Introduction to Microsoft Entra Security Service Edge (SSE)
Introduction
New Microsoft technology was released! Microsoft recently announced Microsoft Entra Security Service Edge. I want to briefly summarize whats new as part of my learning.
SASE
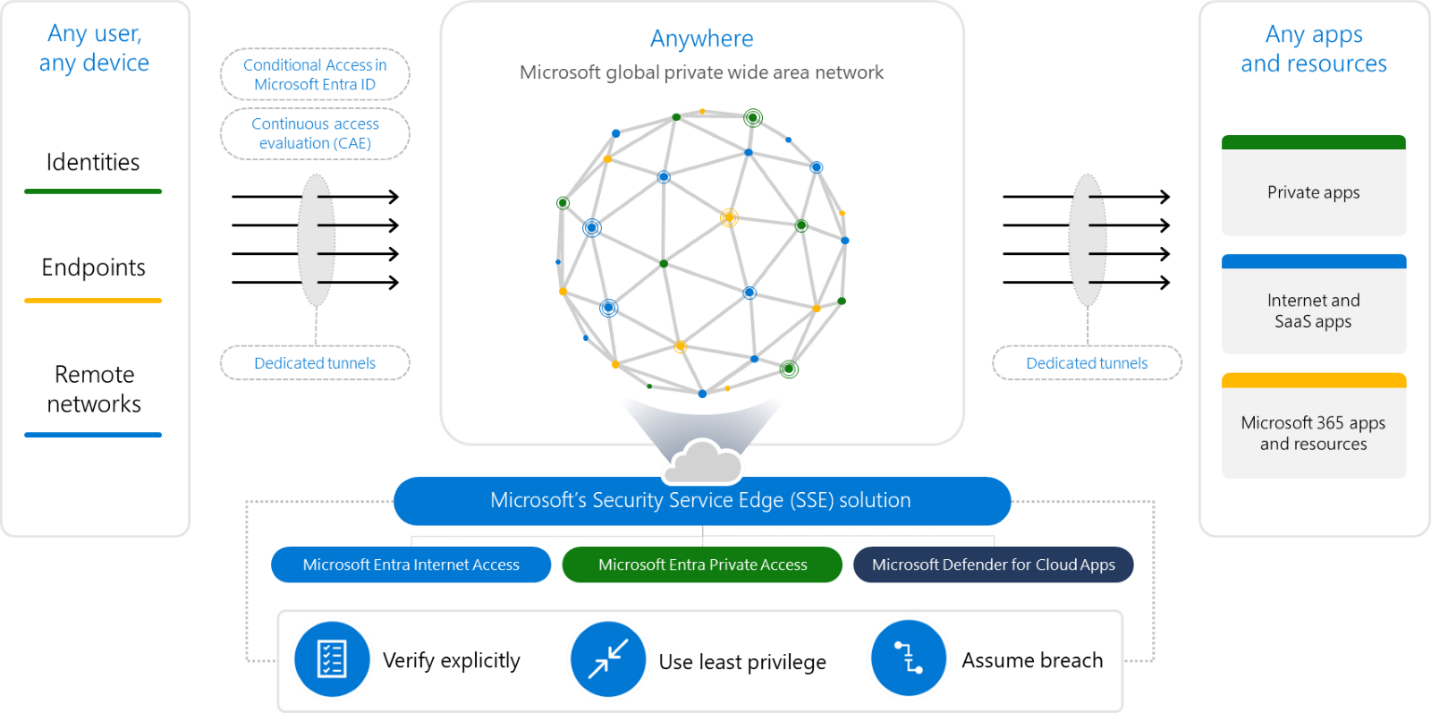
The concept of Secure Access Service Edge is new for Microsoft Entra and is defined as "Converge software defined wide area networking (SD-WAN) and Zero trust into a cloud-delivered platform..."
