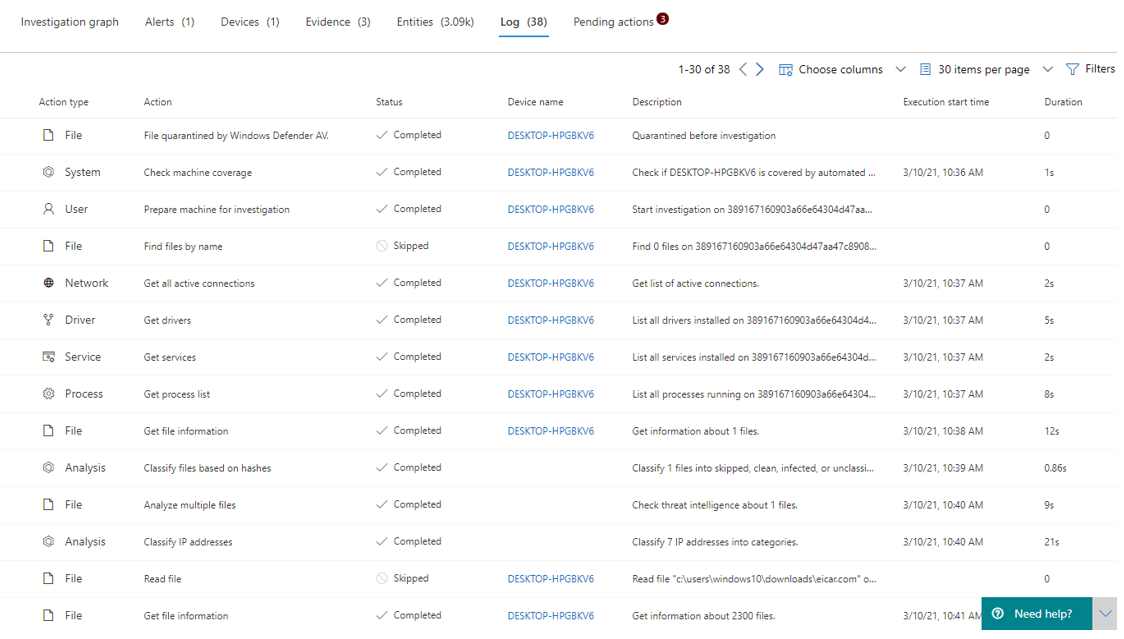
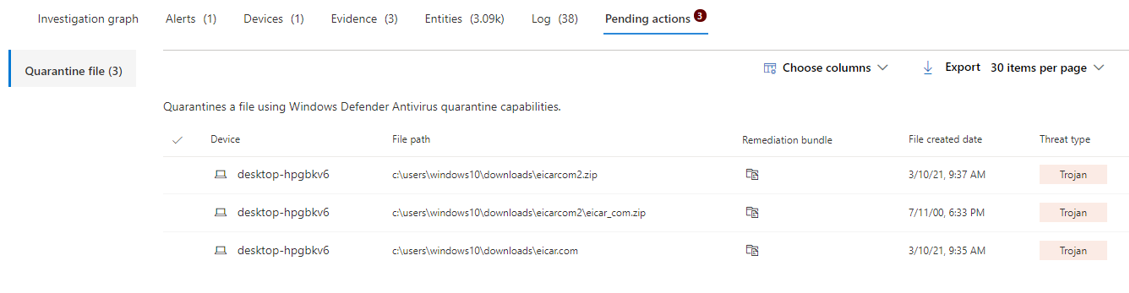
Knowbe4
Ransomware are malicious programs that want to prevent/block a user from using the computer. Usually, data is encrypted or all operations are completely blocked.
Knowbe4 provides a ransomware simulation tool that runs through known attack patterns.
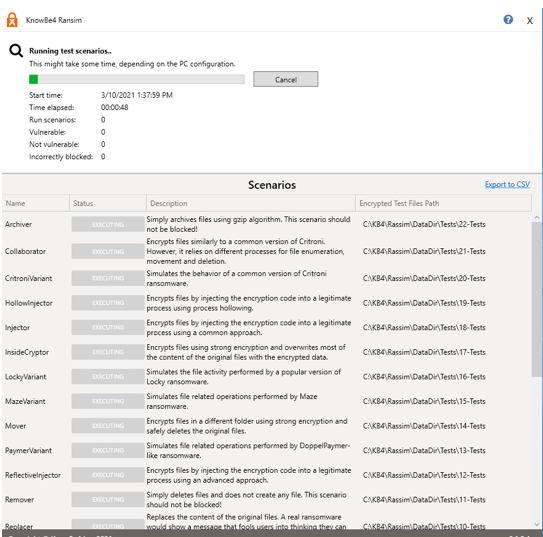
The result looks rather unsatisfactory. However, this is due to the fact that we did practically no configuration of the Defender on this system. Furthermore, we tested specifically for known folders like documents/pictures/videos etc.. However, if the controlled folder access would be configured, most of these attacks would have been unsuccessful. I have done some research and found a video of the PC Security Channel on YouTube, which shows a detailed review of over 50 ransomware types and Defender did pretty well with a pro-active detection score of 98.33%.
