Windows 365: level up security on Cloud PCs

Introduction
This is the sixth part of the Windows 365 series on my blog in which I will show you how you can improve the security posture on your Cloud PC systems. I have listed and described recommended approaches to implement security technologies.
Security is at the heart of every modern system, and Windows 365 should also be secured accordingly. My focus is on the platform security, meaning the secure configuration of Windows and the identity access layer. This write up covers:
- Windows platform security features and technologies
- Steps to reduce the attack surface
- Strengthen the access to Windows 365 systems
- Overview of recommended security improvements on Cloud PCs
Overview
Have a look on this overview table to get an understanding of all the featured topics on a high level and their impacts.
| Feature | Description | Implementation effort | Security improvement |
|---|---|---|---|
| Endpoint Security & baselines | Apply system hardening and configure built-in security features | ❗Medium-High | ❗High |
| Windows LAPS | Local Administrator Password Solution, should be used for all elevated actions | 🟢 Low | ❗High (when also used during operations) |
| Admin roles | Clean up privileged admin roles | 🟢 Low | ❗High |
| App Control for Business | Configure & control app execution | ❔Depends | ❗High |
| Defender for Endpoint onboarding | More visibility and XDR | 🟠 Medium | ❗High |
| Identity - Conditional Access | Protect access to W365 on the identity perimeter | 🟢 Low | ❗Medium-High |
| Endpoint Privilege Management | Configure & control app elevation for special use cases | 🟢 Low | 🟠 Medium |
| Software update policies | Define policies so Windows, drivers and apps stay up to date | 🟢 Low | ❗High |
| Compliance policies | Verify your deployment and system integrity | 🟢 Low | 🟠 Medium |
Top features to get started with
Let's go through all the featured topics.
Endpoint Security & Baselines
I have a dedicated blog post that goes deeply into all aspects around security baselines. Summarized: Security baselines define a set of policies, controls, behaviors and requirements for hardware to keep a system secure and compliant with a framework that is established by security experts and security organizations. In Intune we can start with the following configurations to make use of the built-in security features:
- Antivirus - configure Defender Antivirus
- Firewall - configure all firewall to secure network access
- Attack surface reduction (ASR) - configure ASR rules and device control
- Account protection - account related security controls
- Windows hardening - various system security improvements (Settings Catalog)

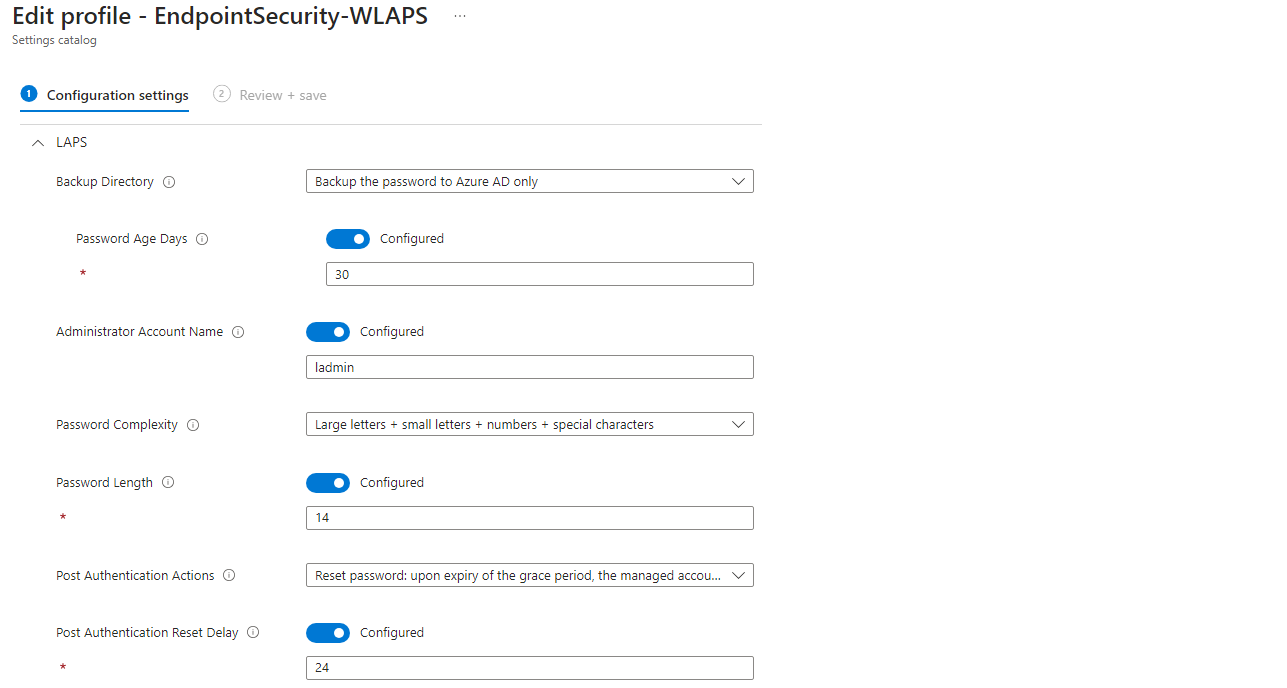
Windows LAPS
Windows LAPS is a Windows built-in feature to rotate the password for the local administrator. This is very important, because it prevents pass-the-hash or lateral-traversal-attacks where multiple systems have a common weak spot (the admin credentials). For full understanding, have a look on my blog post:

To deploy it in Intune, you need two things, both described in my LAPS post.
