Device Control with Intune
Introduction
This post will walk you through Device Control with Microsoft Intune. It is all about controlling access to certain devices or peripherals of Windows.
Background
Device Control can bring the benefit for these requirements:
- Security: Peripherals connected to your device and operating system can potentially contain malicious software or have an impact on your system. It is a measurement for attack surface reduction.
- Data protection: Confidential files could be exfiltrated on removable storage media and stay undetected.
- Inventory compliance: Only approved peripherals should be allowed.
If you are interested in the security background, check out Attacks via peripheral devices by Michael Schneider. Simply put:
- Directy Memory Access > mitigate with Windows Virtualization-Based-Security (VBS) and Secure Boot with DMA
- Sniffing of TPM > mitigate through Pre-boot authentication of Bitlocker
- Prevent FireWire and Thunderbolt > GPO "Prevent installation of devices using drivers that match these device setup classes."
- USB attack in combination with social engineering > Device Control and user education (HID devices may still be used for USB attacks)
Concept
There are different approaches when it comes to Device Control. The following are key:
- Block specific hardware classes - Unused or unwanted hardware classes are disabled
- Control removable storage - Granularly control read/write access to removable storage medium
- Allow-/blocklist certain devices - Inventory authority and control
It is important that your organization has clear guidelines regarding Device Control. This will have a significant impact on the end user. Furthermore, you need to prepare clear inventory data and follow a device strategy.
Guide
Identifying devices
To identify devices you can make use of the device manager. The properties will help to identify the device.
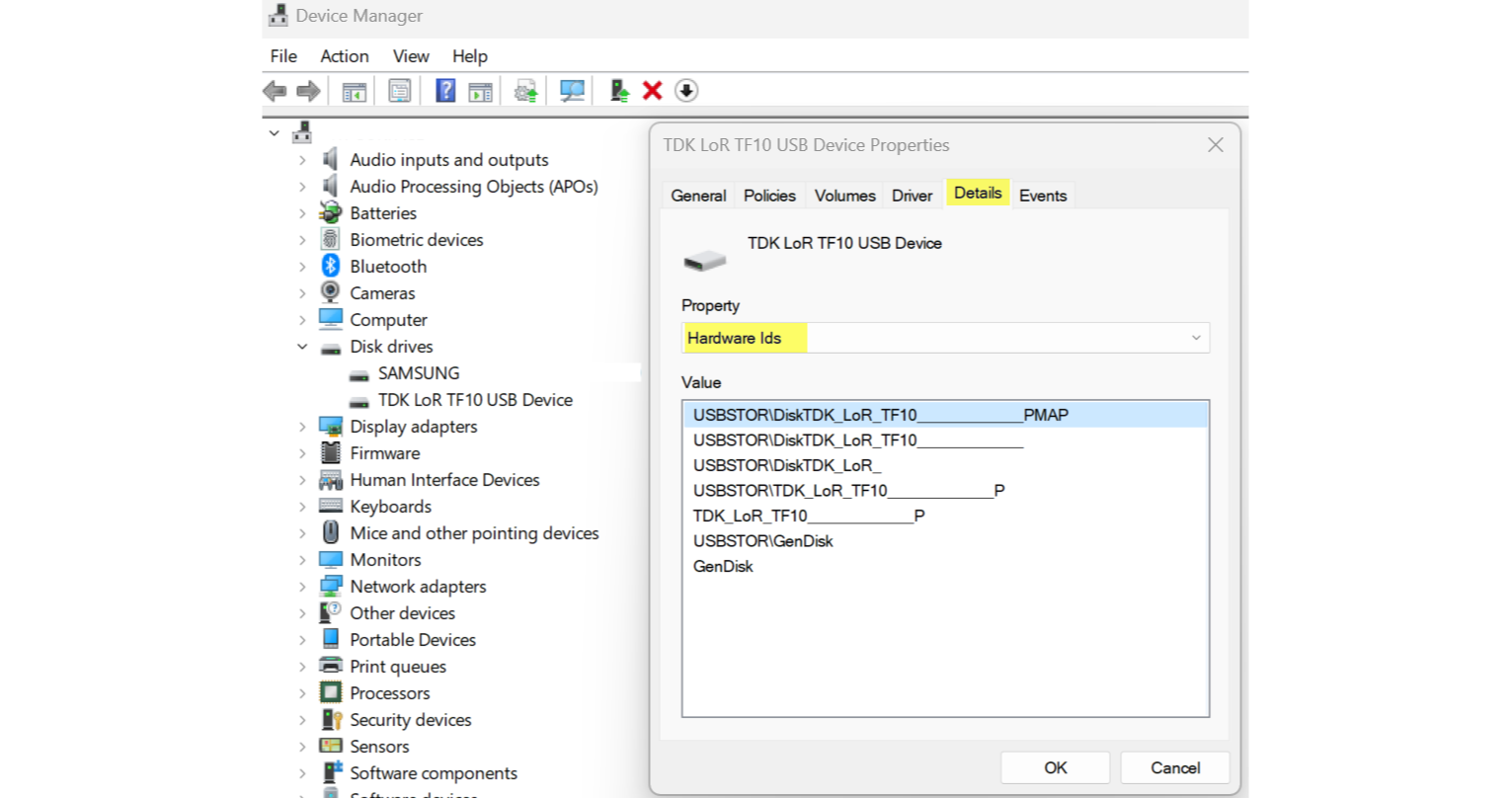
Some device classes may be unused and can be completely blocked, depending on your requirements.