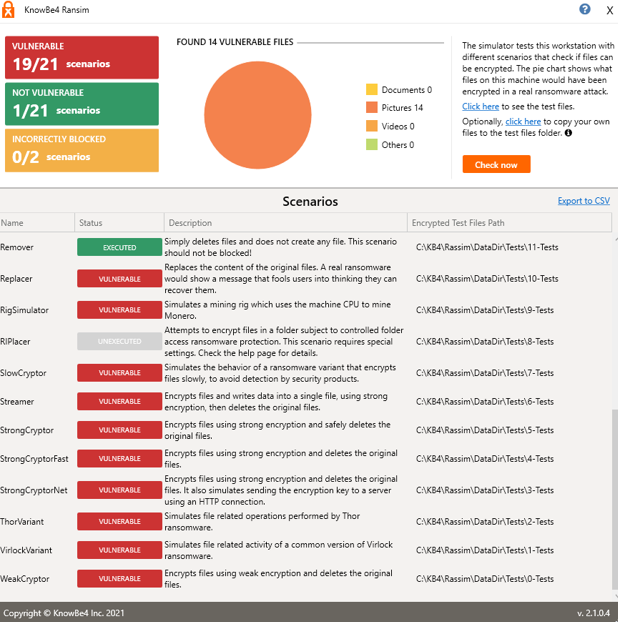
What is also important to remember is that we have a lot of information in the Defender for Endpoint portal about these actions, such as the procedure, affected files or processes and other findings. The investigation was also started automatically.
The complete history is shown here, a corresponding incident is created with the associated clarifications such as detected attack tactics.
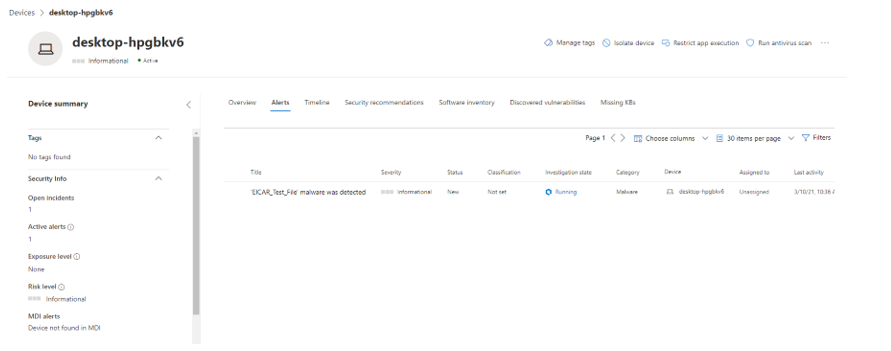
The Microsoft 365 Security Center is another place where relevant incident insights can be found. Microsoft envisions a single-pane-of-glass experience under the Action Center (at the bar on the left), which is a centralized and unified list for remediation & investigation of threats.
In my case a summary where a categorization is made will be shown, for example, 2 MITRE ATT&CK (public database that collects systematic categories on security behavior patterns) attack patterns were detected. It also shows the extent of the threat on devices and users, as well as other rough overviews of specific actions.
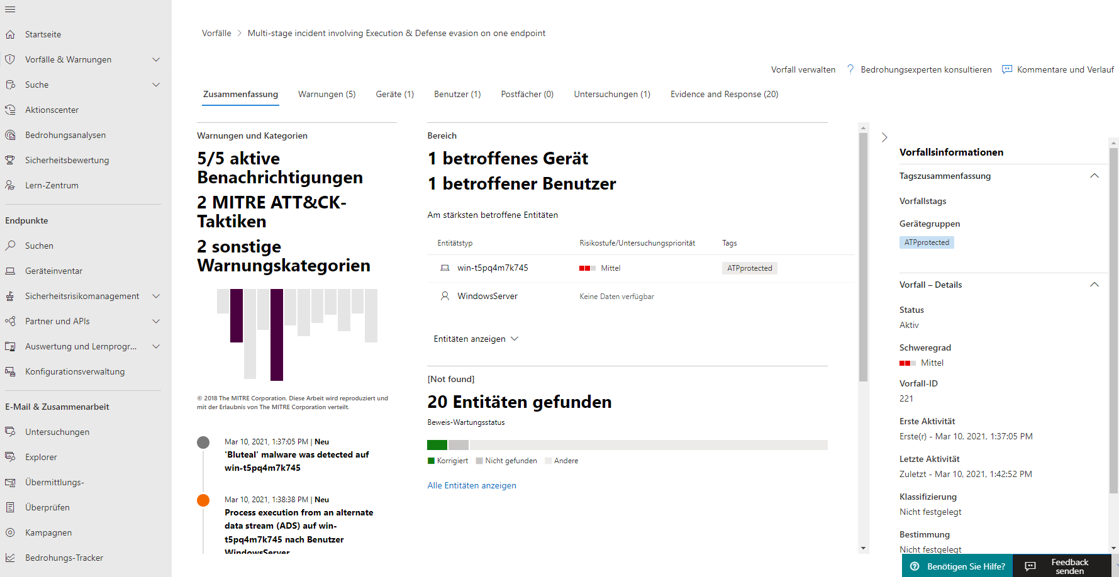
In this example, the graph helps to get more precise information about the test malware. Here, "Bluteal" was detected and prevented directly. The second screenshot goes into more detail about the files used to identify this type of malware. Finally, the Log tab reveals and explains the most important events during the attack.
