Dive into Microsoft Security Baselines
Introduction
In my blog posts I often mention the Microsoft Security Baselines and the Microsoft Security Configuration Framework. Both are essential when it comes to endpoint security on Windows. This post is dedicated around security baselines, their adaption, configuration and operation.
Security configuration is complex. Frameworks provide a structured approach to assessing, configuring, and managing security settings across various systems and technologies. By following these frameworks, organizations can enhance their overall security posture, mitigate risks, and align their security practices with industry standards and best practices.
Our goal is to protect our environment from malicious actions and make it financially unattractive for attackers (ruin the ROI, return on investment). This includes to eliminate vulnerabilities that could be exploited in general/widespread attacks and make it too complex and time-consuming for a targeted attack, discouraging adversaries from targeting your infrastructure.
Our today's aim is to strengthen the endpoint security accross various categories. The technical implementation is accomplished with Microsoft Intune, however we need more tools for the full experience.
Microsoft Security Configuration Framework
The Microsoft Security Configuration Framework contains free resources from configuring security Hardware, Policies, Controls and Behaviors.
This framework describes 5 levels of enterprise security. This means, the higher the level, the more security configuration is required - resulting in a more secure device. It is important to mention that I will aim for level 3/enterprise high security. This is the highest level on 'default' workers devices.

Note, that there are also other security frameworks like CIS, NIST - STIG, BSI, ACSC and more.
Microsoft Security Baselines
Microsoft recently released updated Security Baselines for Microsoft 365 apps and Edge.
The Microsoft Security Baselines are configurations that are coming from the Security Configuration Framework. You can download the sources from the Microsoft Security Compliance Toolkit, which includes:
- Baseline files of Windows, Edge and Microsoft 365 Apps for Enterprise (latest) versions
- GPO and GP Reports (including .admx files
- Excel documentation (for some also PDF documents with more information)
- Scripts to import/local install
- PolicyAnalyzer to compare baselines with local state
Updating
