Privileged Identity Management (PIM) concept + setup
Introduction
Privileged Identity Management (PIM) is no longer a hidden gem in the Microsoft cloud ecosystem. It was originally released almost 10 years ago! I know there is already a lot of great content out there on it, but this blog post will be my personal summary.
What to expect 🎯
- What is PIM?
- Why is Privileged Identity relevant?
- Prerequisites
- Concept
- How to set up
- Bonus
- Enable PIM for groups for roles outside of Microsoft Entra
- Identity Governance
- Integrate with Administrative Units
- Integrate with Microsoft Sentinel
- Change tracking
What is PIM? 🦸
Microsoft Privileged Identity Management (PIM) is an Entra ID Premium Plan 2 feature to secure elevated rights, include approval processes and manage admin roles just-in-time and with just-enough access - based on Zero Trust. This feature is only relevant for administrators and only needs to be licensed for them.
With PIM you can:
- Ensure that only the right staff has access to the right permissions in the right timeframe
- Include approval processes to have a dual control system before permissions are granted
- Apply monitoring & reports to elevation, as well as require more details on why elevation was necessary
- My take: The P in PIM stands for psychological. It is a system to rethink the privileged tasks you want to perform and requires to provide a justification and select exactly the right permission set. (Which can also be a challenge 😉)
Why is Privileged Identity relevant?
Privileged Identities are personas with permissions to do changes on a system that affect multiple entities or have a critical (business) impact. In the Microsoft cloud sphere, this could be anything from locking a user, wiping devices, adding or removing third-party apps, managing data (SharePoint, OneDrive) or altering Teams. It is basically superpower 🦸
You see that those Privileged Identities should be well protected, which doesn't only include PIM as a leveraged product, but also to apply other restrictions like MFA, Conditional Access, proper secret storage and trust to parties to guarantee defense in depth.
Prerequisites
Before you enable PIM in your tenant, you should verify that all users who use PIM have an Entra ID Premium Plan 2 license assigned. To configure PIM you need to be a Global Administrator or Privileged Role Admin.
Concept 📝
Role sources
Roles and permissions in Azure and Microsoft 365 can originate from different sources:
- Entra ID: Roles for administering Entra and Microsoft 365 and related products, compatible with PIM