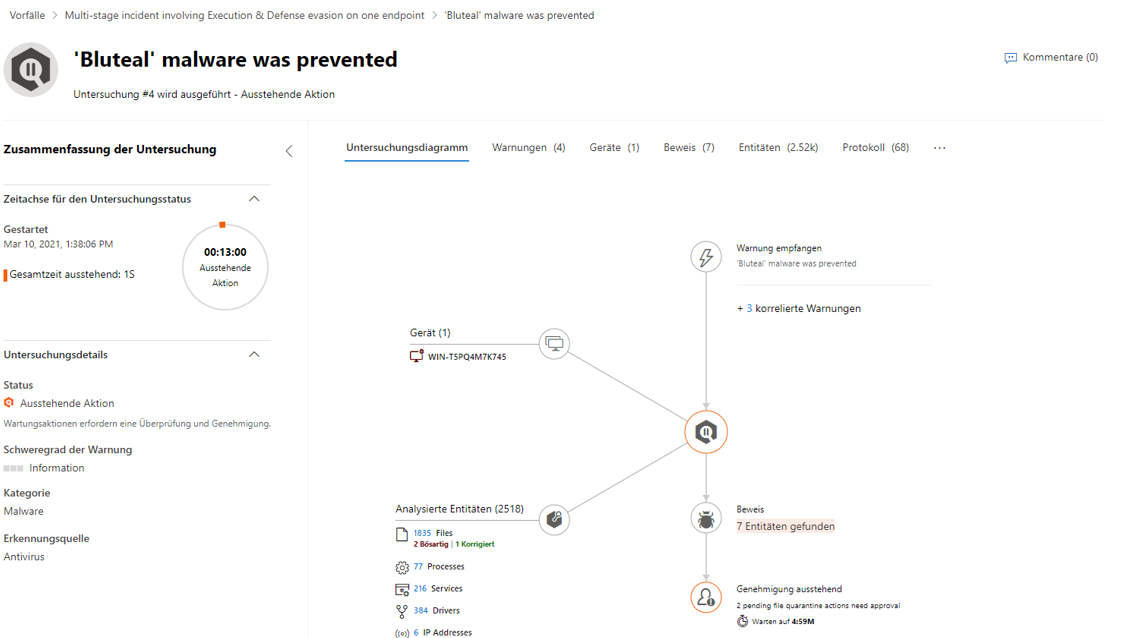
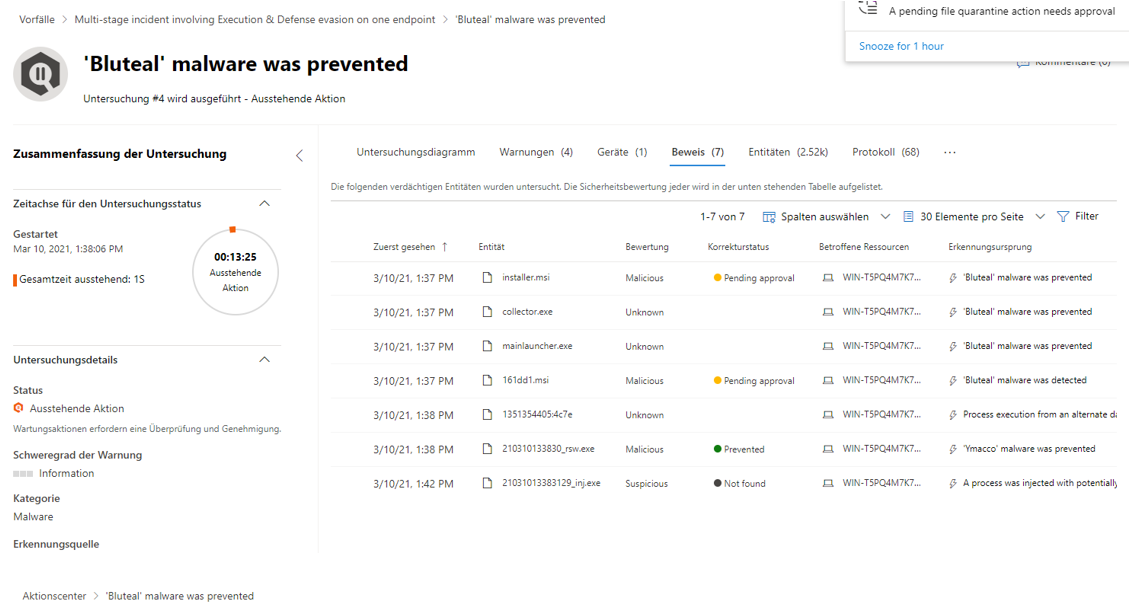
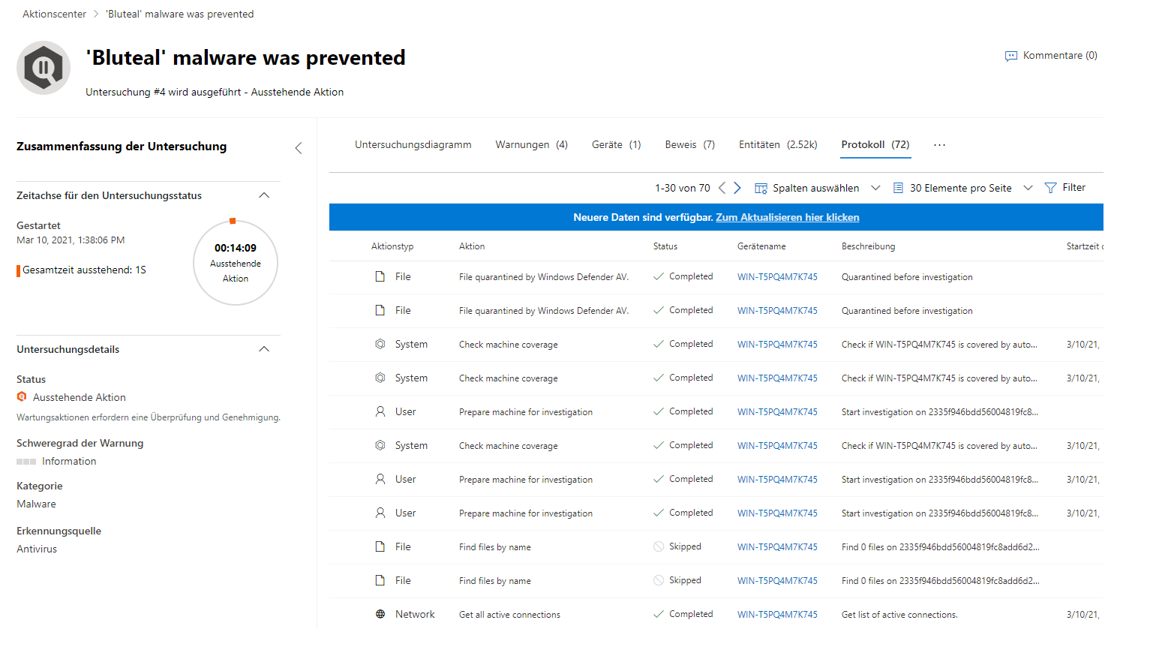
Defender for Endpoint portal
To retrieve information from the DFE portal, there is the main portal https://securitycenter.windows.com. The overall management capabilities and application data are provided here. Furthermore, some of the functionalities can also be found in the Microsoft 365 Security Center at this link: https://security.microsoft.com. An important note is that the Microsoft 