- Create a local administrator that is managed by LAPS
- Create an Intune Endpoint Security, Account Protection, LAPS policy to define the behavior and settings of LAPS
Admin roles
Administrators on a system have full access to modify, alter or delete everything. Therefore we should control the admins on:
- The management plane: Intune and Entra ID
- The Windows system: Local administrators and roles
Management plane admins
A management plane admin is someone that can configure the Windows 365 service. With that, someone could modify the configuration of the Cloud PCs or even delete them. Someone who controls the management plane can also control all layers below (the Windows system layer). Make sure to check the following Entra roles assignments in your tenant:
- Global administrator -> can do everything
- Intune administrator -> can configure every aspect in Intune
- Windows 365 Administrator -> have permissions on Windows 365 resources
- Cloud Device Administrator -> can manage devices in Entra ID
- Microsoft Entra Joined Device Local Administrator -> is local administrator on every Entra ID joined endpoint
🧹🧼 Reviewing and cleaning those roles up from unnecessary or unwanted assignments is crucial.
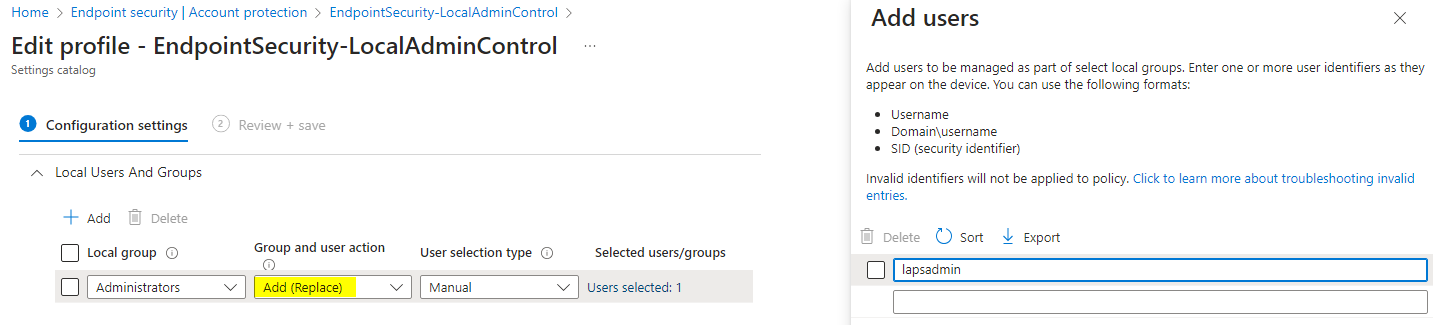
Windows system local admins
To control the local administrators (group) on the Windows system of your Cloud PC, you can make use of local user group membership / account protection policies in Intune. With the setting to replace all administrators, except your LAPS admin, no other user will have local admin rights.
