Microsoft security concepts
Learn about Microsoft cloud security high-level concepts to secure your organization with Microsoft 365 and Azure built-in products and features. The way to secure your digital assets such as identities, infrastructures, platforms, apps and data.
These are the official Microsoft security sources.
On my blog you can find two security paths about:
Security spheres
Microsoft names the following spheres when talking about enterprise-class security & technology.
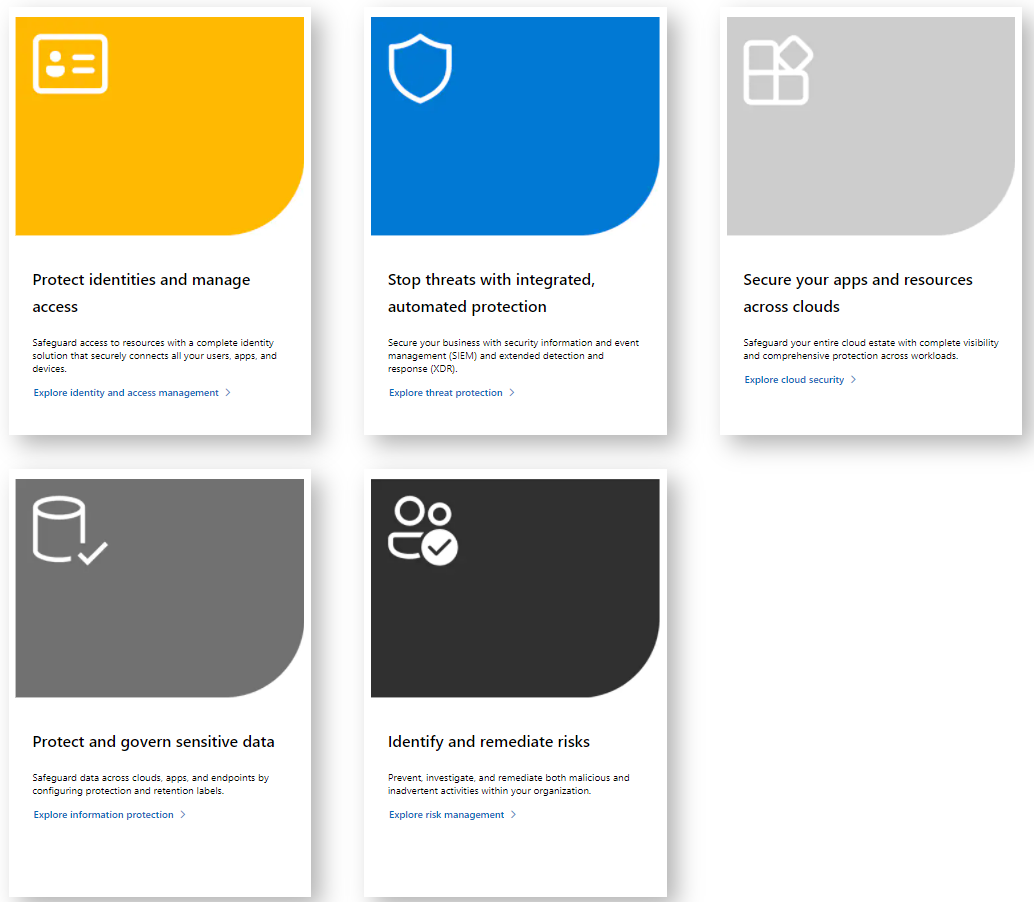
Protect identities and manage access
Identity & Access Management (IAM) is key for every environment, that has its sovereign assets to control interaction between people and resources.
Stop threats with integrated, automated protection
Threat detection, investigation, hunting, response with Extended detection & response (XDR) to protect your assets. Correlation between the products enable high level security - more about security correlation.