365 Security Center also houses the Action Center. This is intended for bringing together all personalized/tenant-specific security-related events from across Microsoft's security products.
Security device information
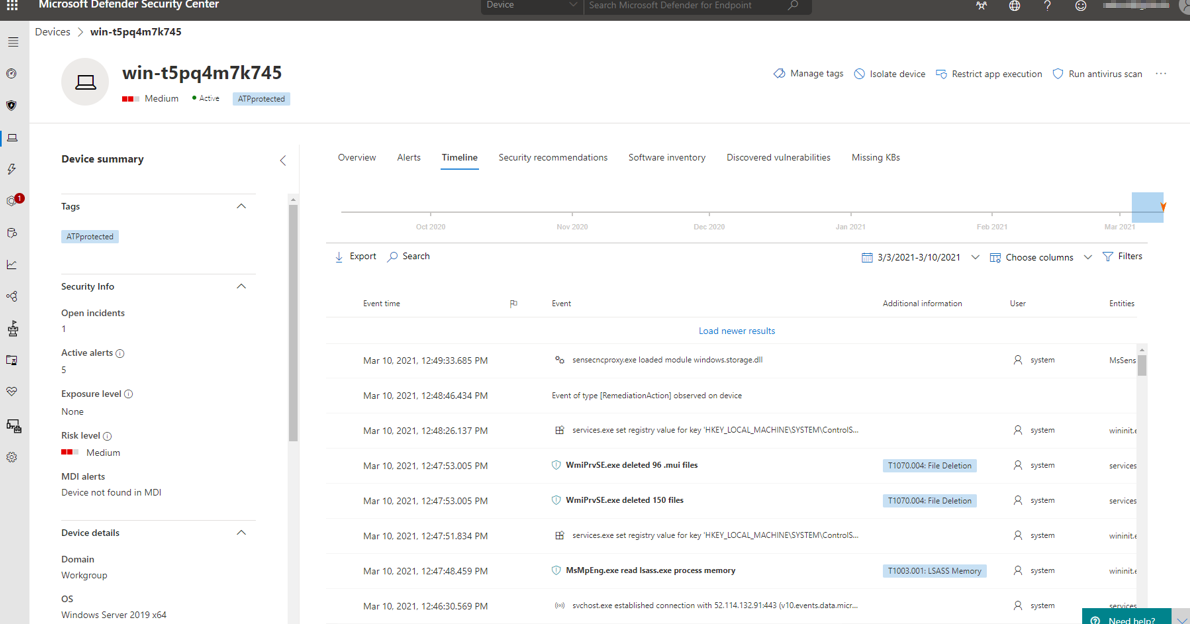
Each individual device with an active DFE sensor provides real-time system data that leads to an individual safety assessment. Subsequently, a risk level is defined, which shows how strongly a device is exposed or whether active alarms are present.