- Intune: Roles specific to endpoint management, by default not compatible with PIM (PIM-enabled groups would need to be used here)
- Defender permissions: Specific roles in Defender XDR / Security Center
- Exchange admin roles: Specific roles in Exchange
- Azure IAM: Roles for Azure resources, separate from PIM
- Purview roles & scopes: Roles in Purview / Compliance
Assignment types
Not all roles are assigned the same way, there are two types:
- Eligible: Role can be activated for a user via PIM for a specific period of time
- Active: Role is static and permanently active for a user
Roles table
When I work with customers, I always recommend to use a roles table to define clearly who has access (permanent or through PIM) to which roles and thereby has which responsibilities. This is how it looks like:
| Role |
Recommended assignment type | Description | Recommended audience |
|---|---|---|---|
| Global Admin | PIM | Can manipulate all aspects of the tenant. | Dedicated admin accounts, except for the Breaking Glass Admin. |
| Global Reader | Static | Can read all aspects of the tenant but cannot manipulate them. | All IT engineers |
| Application Admin | PIM | Can modify Enterprise Apps and App Registrations. | Developer, engineers |
| Intune Admin | PIM | Can configure all aspects of Intune. | Intune Admins |
| User Admin | PIM | Can manipulate user aspects, without authentication methods. | Helpdesk |
| Security Admin | PIM | Can configure security in Defender XDR and Intune endpoint security and Entra settings. | Security Engineers (also consider Defender RBAC) |
| Compliance Admin | PIM | Can manipulate aspects in Purview. | Compliance Officers |
| Authentication Admin | PIM | Can edit security info/authentication methods from non-admins. | Helpdesk |
| Exchange Admin | PIM | Can modify all aspects of Exchange Online. | Exchange Engineers |
| Teams Admin | PIM | Can modify all aspects of Teams. | Teams Admins |
| SharePoint Admin | PIM | Can modify all aspects of SharePoint, inclusive site content. | SharePoint Admins |
| Billing Admin | Static | Can purchase and assign licenses. |
Setup 🛠️
Before you start
The first thing I always do when I get access to any tenant, is to check out the current role assignment. Sort it based on the assignments and get yourself an overview of how the roles are currently distributed. Review them and use it as a starting point: in Entra > Roles
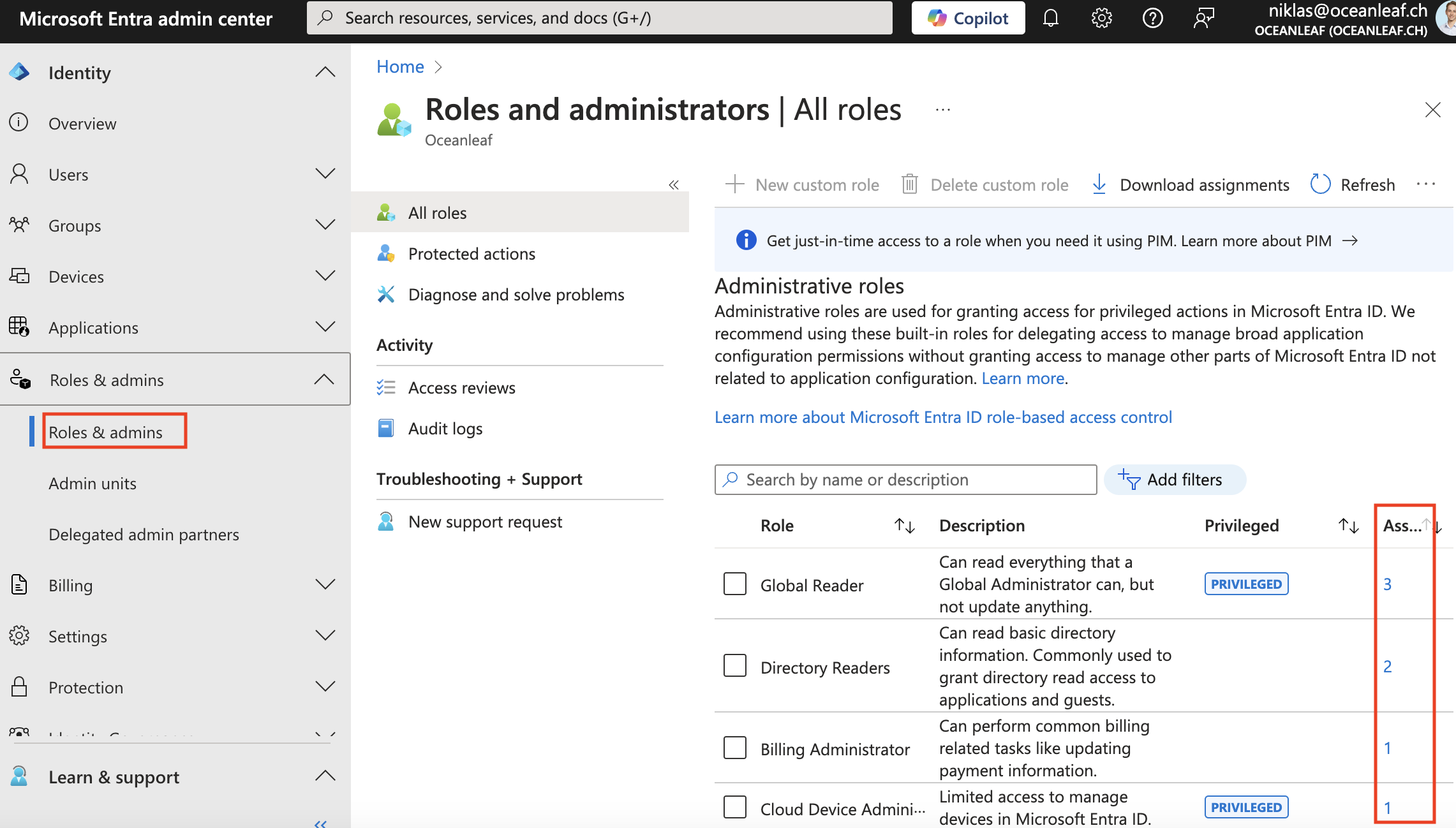
PIM roles
To start configure PIM, go to Identity Governance > Privileged Identity Management > Roles. Assign the roles to admins according to your individual concept roles table from above.