>Simply put; evolve network technologies to adapt with Microsoft identity solutions to connect users, systems, endpoints, and remote networks to apps and resources securely.
Key points
- Strengthen security by identity-driven access
- Networking, but cloud-native, aiming to:
- Rise security by:
- Applying policy profiles / routing traffic
- Set web filtering policies
- Connect with Conditional Access policies to apply access controls
- Cross over boundaries from corporate/private networks and public
- Leverage Microsoft's global network backbone for optimized connectivity
- Provide a seamless user experience
- Rise security by:
Security
There is a lot conversation about security in this topic, for my interpretation it is:
- The whole new products is based on Entra ID, such as ID protection and Conditional Access to provide secure authentication, apply tenant restrictions or to detect (risk) signals and correlate activity data
-> based on the principles of Zero Trust - The Global Secure Access client for Windows is an agent that can monitor and route network traffic over the Microsoft backbone and apply controls
- Or configure a remote network where your network customer premises equipment (CPE) connects to the Global Secure Access service through an IPSec tunnel (with this no client installation is needed but dependent on the network)
- Defender for Cloud Apps gives further insights as cloud security access broker (CASB) between the communication of your identities and cloud apps and allows for policies regarding app governance
Profiles
The traffic from three app/resource channels can be differently treated:
- Microsoft 365 - all traffic to Microsoft network endpoints
- Private access - traffic to on-premises hosted apps
- Internet access - traffic to any other network/the Internet
Elements of SASE
| Term | Description | Microsoft solution |
|---|---|---|
| Software-defined wide area network (SD-WAN) | Technology that optimizes and manages multiple sources of network connectivity to enhance the performance, efficiency, managebility and security of wide area networks | new Entra SSE |
| Secure web gateway (SWG) | Network perimeter protection that filters traffic for particular networks | new Micrsooft Entra Internet Access |
| Cloud access security broker (CASB) | Security solution that provides visibility and control over data and applications as they move between an organization's on-premises infrastructure and cloud environments | Microsoft Defender for Cloud Apps |