The timeline again shows a chronological sequence of events (e.g. executables, registry entries or file changes) on Windows 10, where events can be registered down to hundredths of a second.
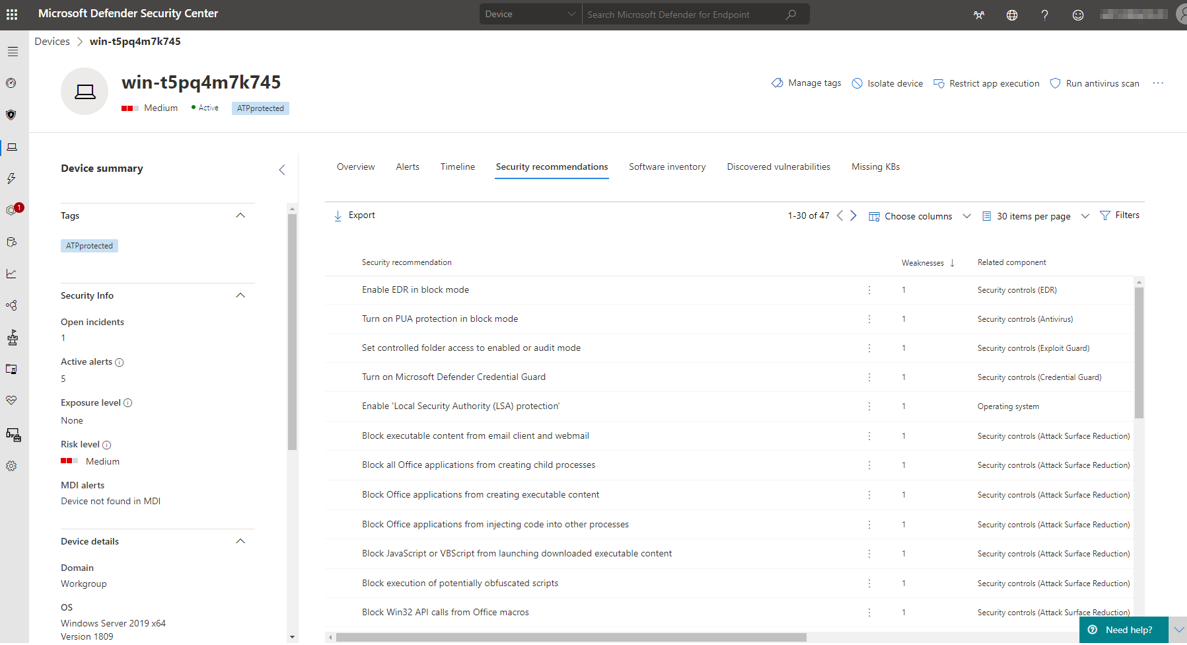
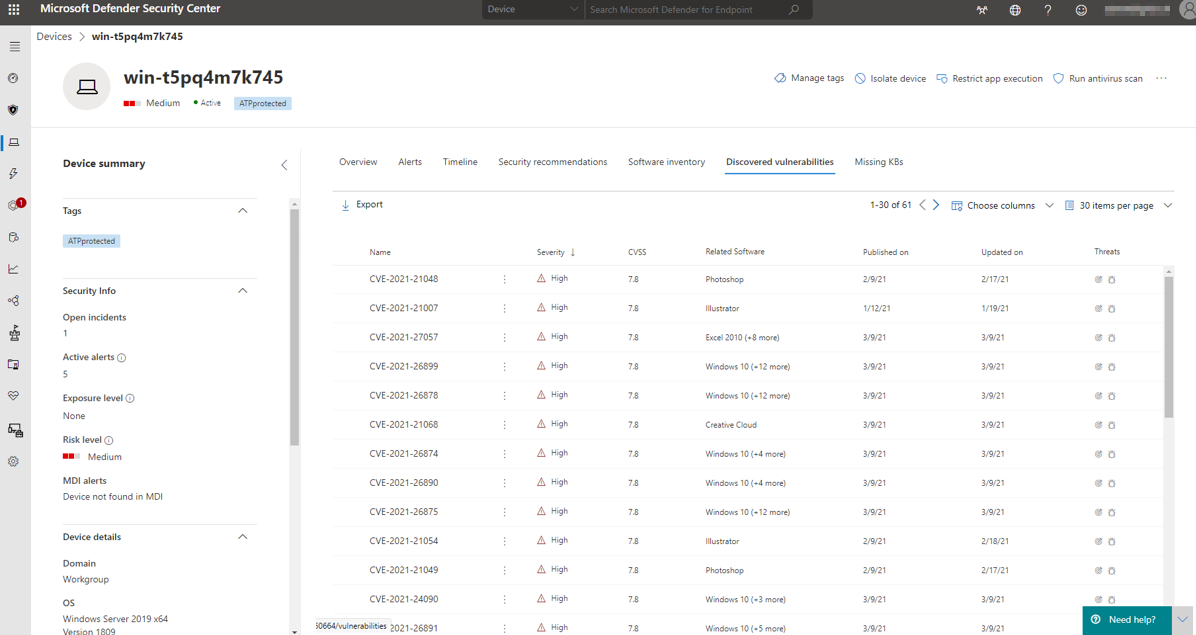
The security recommendations show security-sensitive configuration settings that could be a potential attack surface against attackers. Each recommendation can be measured on the weakness score, this is your reference on how vulnerabale the device is, due to the misconfigured setting.