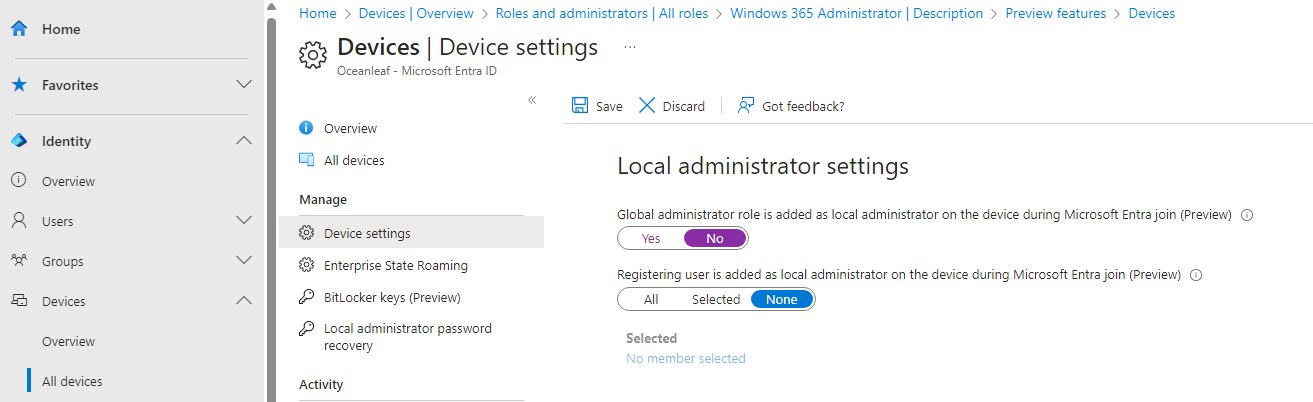
Furthermore, there is a new Entra ID device setting that allows to configure the local administrator user members of your tenant. I would configure both to 'none'.
App Control for Business
App Control for Business (ACfB - formerly Windows Defender Application Control) is a Windows security feature that controls the execution of code. It consists of multiple features that are all designed to secure software, drivers, apps and files on the system.
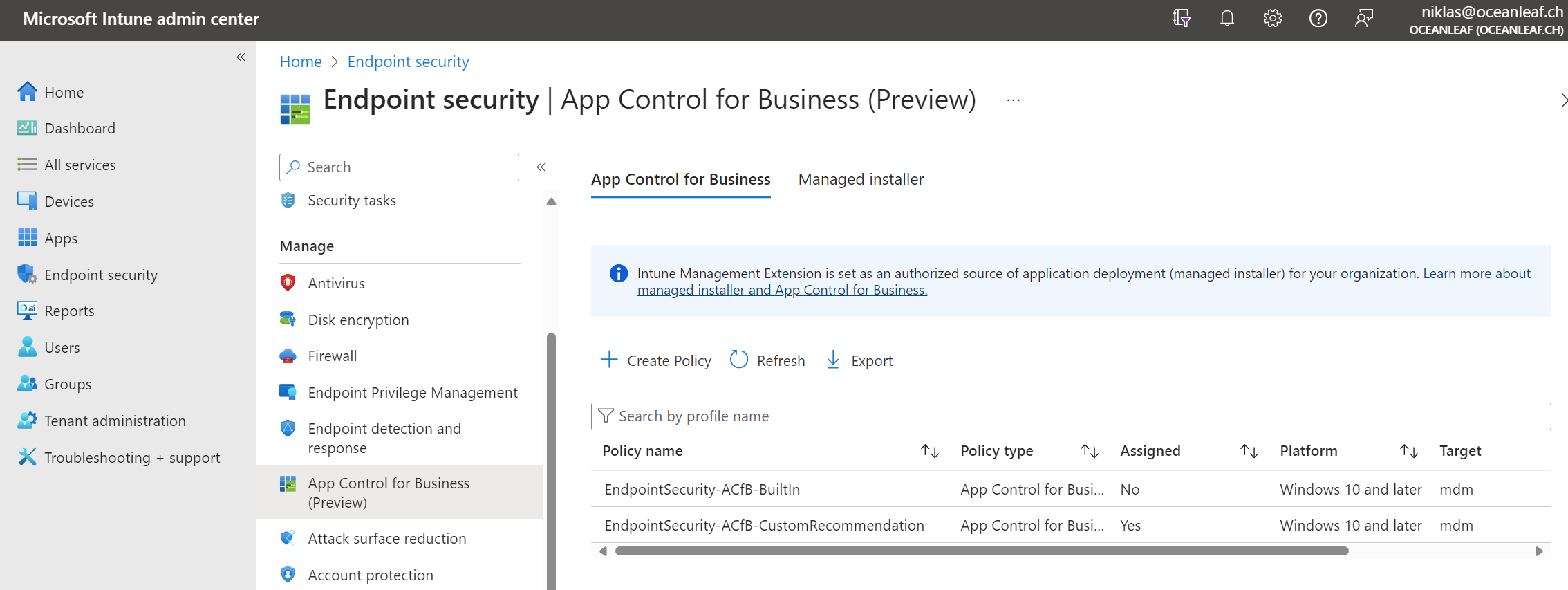
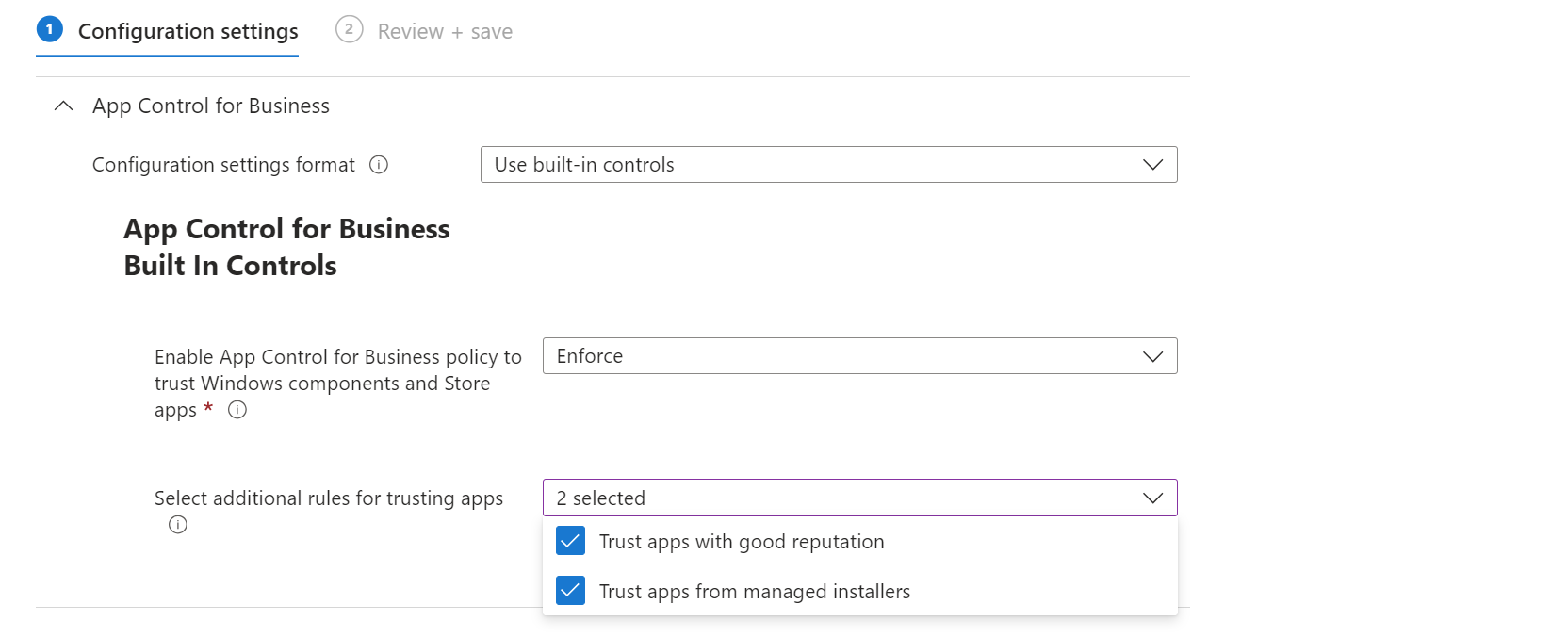
Use App Control for Business as an Intune configuration on Windows 365 and only allow software on the system that you know is good.
💡 Best practices to deploy App Control for Business
- Leverage the Managed Installer feature - with that all software installed by Intune is flagged as secure and can be executed
- Use the WDAC policy wizard to create custom XML based policies
- Use the XML based configurations, since the built-in options do not allow all features
- Start in Audit Mode with the feature and detect the potential impact
- Include publisher certificates of software and vendors that you trust
- Consider the Microsoft Intelligent Security Graph (ISG) feature - which is a database by Microsoft that classifies software and code. The ISG is a collection of generally well known and good reputable software.
Defender for Endpoint onboarding
Defender for Endpoint onboarding is crucial, so that Cloud PCs are protected by XDR and deliver their signals for analyzation, correlation, detection, hunting and response. In Intune you can create can setup the connection to Defender for Endpoint, as described in this blog post.
