My take on the future app deployment with Intune
Introduction
There is currently a lot going on in the app deployment of Windows management with Intune. The new Microsoft Store came up, together with an integration to Intune. Simultaneously the Windows Packager Manager (winget) starts to find more establishment with these topics.
This is a write-up to my experience and some advice I can give, yet. If you have any inputs, please let me know.
Summarized notes
- Microsoft Store for Business is deprecated by Q1 2023
- The new Microsoft Store is the successor that is a general store experience for consumer and enterprises
- With this topic the integration with winget came up, but these are generally separate topics
- The new Store experience in Intune leverages winget to install apps on endpoints
- Winget is the client interface to the Windows Package Manager service based on command line
- Winget can install apps from multiple sources, including the public repository the new Microsoft Store, private app repositories are also possible
- This is the public repository from winget where vendors and publishers as well as the community can sumbit packages and manifests
- End-users may install winget apps through the command line on their own when the app comes through the Microsoft Store or is installed in the user profile only (essentially when it wouldn't trigger an UAC admin prompt)
- This is the official docs on Store group policies > you should only set the Store to private (to prevent end user installations from the store), but not block it completely, as this would also stop app updates from the store
- If you only want to disable the winget package source, you should try to disable the EnableDefaultSource setting thorugh OMA-URI - this will also have an impact on the agentexecutor.exe which is leveraged by Intune
-> The better way to get app execution under control, is to consider AppLocker - Limitations: (Micorsoft is already working on it)