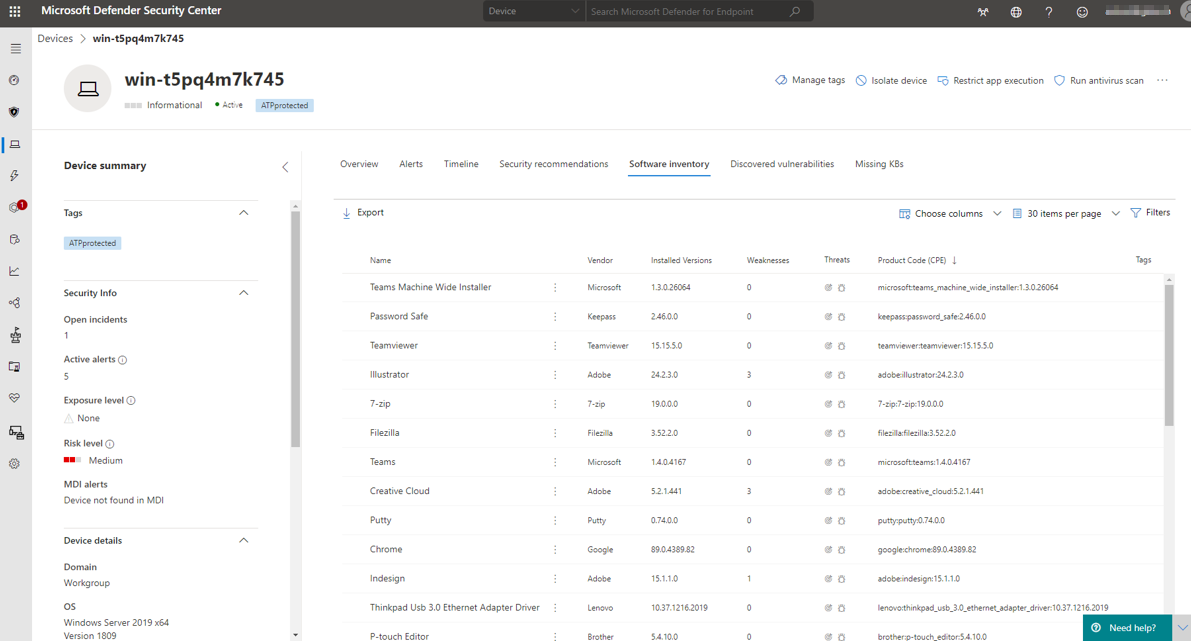
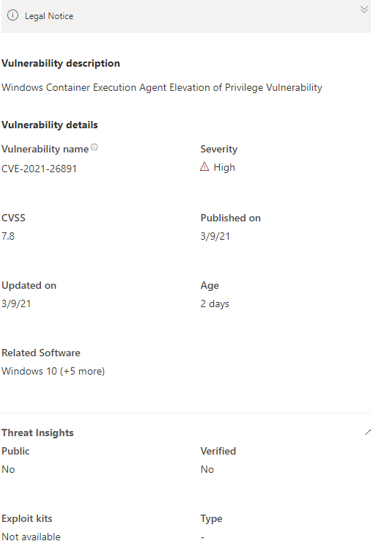
In the software inventory we see a list of installed applications and their possible breaches or threats based on addressed CVE (common vulnerability and exposures) reports. These informations are always up to date, guaranteeing the most secure environment.