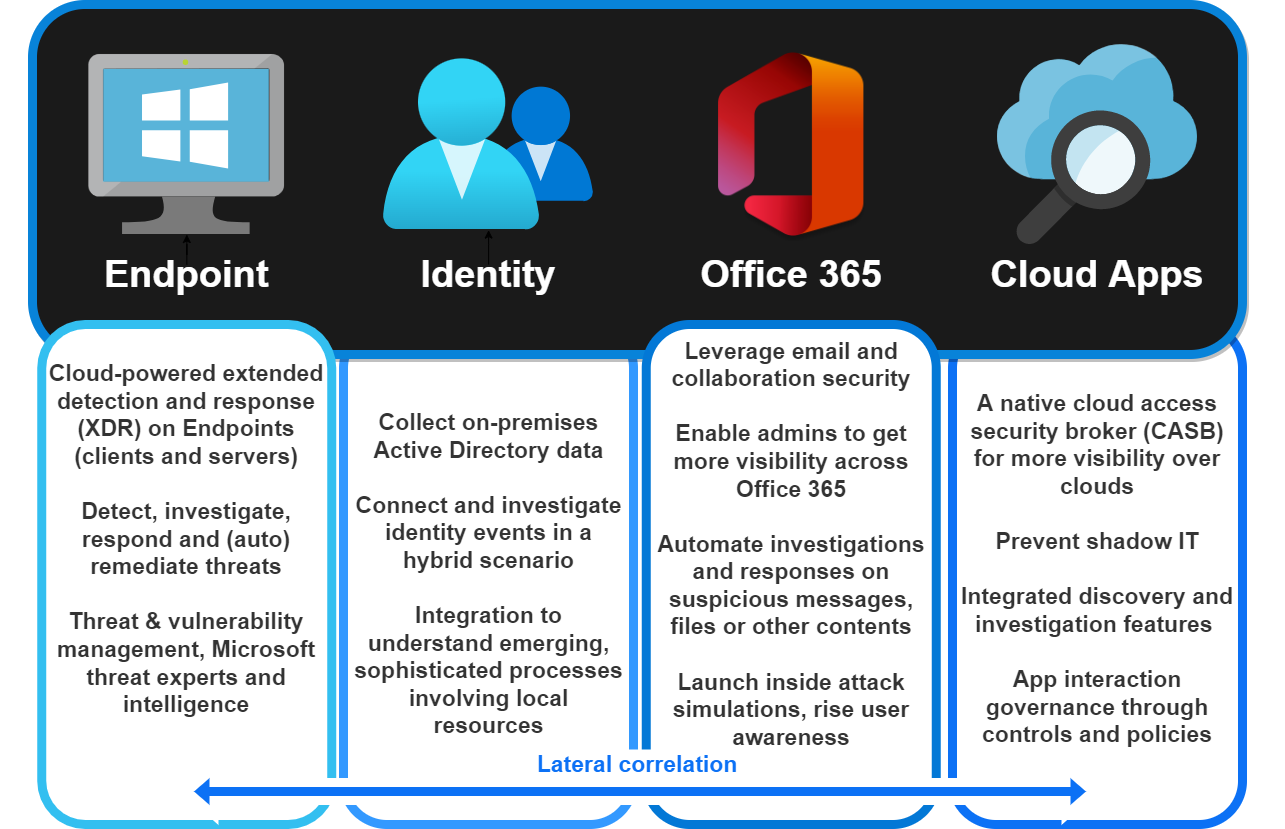
Secure your apps and resources across clouds
Modern applications are found in the cloud. To govern the collaboration of your organization and these, you need a discovery across your tenant. Then you can granularly control with policies.
Protect and govern sensitive data
Compliance, governance are central for information protection. Full authority over your data independent of their location or state at every time. Microsoft compliance
Identify and remediate risks
In an emerging world where adversary technologies and techniques develop just as fast as the legitimate, it is import to keep an overview of what is currently going on in cybersecurity. Identification of potential and direct vulnerabilities or threats can be done with Microsoft Threat Analytics helps to get a better understanding about threats and correlates detected events to your organization.
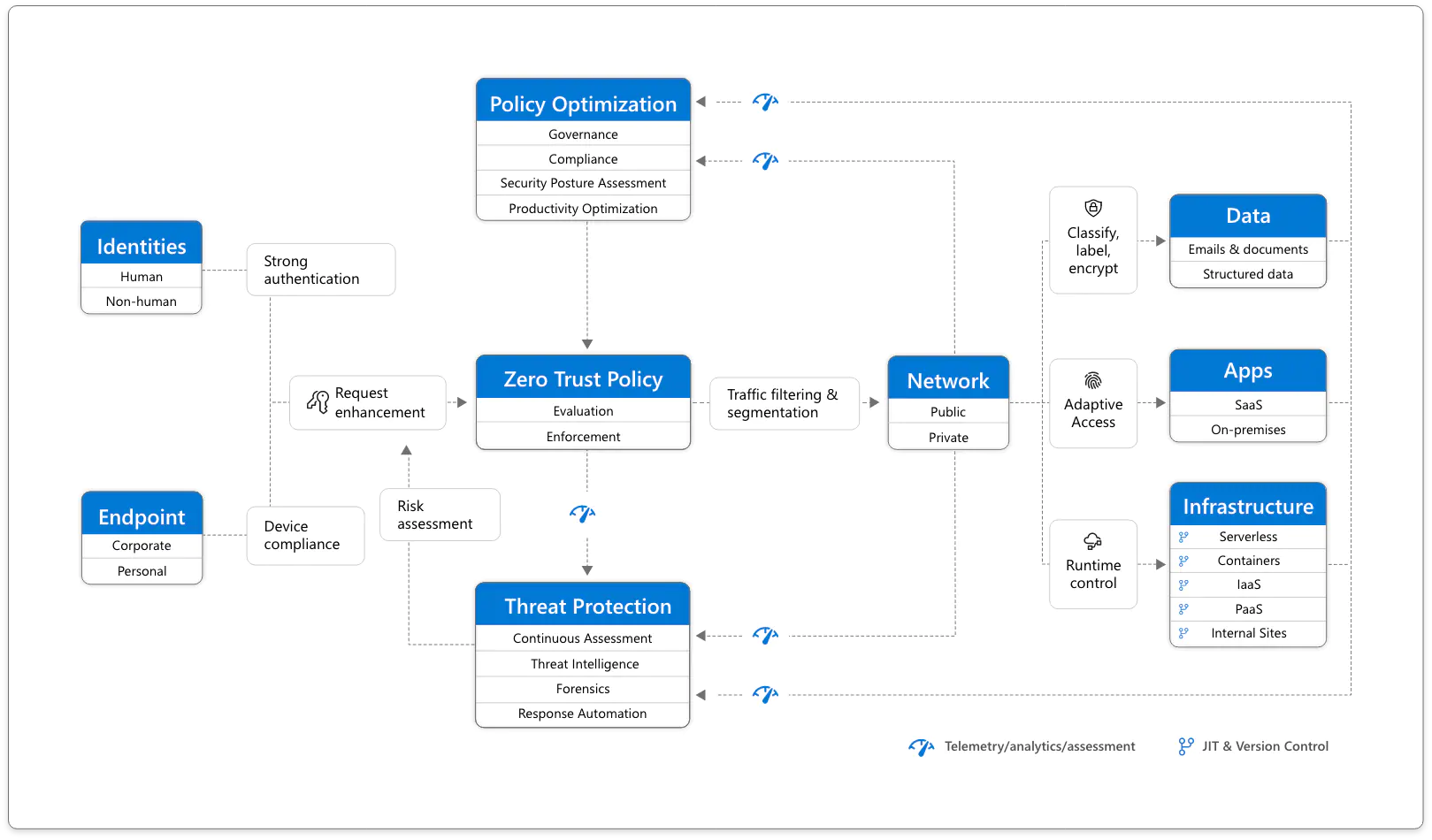
Zero trust