Please keep in mind that Microsoft regularly updates the security baselines with new settings. This ensures that the security configurations remain up-to-date and aligned with the latest security standards and practices provided by Microsoft. The cadence looks as following:
- Windows OS - once a year, when the new major OS version is released
- Microsoft 365 Apps - usually twice a year
- Edge - on every new major version, usually once a month
You can track the new versions on the Microsoft Tech Community blog.
Deployment methods
Before we start with the effective deployment of the security baselines, we need to clarify what that means.
- Institute releases security framework and baselines
- Admin reviews and imports security baselines to management system
Hardware security can not only just be 'deployed', the hardware needs to provide the functionalities and prerequisites too. - Management system (Intune or GPO) deploys settings to devices
- Devices apply settings
Endpoint security
To get an idea of what's in the Microsoft Security Configuration Framework, I want to briefly present some Windows related security features which are mentioned. If you are already familiar with them, you can skip this part.
| Feature | Description |
|---|---|
| Local Admin Password Solution (LAPS) | Manage, backup and rotate local administrator passwords |
| Defender for Endpoint | Extended detection and response, threat and vulnerability management, threat intelligence |
| Windows Defender Credential Guard | Isolate through virtualization based security |
| Windows Defender Application Guard | Run applications (Edge and Office) in a virtualized context |
| SmartScreen | Reputation based filtering of websites, downloads and apps |
| AppLocker | Define and enforce policies for the execution of applications |
| Windows Defender Application Control (formerly part of Device Guard) | Successor of AppLocker with more features |
| Smart App Control | Block potentially unwanted apps based on Microsoft intelligence |
| Trusted Platform Module (TPM) | Physical security chip on mainboard to protect secrets and keys |
| BitLocker drive encryption | Storage drive encryption |
| UEFI Secure Boot | UEFI security to check signature of boot components |
| Virtualization Based Security (VBS) | Uses hardware virtualization and the Windows hypervisor to create an isolated virtual environment that becomes the root of trust of the OS |
| Memory integrity (formerly Hypervisor-Protected Code Integrity (HVCI) and formerly part of Device Guard) | Operating within the isolated virtual environment of VBS, safeguards Windows by enforcing kernel mode code integrity and preventing unauthorized modifications |