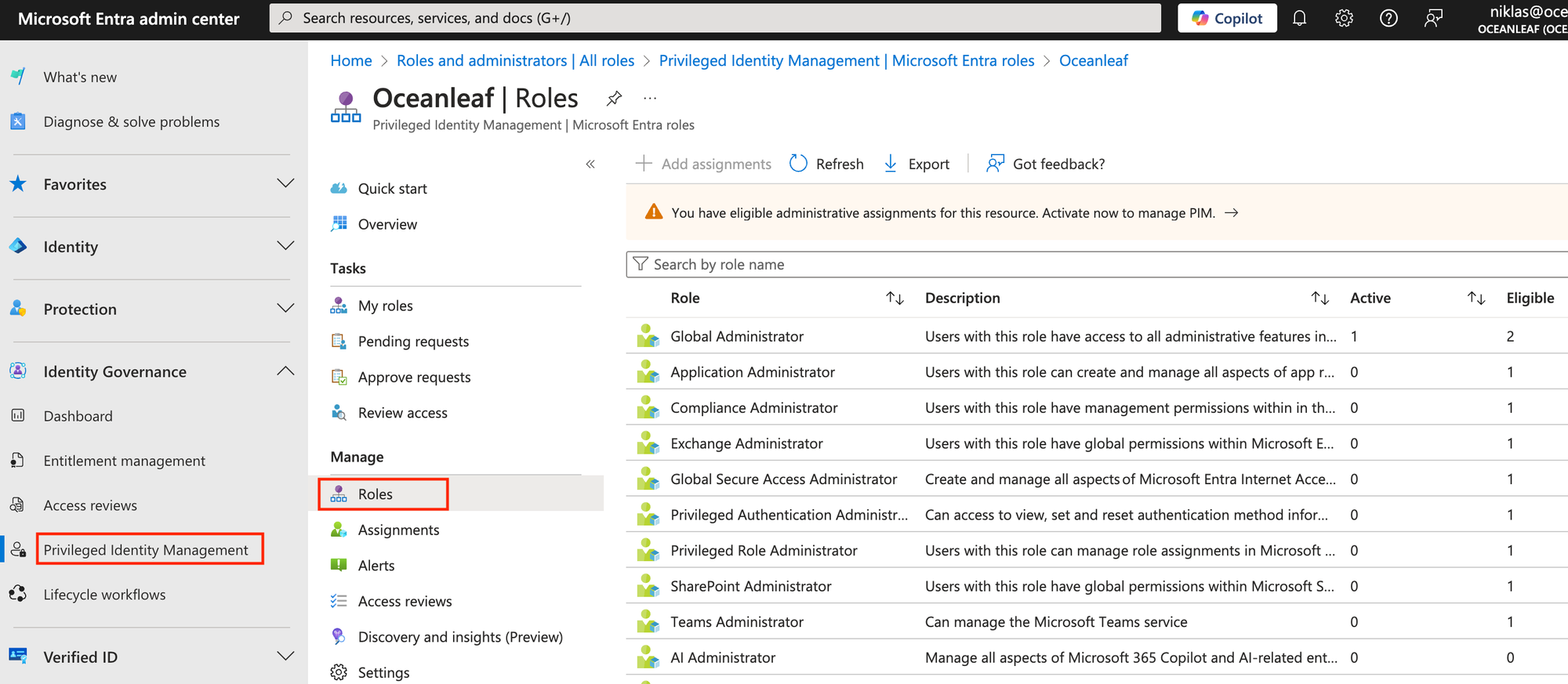
Roles configuration
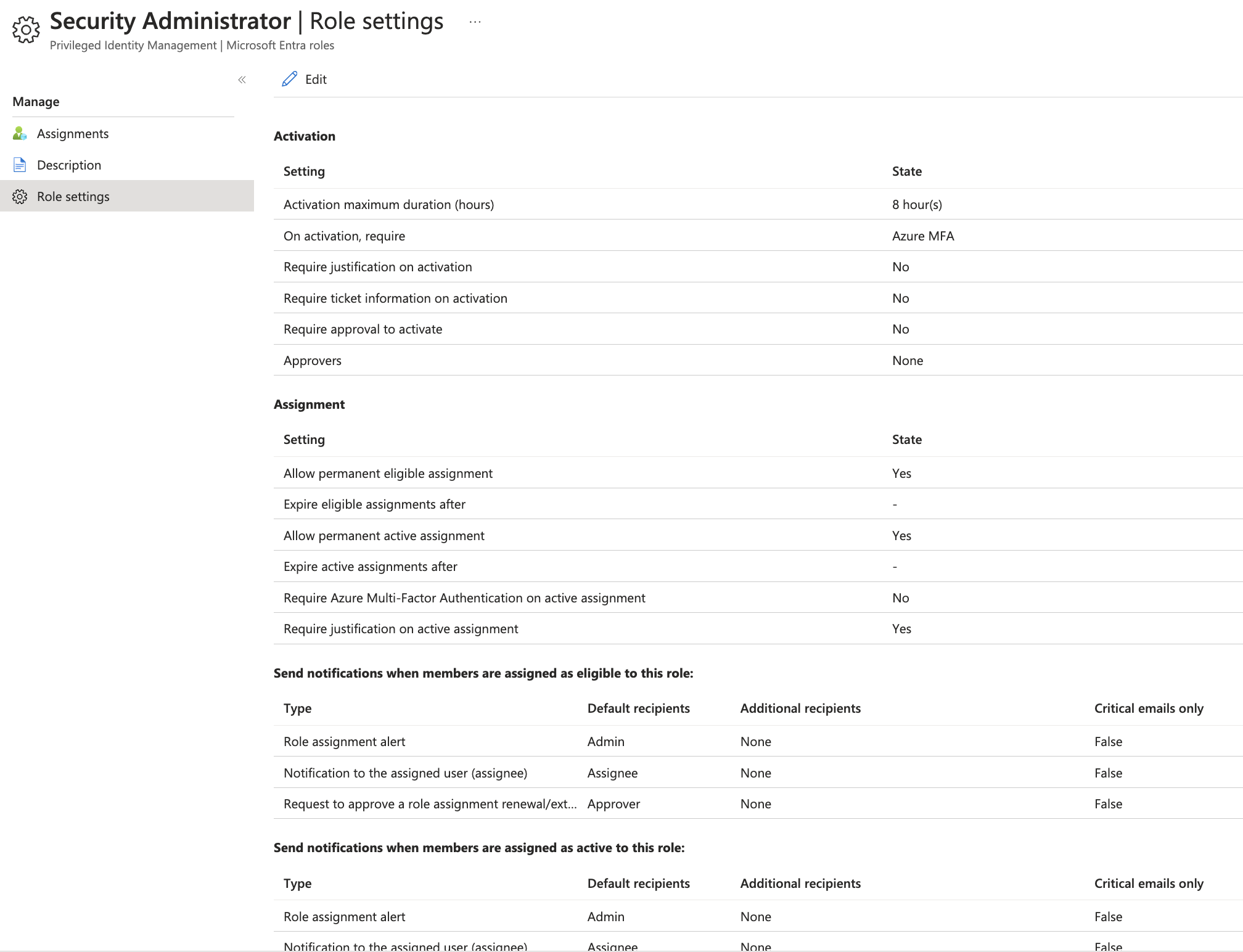
Each role can individually be configured with settings around:
- Activation - Maximum activation duration, activation authorization requirements, justification and approvers
My recommendation: I configure the maximum duration for all roles to 10 hours. For highly privileged like Global Admin, I reduce that timeframe to 1 hour. Approvers is individual, based on your RBAC process.
- Assignment - Assignment settings
My recommendation: Leave on default, except you want to add roles permanently active, then you need to change this setting.
- Notifications - Email notifications and recipients on assignment or approval