| Firewall as a service (FWaaS) | Cloud-based security solution that delivers firewall functionality, such as traffic filtering and network protection and policies | new Entra SSE policies |
| Zero Trust Network Access (ZTNA) | Security framework that requires zero trust, least privileged, all identities must be authenticated, authorized, and continuously validated before being granted access to company private applications and data | new Microsoft Entra Private Access |
What's new?
In Microsoft Entra we can greet two new features under the Global Secure Access pane.
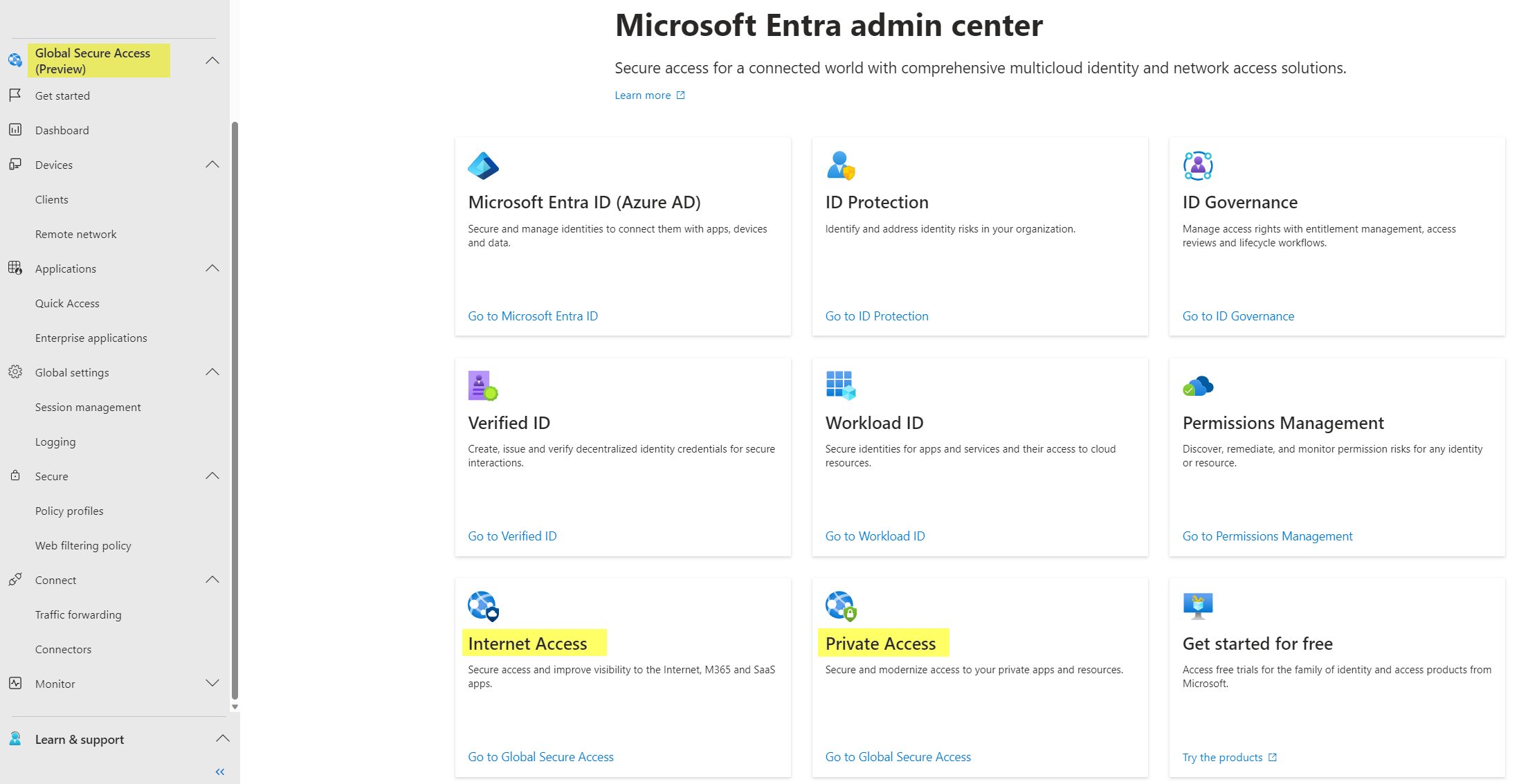
Internet Access
Protect access to any public app/SaaS. The Internet traffic can be managed through security traffic profiles and web content filtering policies.
Learn more in my dedicated post, including hands-on:
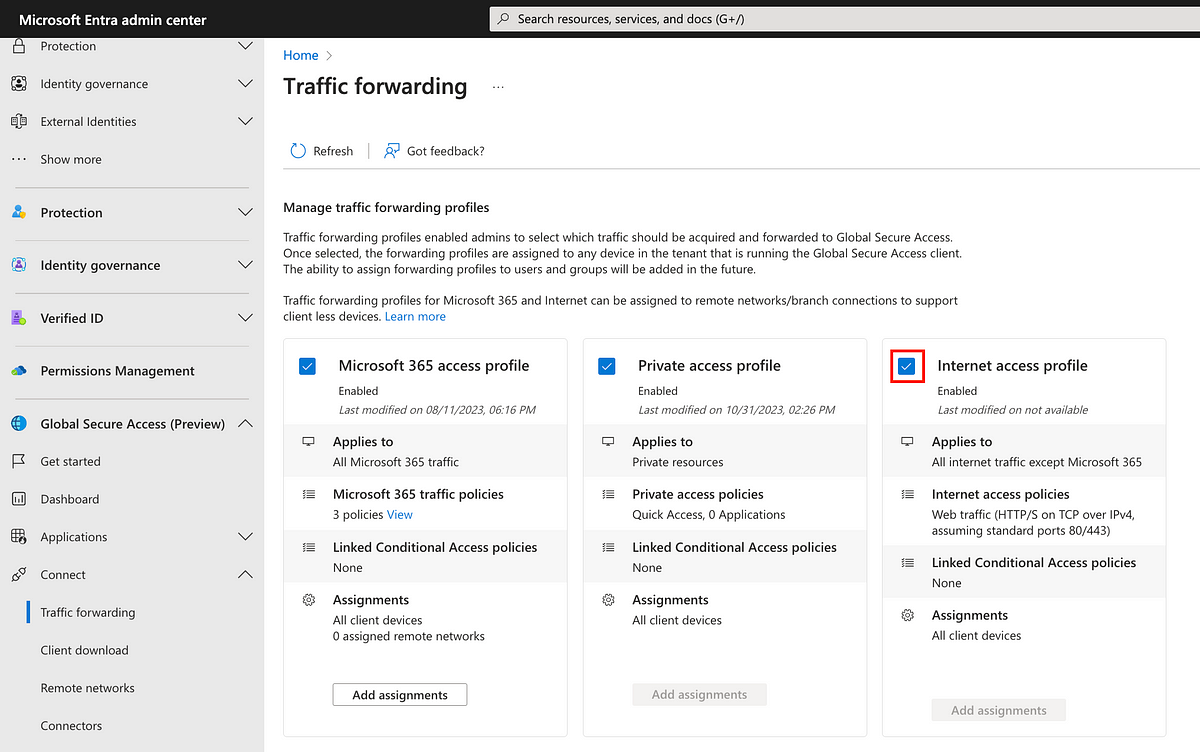
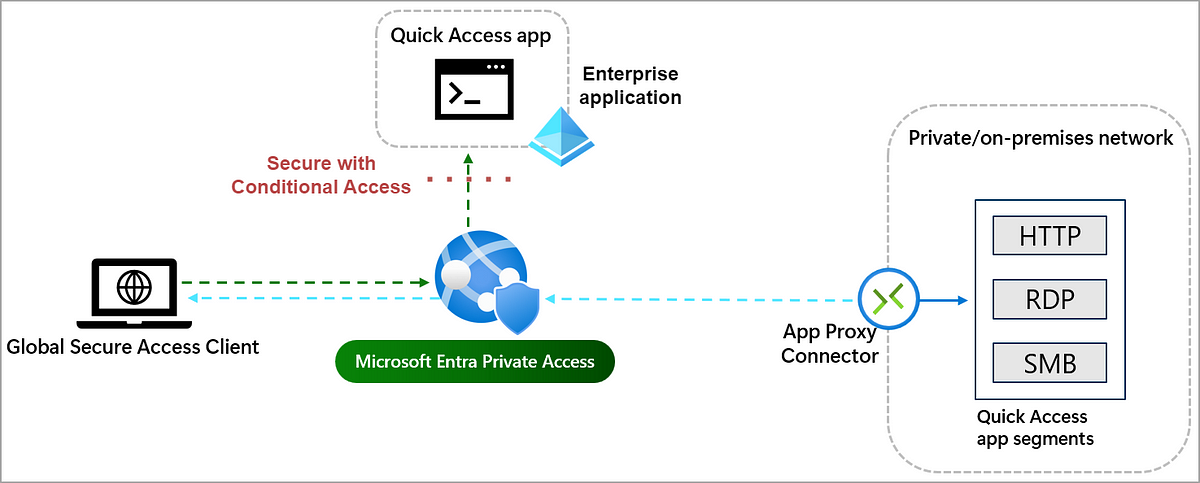
Private Access
Establish and secure access to any on-premises hosted app. (This is a comparable feature to Azure AD Application Proxy)
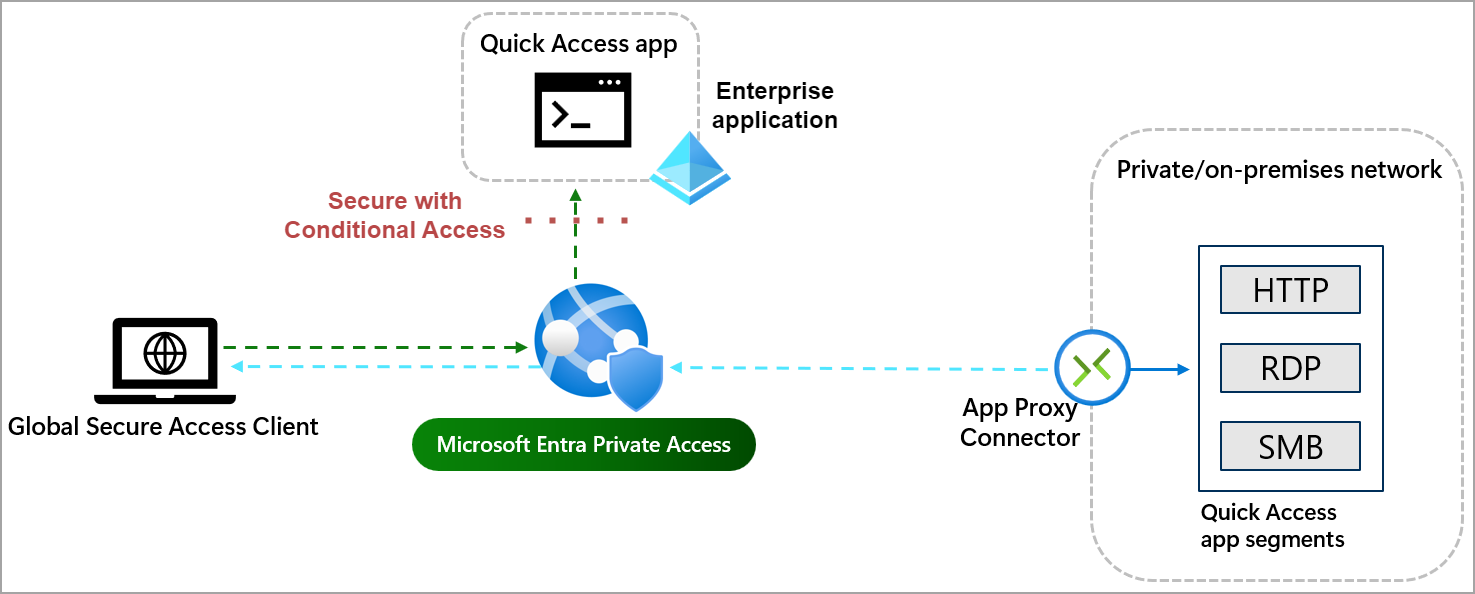
Source: Microsoft with custom additions
I have already written a post exclusively on this feature, including a demo:
SASE vs SSE
SASE - framework
Components:
- SD-WAN
- WAN optimization
- Quality of service (QoS)
SSE - subset of SASe that focuses exclusevly on cloud security
Components:
- SWG
- CASB
- ZTNA
Conclusion
From my perspective, Microsoft is expanding their identity portfolio with network tech to rise security and provide new features, which were until now rather reserved for other vendors.
For an organization with a single vendor and cloud strategy, this is a really welcome announcement. Network traffic can now be a more than ever relevant source to controlling Internet Access to corporate resources with Entra ID, Enterprise app management and Conditional Access (and more). And for Private Access, this enables a whole new set of capabilities by integrating on-premises apps, resources and protocols to endpoints.
Tests can be yet made, but as long as most features are in preview, orgs may still wait. It also requires some change of mindset, because the network limitations from before may not exist anymore. Furthermore the security architecture needs to orderly integrate the new concepts. For licensing we do not know anything as of August 2023.
But once more with SSE, we can profit from an even more capable security ecosystem.