- CDROM
- FDC
- FloppyDisk
- SmartCardReader
- TapeDrive
Microsoft publishes a list with all setup classes - there you can find the ClassGUID which is needed for the policy.
Reusable settings
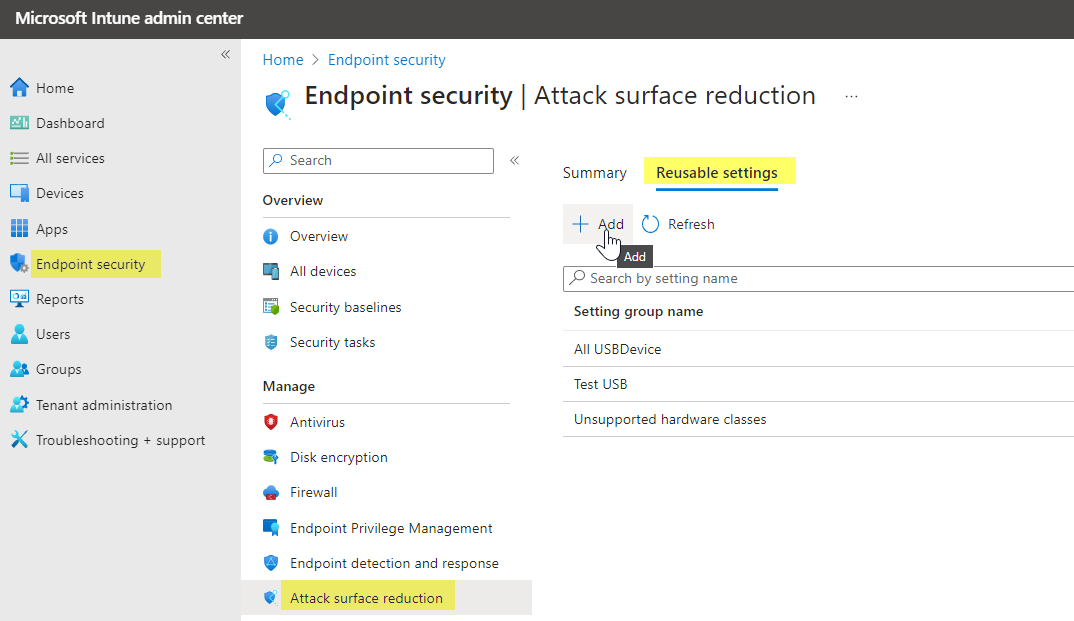
Reusable setting groups define a set of device attributes that can be used for multiple policies. This is more convenient and only requires updates at one place. To create this:
- Open Intune admin center and go to Endpoint Security>Attack surface reduction and switch the tab to Reusable settings
- Specify a name and description, and add>Removable storage (you can add multiple instances), then Edit instance - here you can edit multiple different attributes of storage media