My recommendation: Set up emails to approvers (if in place) and otherwise send only critical emails only. Read more below on notifications with Microsoft Sentinel.
How to use it 📙
Now assumed from an administrator perspective, you want to enable roles to perform specific privileged tasks. Before you do that, you need to know which role you need for the task. Often, this is mentioned in the documentation of your task (it should be!), but if you don't know, this resource might help you: Entra built-in roles or Azure built-in roles, or when working with Microsoft Graph: Graph permissions reference
As admin, go to Azure Portal > Identity Governance > Privileged Identity Management > My roles
Here you can see all your available roles. Please note the assignment state. The already active assignments are shown in a different tab.
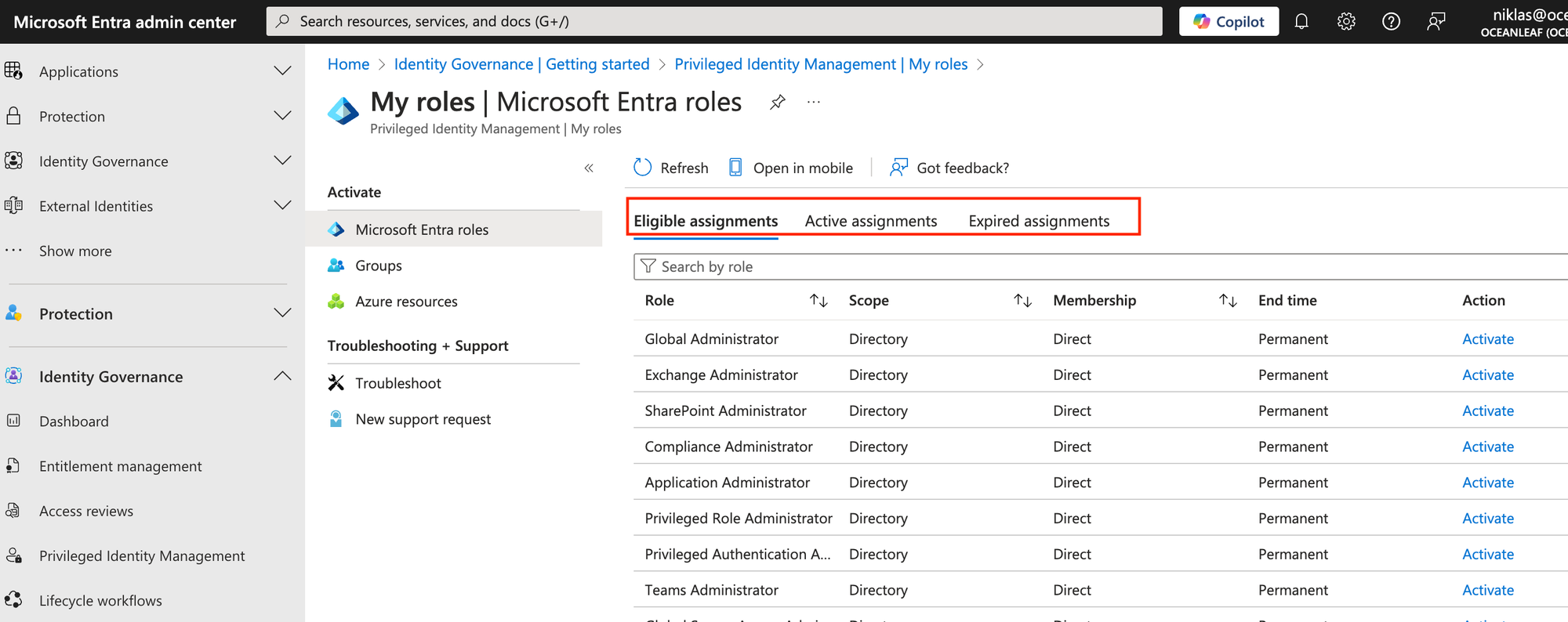
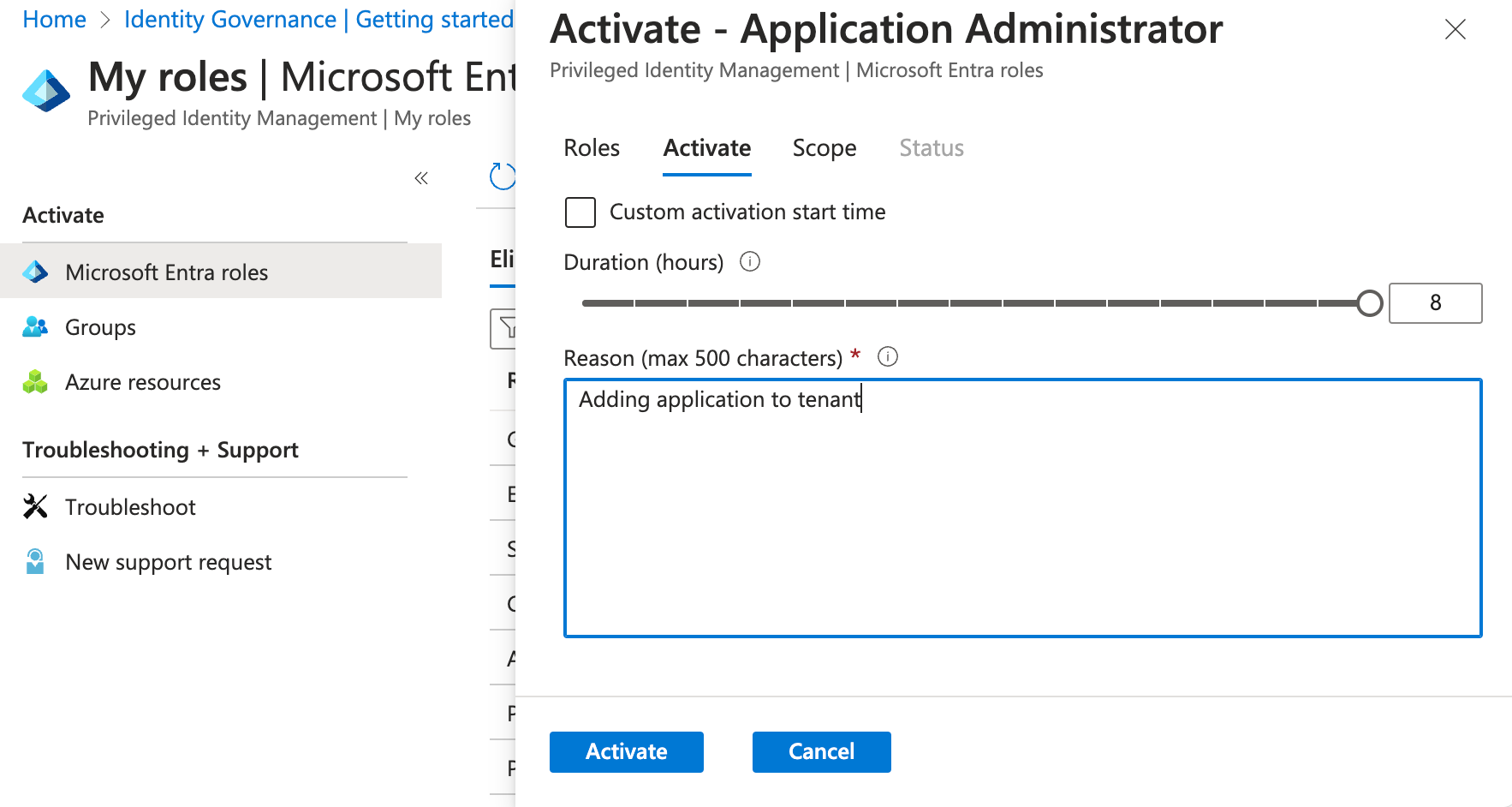
Now, to activate a role, choose the correct, hit "Activate" and provide the justification (required). Optionally:
- Set a custom activation start time (when the assignment begins)
- Adjust the duration time
- Select a scope (tenant level or Administrative Unit)
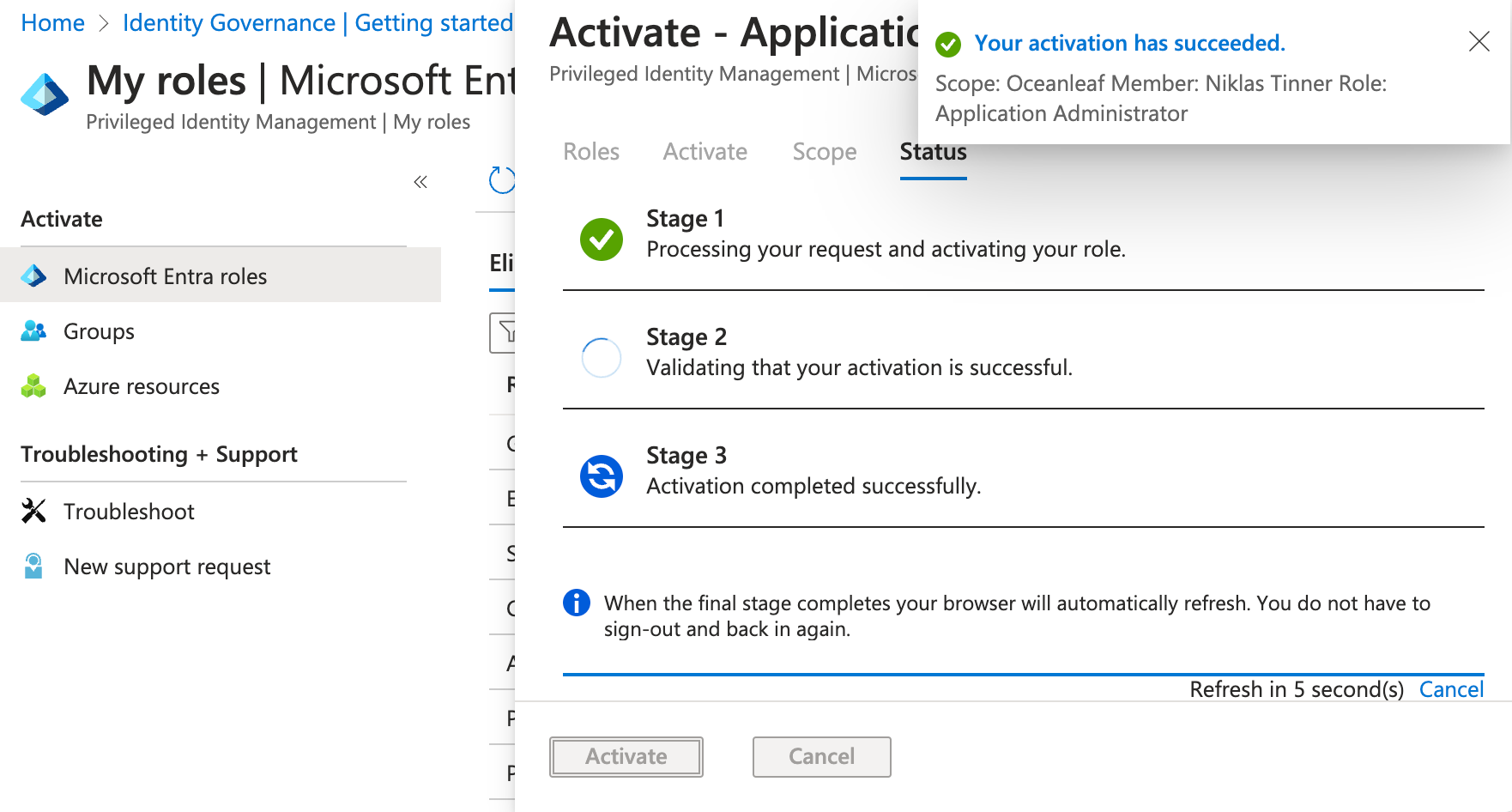
The assignment process through the systems take a few seconds and the page automatically refresh. (If you are in a different portal, make sure to refresh the site. Sign-out and sign-in again is not needed)