The zero trust strategy is about eliminating trust and treating all interactions the same. It is a perimeterless attempt.
- Verify explicitly, any authentication and authentication processes must be checked against all available information at any time
- Least privileged access, user access should only be granted according to the concepts of just-in-time (only for a defined period of time for the corresponding actions) and just-enough access (dedicated authorizations for the respective action) (JIT/JEA)
- Assume breach, all operations should always be considered as if they were a compromised attempt or attack
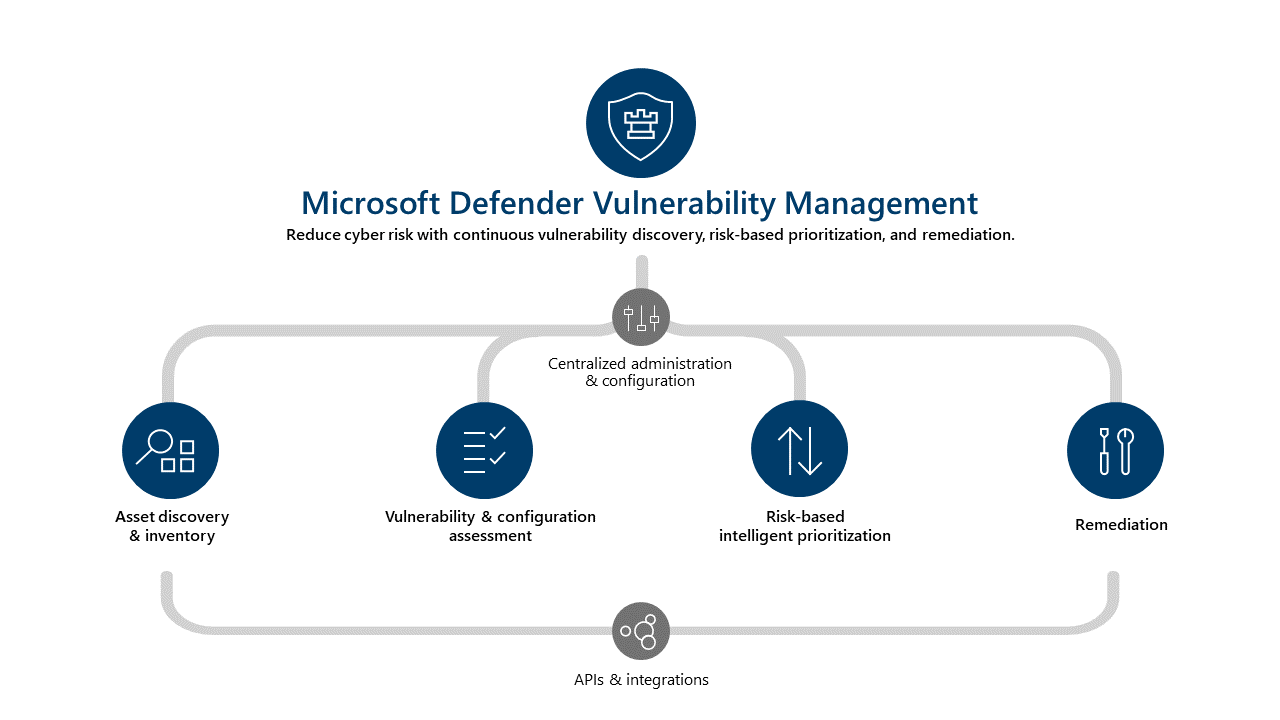
Threat & Vulnerability Management
Versatile devices and apps offer versatile attack surfaces. Microsoft Defender Vulnerability Managment forms the corresponding solution to this concern and delivers high- to low-level information about all types threats and vulnerabilities, shows affected assets, supports in priorization and mitigation options.