Example CVE
Reporting options
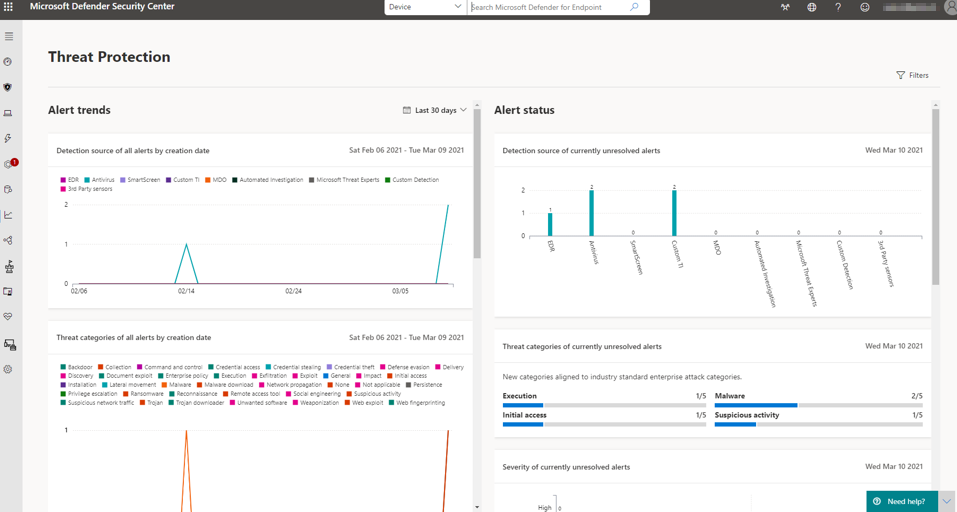
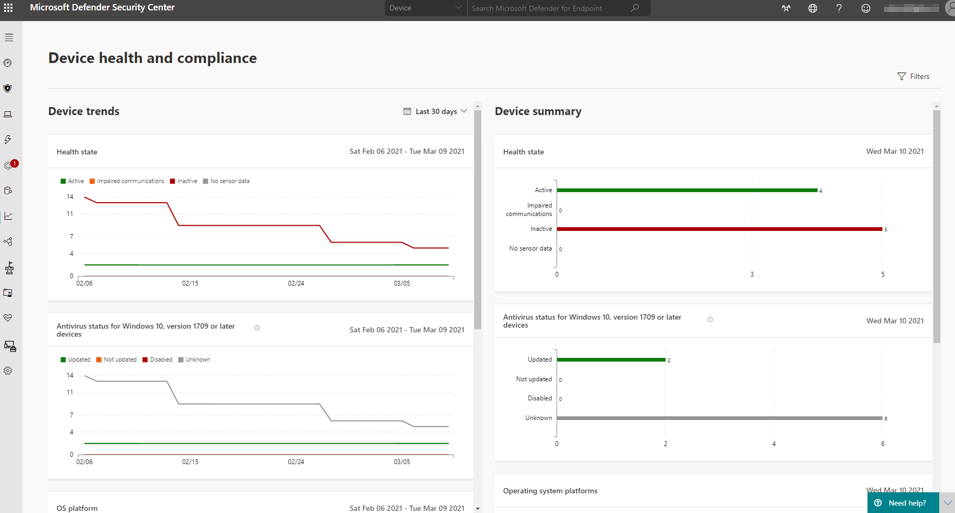
For a security coordinator or similar roles, it is important to have overviews and trends of categorized security-related information and histories from various sources. The diverse capabilities of the Reporting segment in Security Center enters the game here, providing insights into current or past alarms, health conditions, vulnerabilities, threats, reconnaissance, security configurations, and much more.
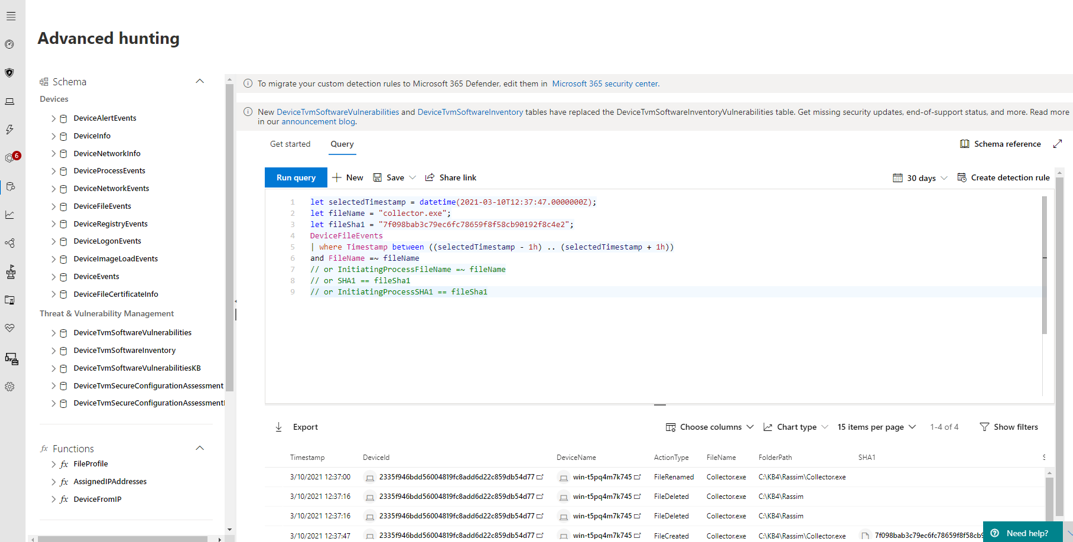
Advanced hunting
Often threats cannot be fully identified from the information displayed. Advanced Hunting relies on Kusto query language, which provides unrestricted insight into the DFE tenant's database. This allows security experts to perform a high-level exploration of the entire security environment.