Identity - Conditional Access
To protect the identity layer and access to Cloud PCs you should consider Conditional Access. Combine different signals and conditions to ensure access to the service is valid. In Conditional Access you should choose the Windows 365 and Azure Virtual Desktop as target cloud apps to catch all authentication that could come against W365.
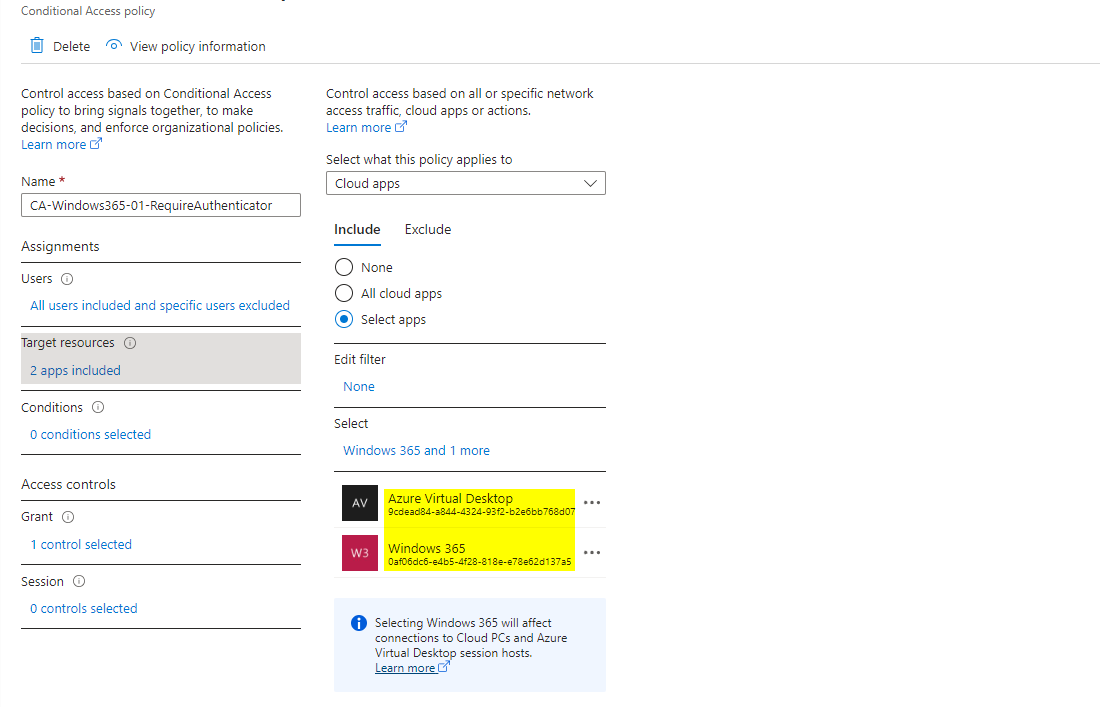
💡 Some ideas from policies:
- Require Authentication Strength such as Microsoft Authenticator or phishing-resistant MFA
- Only allow connections to Windows 365 from compliant devices
- Require terms of use for access to Cloud PC
- Restrict access to Windows 365 based on the user's location
Endpoint Privilege Management
Endpoint Privilege Management (EPM) is part of the Intune Suite. It is a feature that allows standard users to elevate applications defined by administrators in a policy from Intune. This feature helps to balance security and usability for end users. 1. They can run defined apps elevated by themselves, reducing the effort for the IT and 2. no local administrator rights that are system-wide are needed. Read more about it this blog post:

Software update policies
Software updates often deliver security fixes or address security relevant features in the system. Therefore, you should update all the software regularly, even better control the update deployments to ensure they are executed timely after release. Consider all those:
- Microsoft updates, includes updates for all their products such as Windows OS, Microsoft 365 Apps for Enterprise, Edge and Drivers & firmware from their catalog
- Third-party updates, anything that must be updated separately - use auto-update capabilities or separate tools for auto patching
Intune Windows Update rings
In Intune you can easily deploy policies for all Microsoft related updates. Create an update ring for Windows 10 and later and configure it accordingly. This is a recommendation:
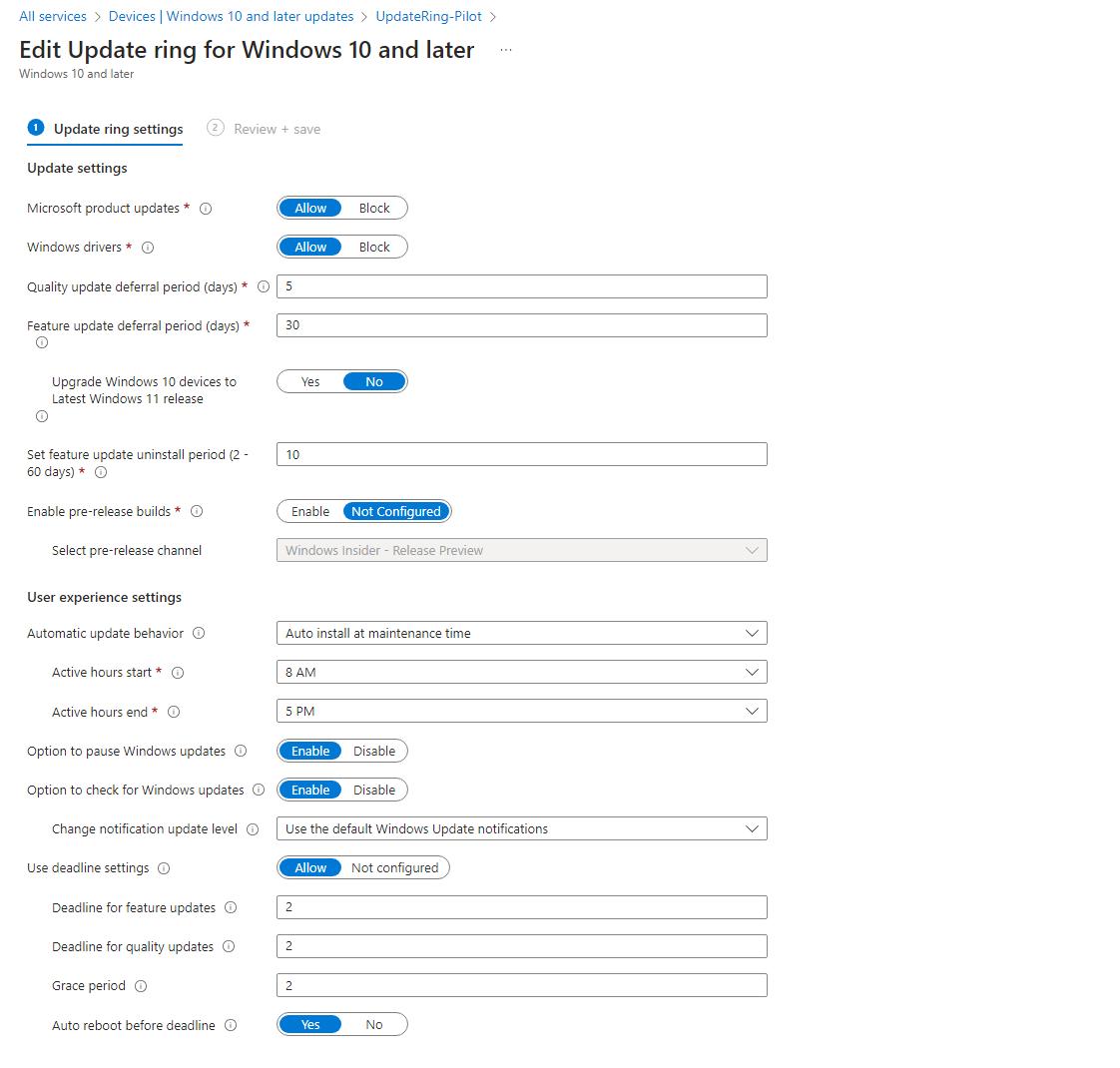
Read more about Windows Updates in this blog post.
Verify with Compliance Policies
For Windows 365 you should apply a compliance policy that checks if the features from above are enabled on the system and therefore are compliant. This is my recommendation:
| Setting | Value | Description |
|---|---|---|
| Minimum OS version | Latest OS version | OS minimum requirement, please note to continuously rise |
| Firewall | Require | Control network security |
| Antivirus | Require | System protection for Antivirus state |
| Antispyware | Require | System protection against spyware |
| Microsoft Defender Antimalware | Require | System protection against mailware |
| Microsoft Defender Antimalware security intelligence up-to-date | Require | Antimalware data up-to-date |
| Real-time protection | Require | Real-time system protection |
| Require the device to be at or under the machine risk score | Medium | Signal from MDE to consider machine risk score |
powered by