If an approval process is in place, request the role here and wait for it to be approved through the configured personas. (Approval through Azure Portal > Identity Governance > Privileged Identity Management > Approve requests)
You should now have the permissions in the context and see the active role under "Active roles" for your timespan. Later see them in
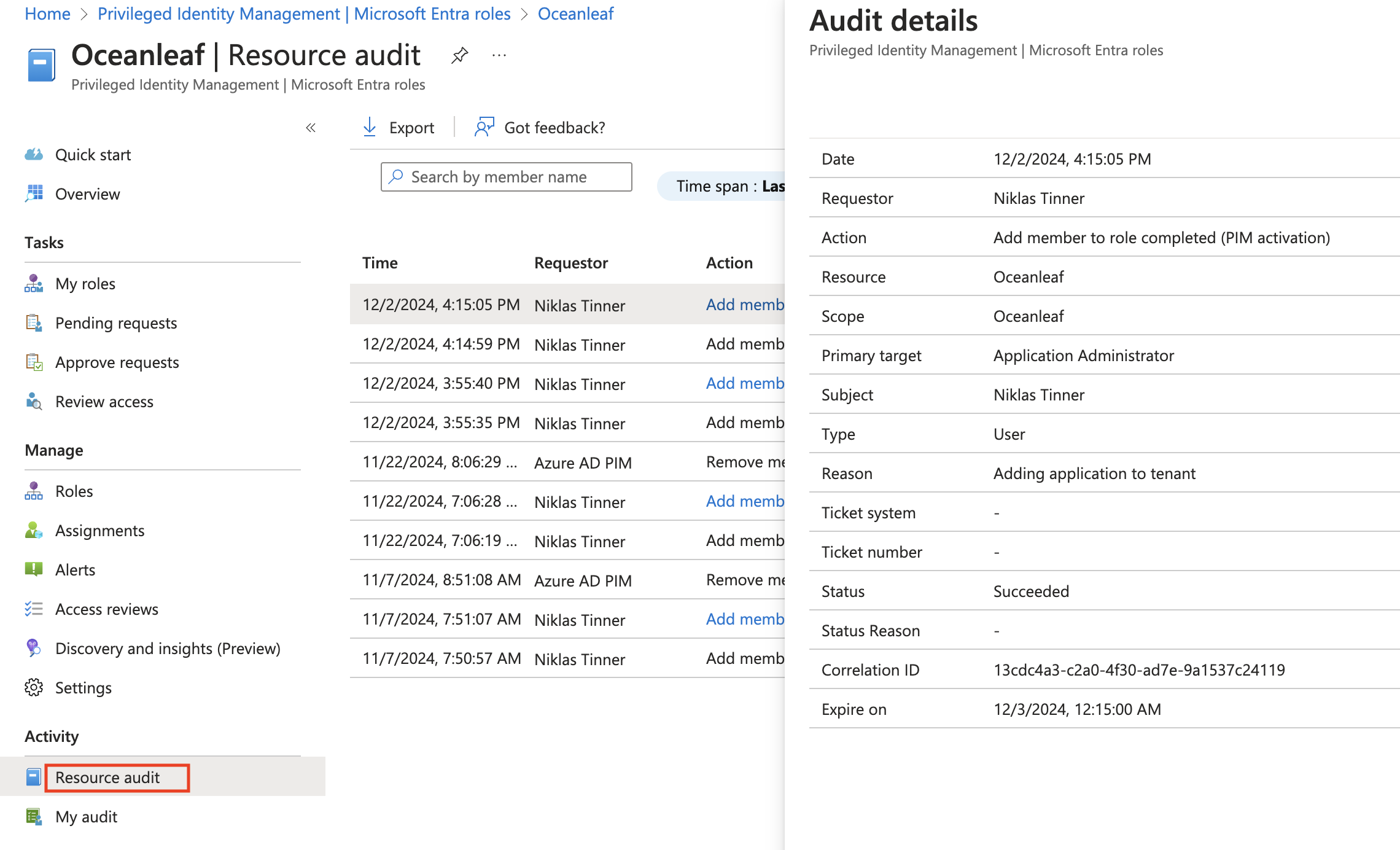
Audit logs
Find the audit logs of all PIM activities at PIM > (Manage) Microsoft Entra Roles > Resource audit. Click on any record to see more details, including the justification reason.
Bonus 🔮
PIM enabled groups
It is also possible to enabled PIM for groups. That means, you can be an eligible member of a group and activate the assignment for a limited timeframe. (Including all other features of PIM) This is a nice feature, when you assign privileges to groups, e.g., in for Intune custom RBAC roles.
To enable a group for PIM, go to the Group overview > Privileged Identity Management and Enable PIM for this group, after that, you can configure the same settings as for a PIM role.
Identity Governance
As PIM is part of Identity Governance, why not make use of the other great features to improve the handling of these hot identities? Use Access reviews to ensure that the role assignments are still needed. With this feature, you are appointed to regularly review your or others assignment to roles. And with Access packages you make a bundle of permissions (now including Entra roles!) to permit access to resources.