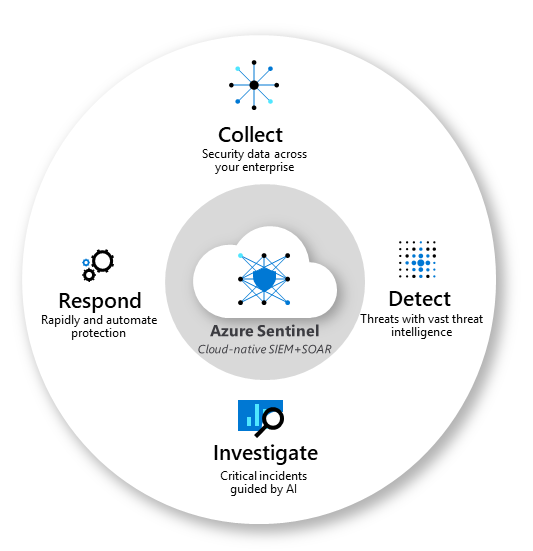
Azure Sentinel - the cloud native SIEM
Microsoft's first-party SIEM & SOAR solution is called Azure Sentinel. This cloud-based intelligent security product provides comprehensive alert detection, threat visibility, proactive search and threat response capabilities across an entire enterprise.
Sentinel is based on Azure Log Analytics Workspace that represents a logical storage unit where massive amounts of data can be processed. The analysis of big data is prioritized in workbooks, which are a graphical template for the collected data to identify further conclusions.
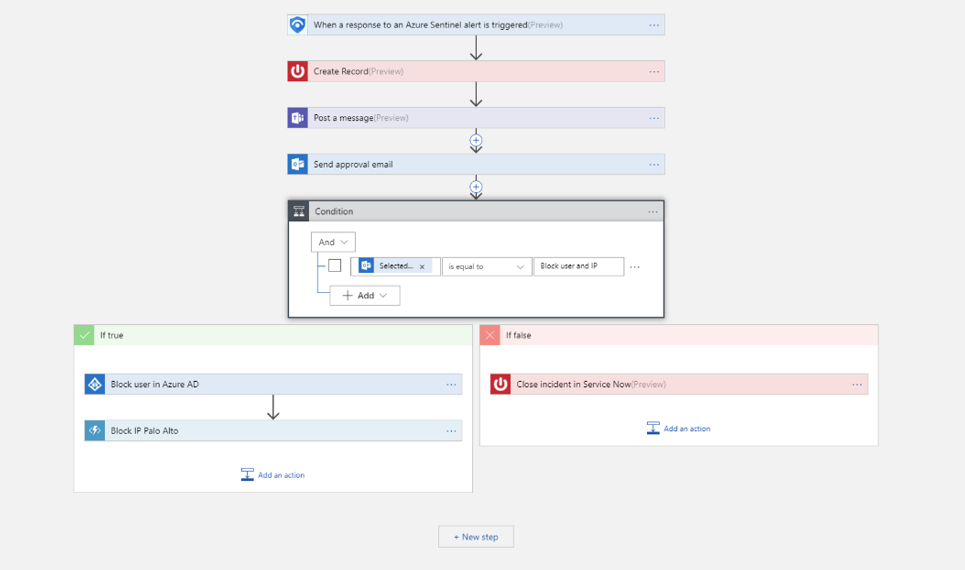
Security automation & orchestration - SOAR
Automation is becoming an increasingly important topic. This is also the case in the area of security, as the mass of versatile tasks can often no longer be handled by employees alone. This competence is offered by Azure Logic Apps, which is all about automation of orchestration tasks based on regulated processes and conditions.
Personal conclusion on the Microsoft Defender
Now let's move on to my personal evaluation and experience rating of Defender, as well as Defender for Endpoint based on the test runs and what I have seen so far.
The majority of malicious code and subsequent actions were detected rapid and correct and prevented where necessary. Thanks to the wide range of security products in Defender, threats were correctly classified and appropriate measures were initiated directly without any noticeable performance impacts. Settings for an administrator are easy to make, or can be left at the default baseline security settings of Microsoft. The warnings for the end user are also adequate. In any case, the evaluation variations and automated investigations and the intelligence of Defender for Endpoint are largely responsible for its success. The cloud management portal is well structured and contains relevant information to all activities helping IT administrators to set the right measures.
In my opinion, Microsoft Defender, together with the cloud, is a powerful and intelligent tool for taking care of attacks and threats during all stages. This is not least due to the distinctive capabilities of the cloud and its interaction with Microsoft products & services.
Thank you for reading until here! I hope you liked this report and learnt some new stuff. If you found this content helpful, I would highly appreciate any type of sharing.
Shoutout to to Sascha, who contributed to this :)
I have already written two blog posts about security in the past. Feel free to take a look to them as well.
Microsoft security concepts
Some more security ramble