- New Store apps in Intune can't be installed during the enrollment status page (ESP)
- UWP apps are not supported in the device provisioning (context)
- Scope tags do not work on the new Store apps (from my experience)
- App updating is not covered when adding an app through the new Store integration
- Winget command line tool is supported on Win 10 1709 or later - the first run comes up with a terms of use
- Here you can also find all winget packages
Winget
Here are some basics with winget to understand its essential functionality.
Basics
| Command | Use |
|---|---|
| winget | Show all commands |
| winget -v | Show current installed winget version |
| winget source | Show all sources for winget Default: -winget / public repo -msstore / new Microsoft Store |
| winget settings | Reference to the settings - default settings: https://aka.ms/winget-settings |

Install, upgrade and uninstall app
| Command | Use | More |
|---|---|---|
| winget search app name | Find an app from the sources | |
| winget list | List all installed apps on the local system | Supports search for a package: winget list app name |
| winget install app identifier | Install an app | |
| winget upgrade app identifier | Lookup for a new version of the app and upgrade to the new version | Can upgrade all at once with: winget upgrade --all |
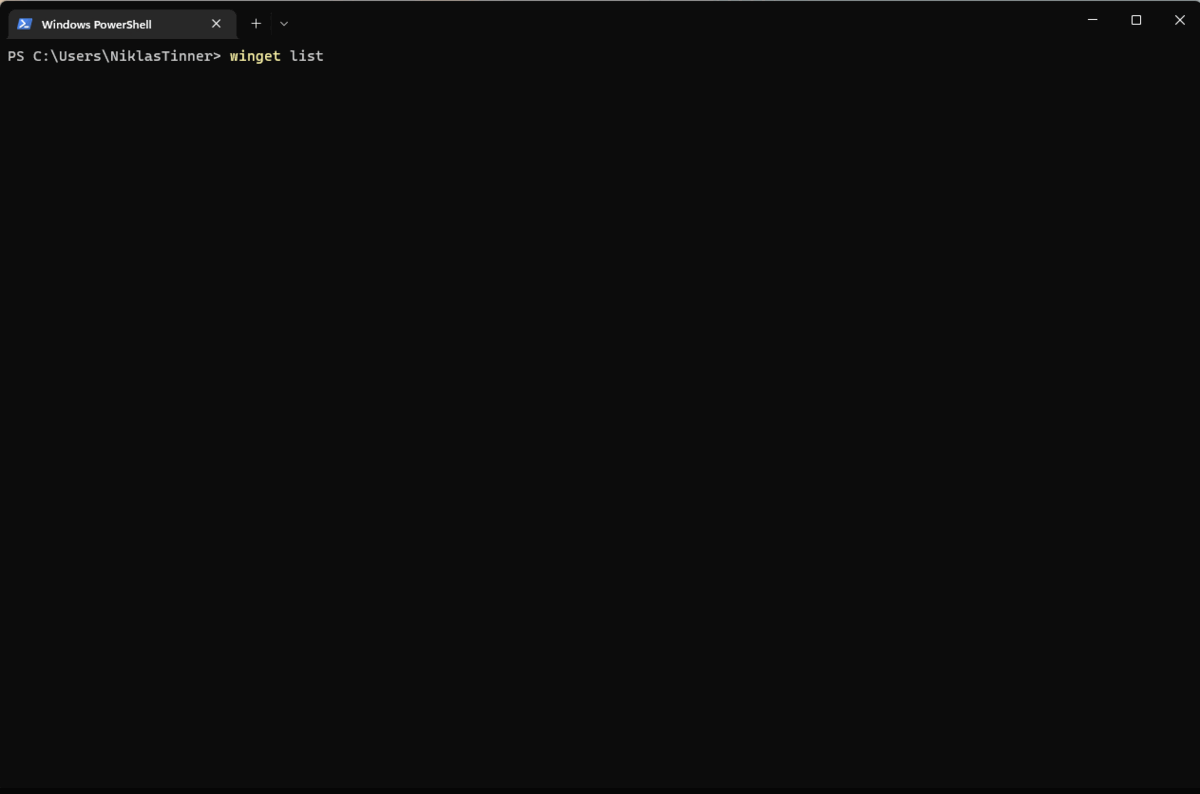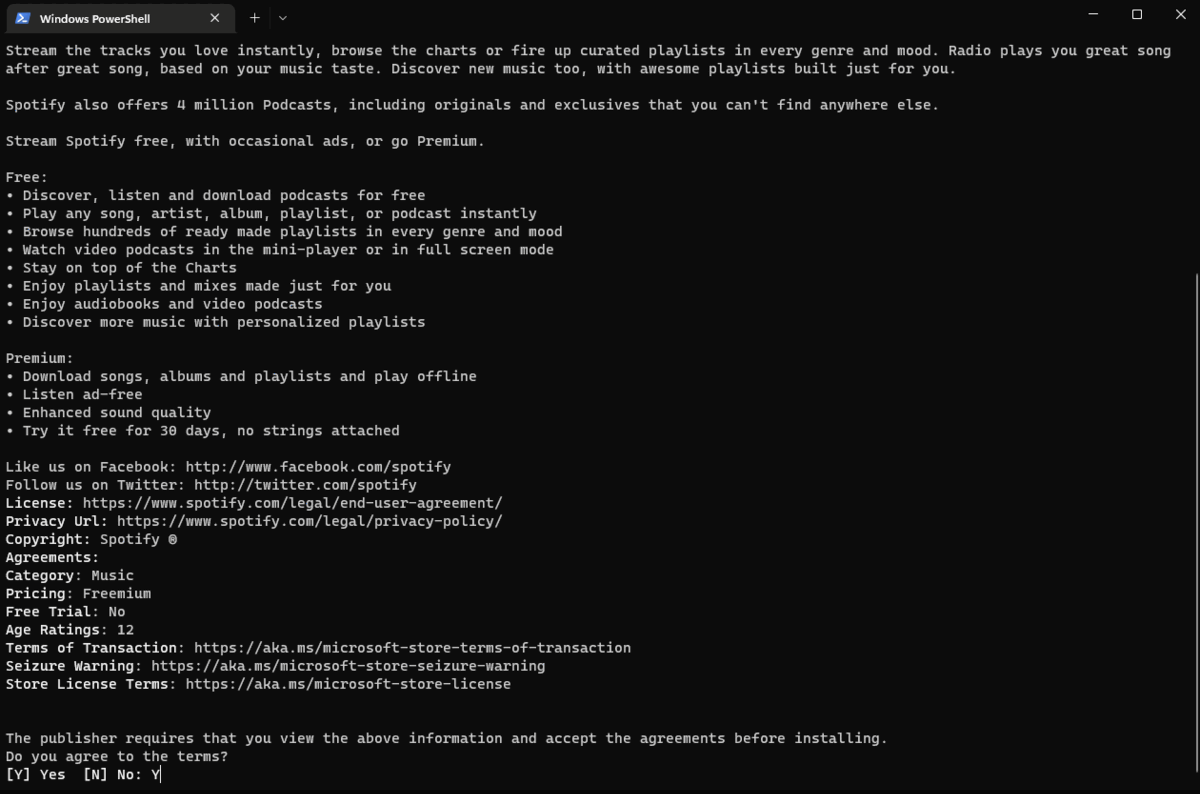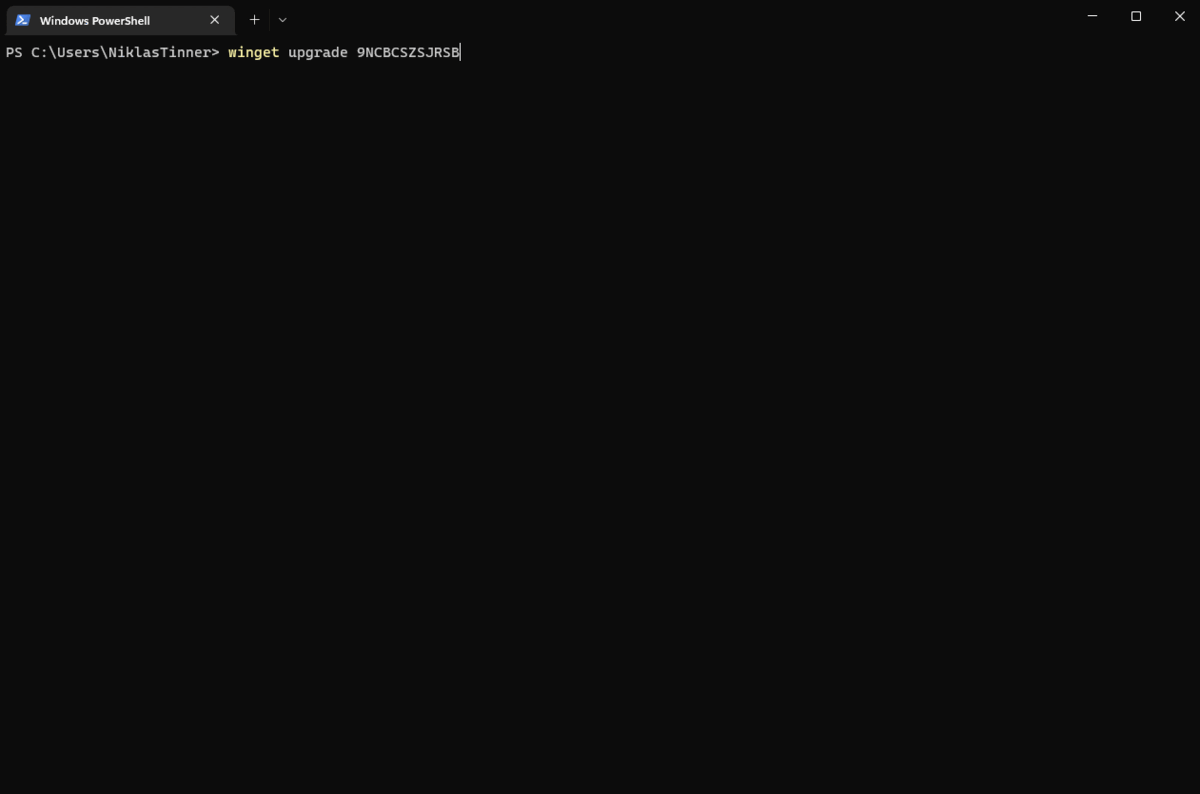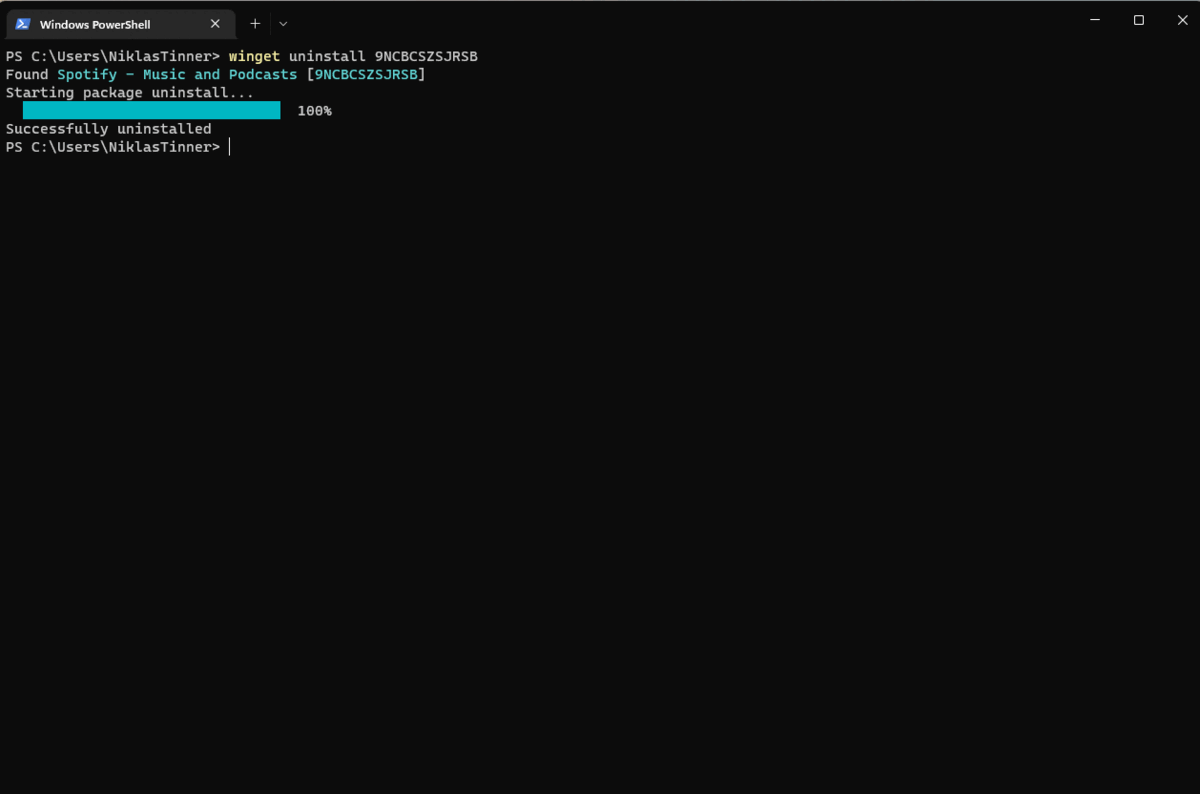
| winget uninstall app identifier | Uninstall an app |
App types
In a modern world we encounter the following app types in Intune and Windows:
- Win32 - custom uploaded apps to Intune (with Content Prep Tool)
- Microsoft Store app (new) -> in the background winget is always used
- Universal Windows Platform (UWP) - Store apps
- Win32 (currently in preview), third party vendors and publishers and the community that add their apps to the Microsoft Store
Logs
Log files are created by default when executing commands under:
%LOCALAPPDATA%\Packages\Microsoft.DesktopAppInstaller_8wekyb3d8bbwe\LocalState\DiagOutputDirIntune
Add new Store apps
Adding new Store apps to Intune is straightforward:
-
Go to Intune>Apps>Add
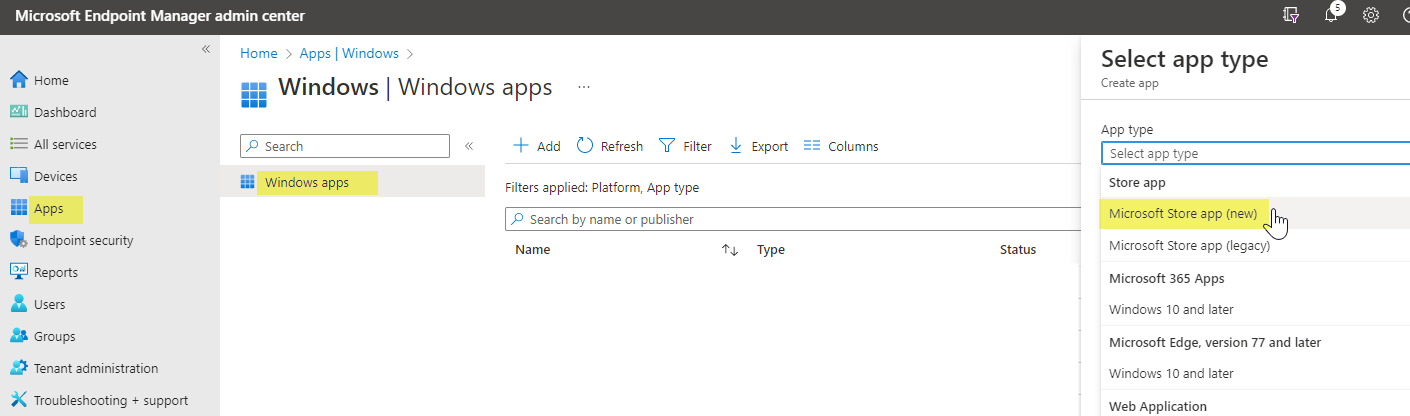
-
Search for the app by name
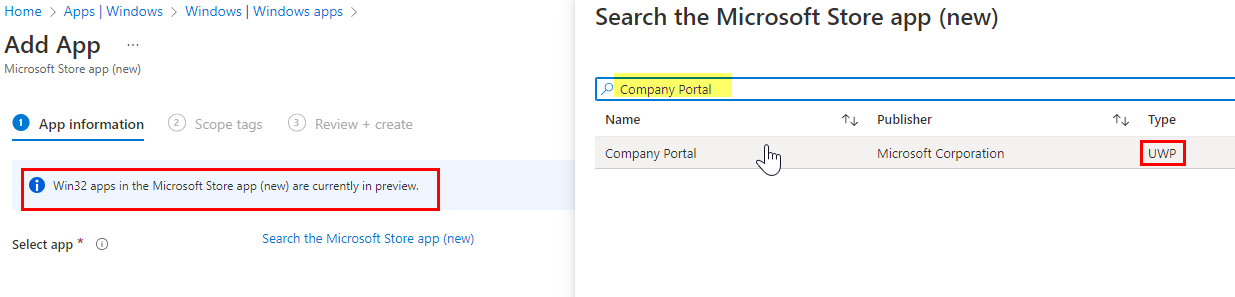
If you can't find the app by name, you can search for the packageIdentifier. For this, visit the Microsoft Store Online and search for your app. In the URL you can find the ID, that you can then use to also search apps in Intune.

This equals to the app in Intune:
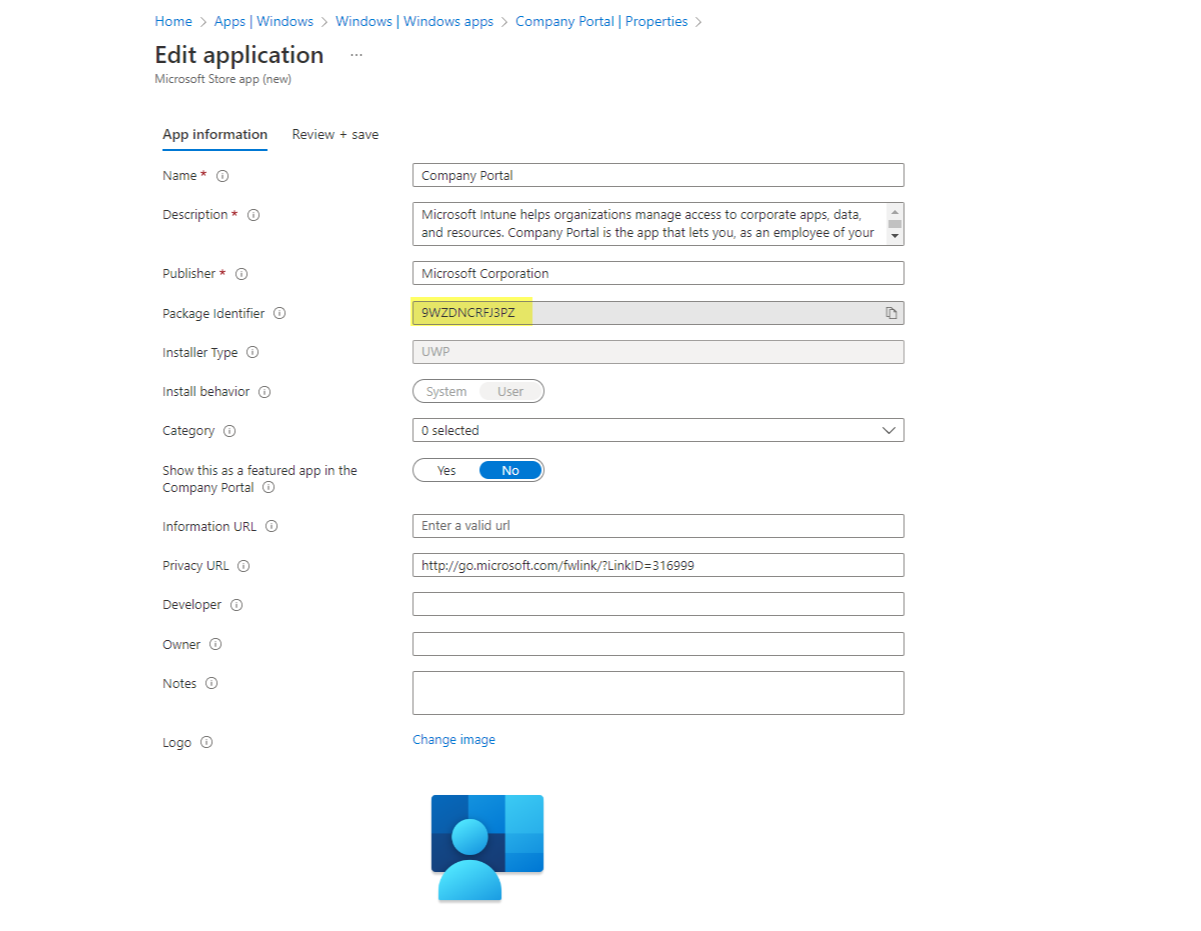
Hint: here you can find a repository full of app icons.
Transition in Intune
You may ask now, how to make a transition to the new Store and removing the old Store for Business apps from Intune. You need to know:
- The new Store is the future for app deployment, but at this time there might be some bugs or features are not fully developed
- Package quality and reliability from third parties is unkown