Administrative Units
Administrative Units are a virtual container inside of Entra ID. You can either add users or devices to an Administrative Unit as members. Entra ID roles can then be assigned on the scope of that Unit, but not the whole directory including PIM. This allows IT admins to only manage a subset of all users and devices. Read more
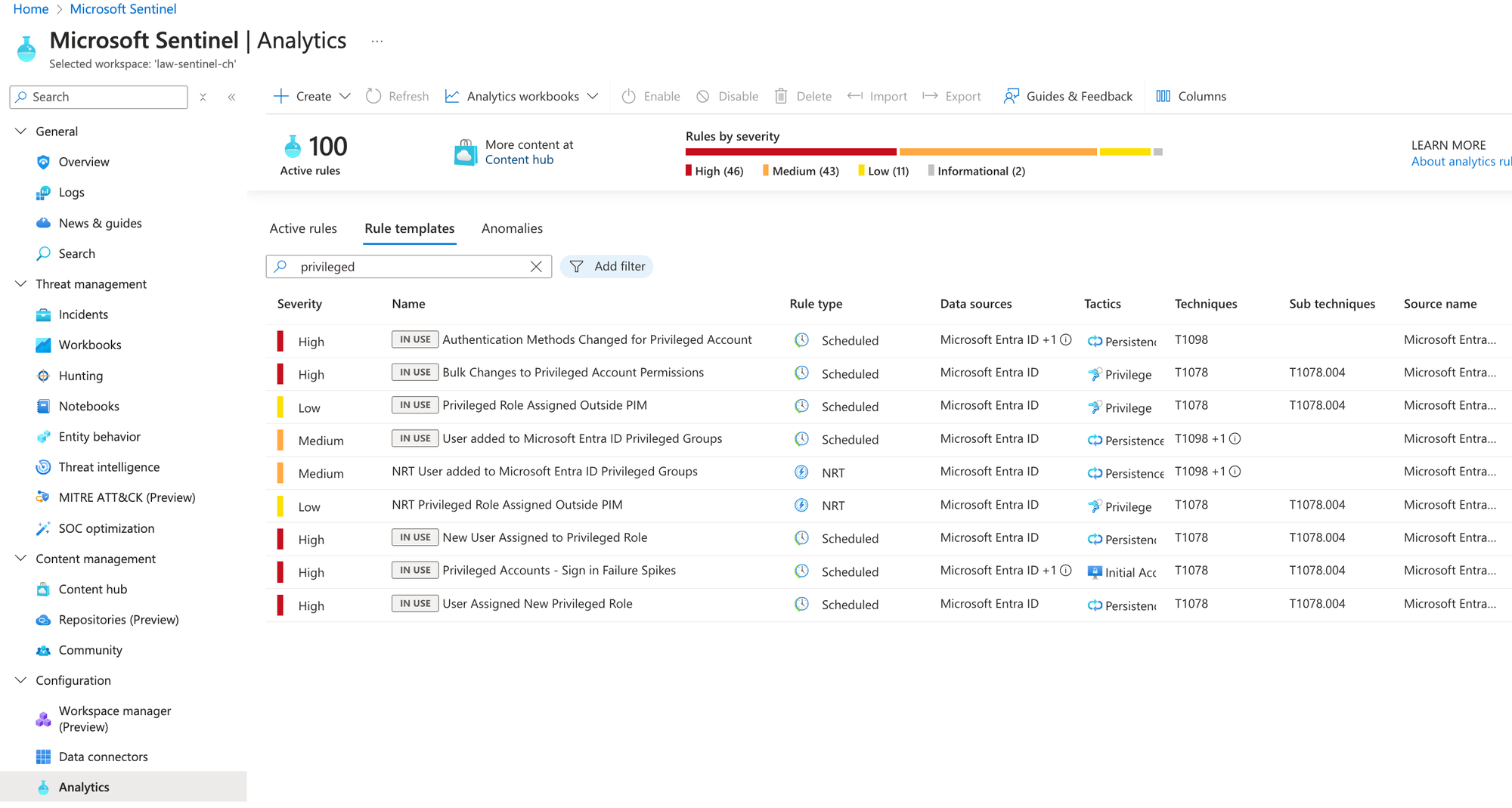
Sentinel integration
I advise you to use Sentinel (if in place) to alert and notify on PIM activation anomalies or critical role changes. You should get a NRT (near real-time) alert if a potential event of privilege escalation was detected. Here are the built-in rule templates to use:
Change tracking of roles
It is often hard to keep track on changes made to the built-in roles. Microsoft adjusts these and also adds new roles. To keep track and have a change history, I built an automation, which exports the manifests of roles to a GitHub repo regularly:
powered by Oceanleaf