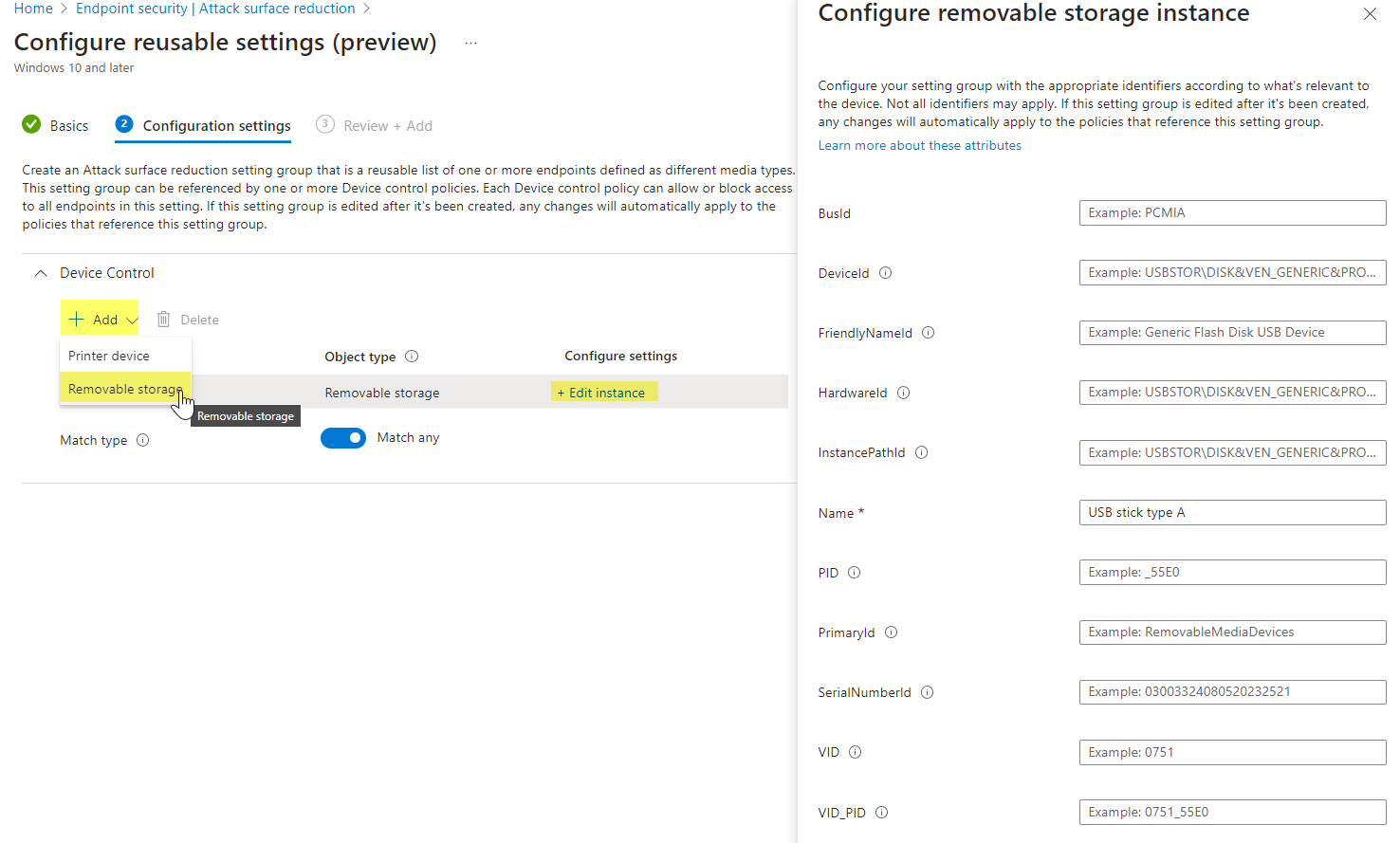
Note, that you can switch to "Match all" or "Match any" at the bottom. This means, that either one attribute within an instance or all must match to apply for this Reusable setting group.
Create Device control policy
A Device control policy is part of Attack surface reduction in Intune, also in the Endpoint Security node. Find all settings and description in the official documentation. You can orientate yourself with my policy.
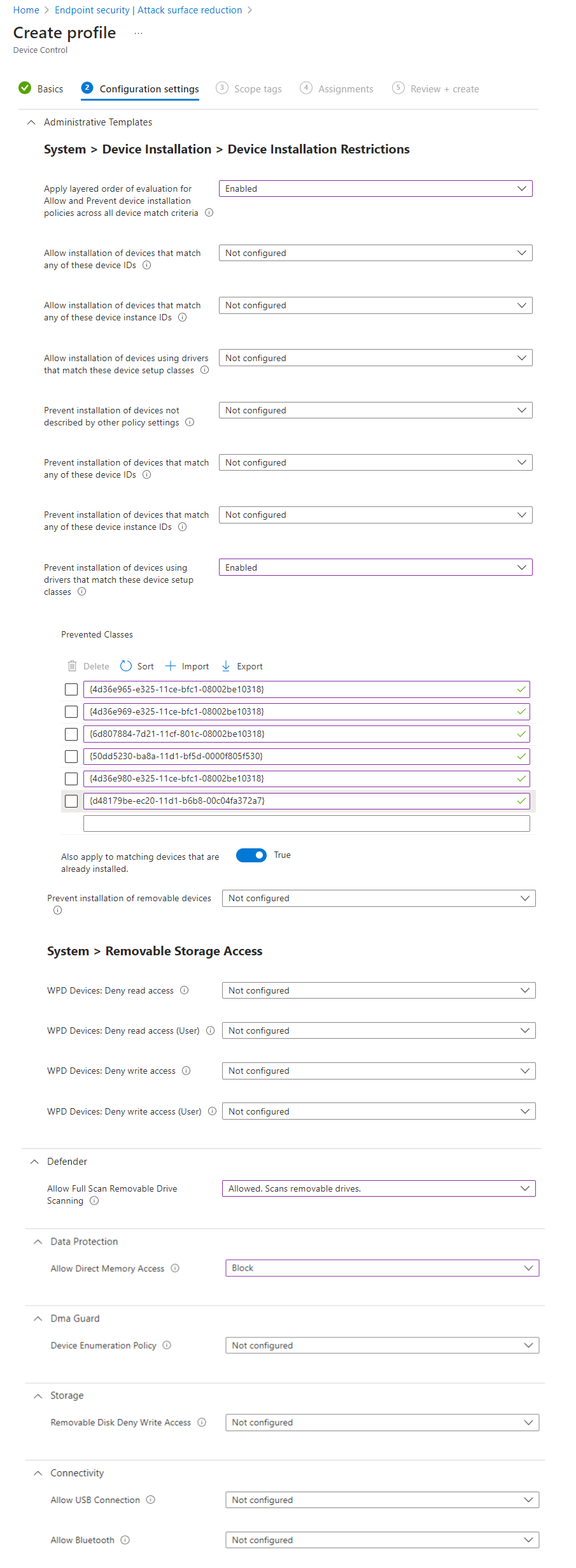
Please compare the settings with the Microsoft Security Configuration Framework.