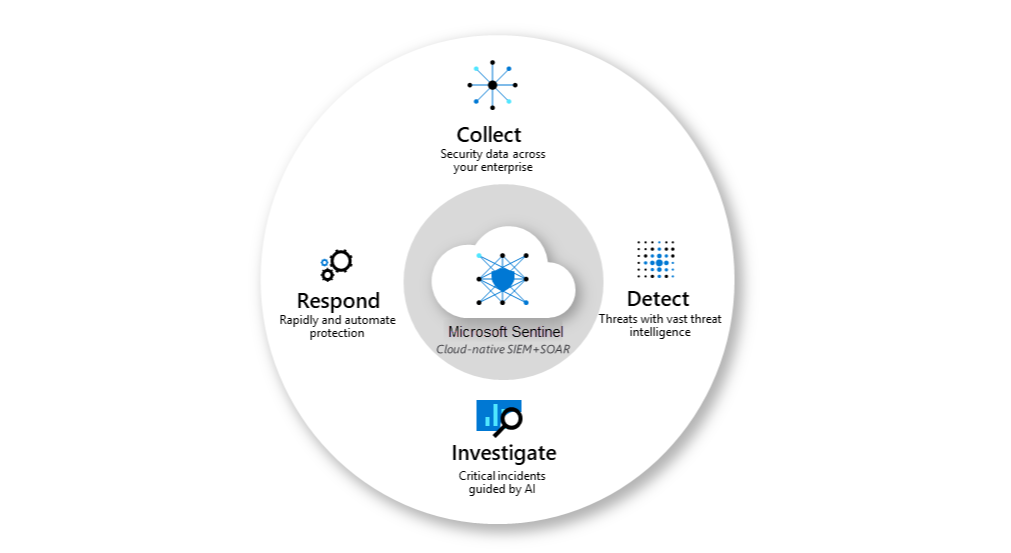
SIEM and SOAR
SIEM and SOAR associate in IT security event aggreagation, management and response.
Security Information Event Management (SIEM)
Security Information Event Management relates to event management based on information on a security landscape. It includes all basic security operations. Delivered through Microsoft Sentinel.
Security Orchestration, Automation and Response (SOAR)
Security Orchestration, Automation and Response is the evolutionized version of SIEM, that has its focus on security task (mainframe) orchestration and automation response and mitigation to drive security operations to the next level.
Licensing
- E3 Security hosts basic security products that provide a foundational protection, though they often lack of sophisticated investigation or reporting options
- E5 Security is the full package for mainly cloud-only oriented customers that want the whole and best security experience throughout all products
More information are available in my Microsoft 365 license guide post.
For a detailed and up to date overviews, visit: M365Maps

Security powered by Oceanleaf:


More helpful Microsoft resources
| Resource site | Contents |
|---|---|
| Security 101 | cybersecurity fundamentals |
| Security Insider | Explore the latest cybersecurity insights and updates |
| Digital Defense Report | Regular report about the cybersecurity landscape at scale |
| Security Response Center (MSRC) | Front line of security operation and response |
| Security blog | Articles on different topics |
| Security events | Overview of scheduled security events |
| Tech community | Community platform |
| Security documentation | Product and feature docs and sources |
| Learn | Learning paths and certifications |
| Trust center | Find information about security, compliance and privacy |
| Service Trust Portal | Audit reports of Microsoft services |