- Updating is not covered, when you only add the app (Proactive remediation could regularly run "winget upgrade --all")
My fellow mate Nicola Suter provided some Graph commands to create an assignment report including the app packageIdentifier. (They do not change anything)
Connect to Graph with the right permission scopes. (Verify that the Microsoft.Graph module is installed before)
Connect-Mggraph -Scopes "DeviceManagementApps.Read.All"Get all assigned Microsoft Store for Business apps.
$apps = Get-MgDeviceAppMgtMobileApp -Filter "isOf('microsoft.graph.microsoftStoreForBusinessApp')" -ExpandProperty "assignments" -All | Where-Object {$_.Assignments.Count -gt 0}Extract the packageIdentifier (which is used to uniquely identify an app).
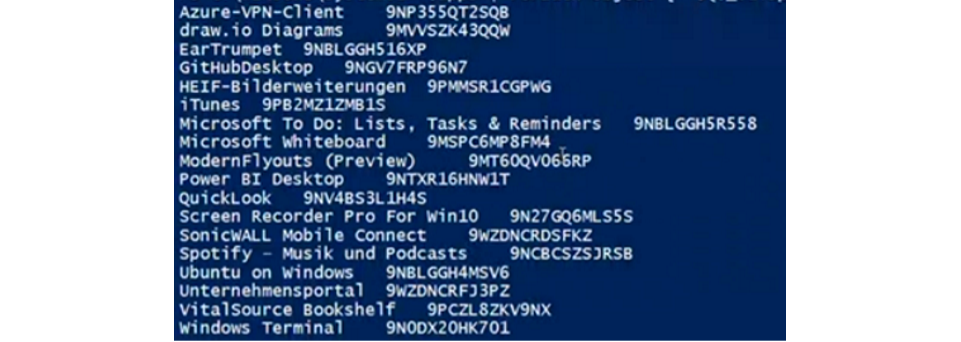
$apps | ForEach-Object { "$($_.displayname) `t" + $_.AdditionalProperties["productKey"].Split("/")[0]}Now take a look at the variable.
$appsThis should look like: (left side = app name, right side = packageIdentifier)
Other sources