Allow list through Reusable settings
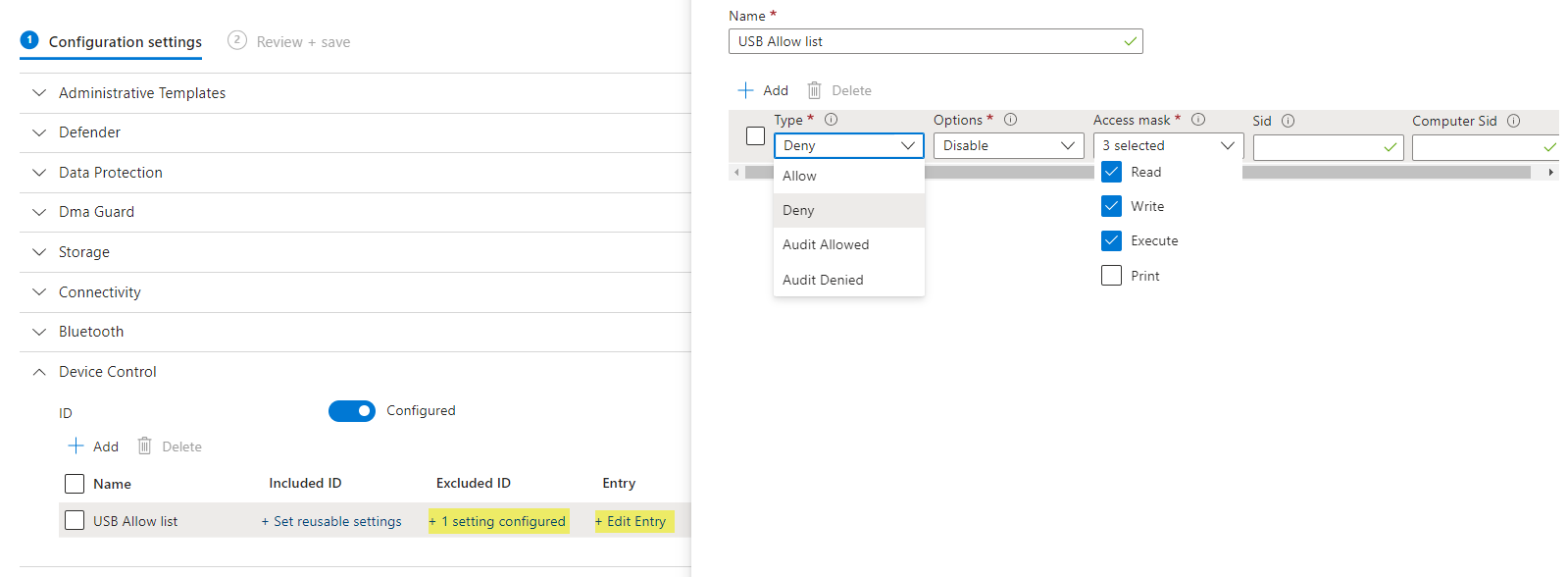
Any specific storage devices can be allow-listed in the Device Control policy. Therefore create a Reusable settings group and fill in values that identify the device.
Add this Reusable group as Excluded ID and Edit the Entry.
Notes from the field
- For inventory control, specifically allow listing storage and device types, I would recommend you to use the VendorID (VID) or VendorID + ProductID (VID_PID), mostly found under the HardwareID property.
- If you want to block all removable storage, add all related ClassGUIDs:
- Disk Drivers
- Storage Volumes
- Windows Portable Devices (WPD)
- Bluetooth control should also be considered, as it is a very popular feature and offers attack surface. Learn more