| Windows Hello for Business | Go passwordless, reinforce security and increase end user usability with PIN and biometric authentication |
| Kernel Direct Memory Access (DMA) I/O protection | Protects against external peripherals from gaining unauthorized access to memory |
| Exploit Protection | Enforce memory protection for OS-level controls (includes more sub features) |
| Attack Surface Reduction (ASR) | Set of policies to prevent actions and apps that are typically used by exploit-seeking malware |
| Controlled Folder Access | Protect valuable data from malicious apps and threats, such as ransomware |
| Modern Standby | Enables an instant on/off user experience (device lock and sleep) |
Deployment
The deployment will be focused on Intune, although I will mention the similarities from Active Directory and GPO's. In a nutshell the process looks as following:
- Download the Microsoft Security Compliance Toolkit
- You can find the GPO's here and all the documentation - I would highly recommend to have a look at the documentation
- Import the GPO or settings files
- Create the Intune profile and assign it / link GPO to Organizational Unit
Intune
Built-in security baselines
Microsoft provides their Security Baselines as one profile per product built-in into Intune. You can find it under Endpoint Security>Security Baselines. These capabilities are available:
- Create and assign profile with current baseline settings
- Export policy
- Change version (update to latest) - Microsoft should update these regularly in Intune
- Settings can not be removed from the baseline, only set to "not configured"
Endpoint security profiles + Settings catalog
If you don't want to implement the built-in profiles, it is also possible to configure the settings individually. For this, you want to use Configuration profiles (Settings Catalog) and Endpoint security profiles, which cover:
- Antivirus
- Disk encryption
- Firewall
- Endpoint Privilege Management (not relevant for baselines)
- Endpoint detection and response (only for MDE onboarding)
- Attack surface reduction
- Account protection
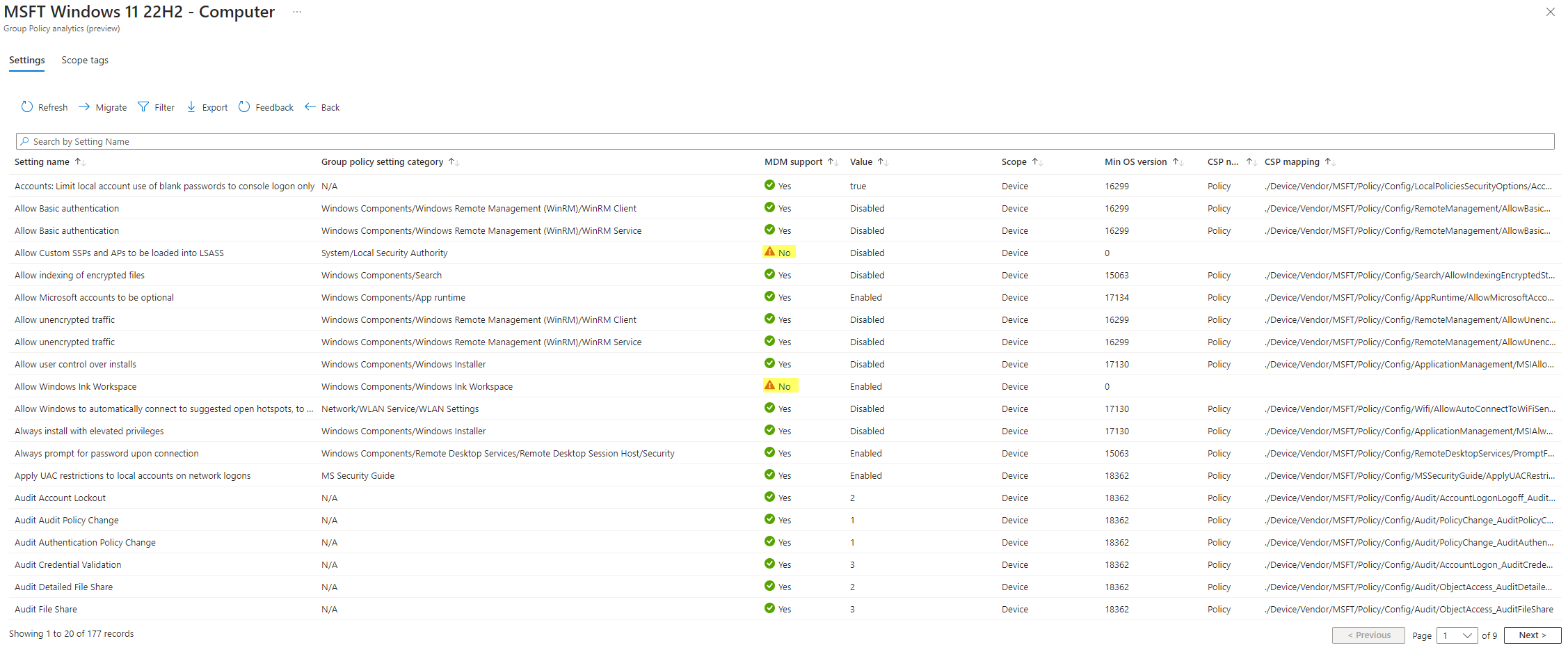
To import GPOs in Intune, you can use Group Policy analytics. Basically, you can import gpreport.xml files which are then analyzed by Intune if the settings are available in Intune:
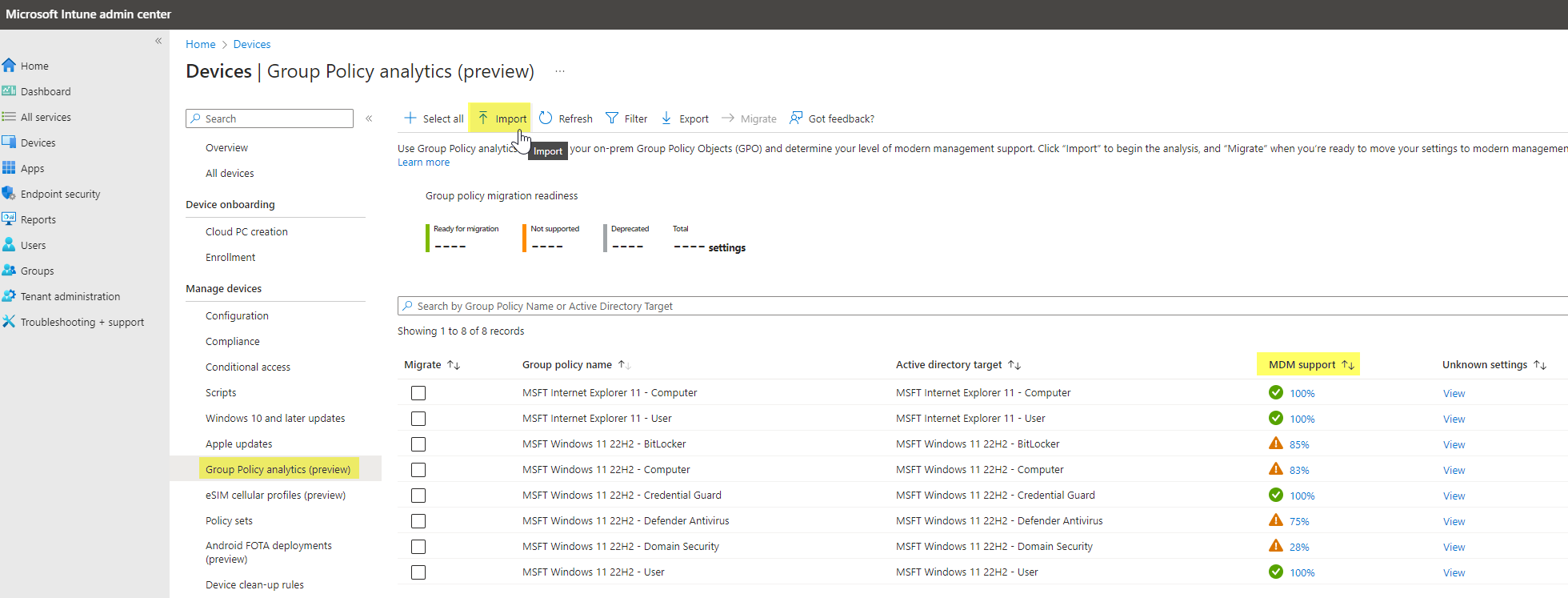
As you see, there are not all settings covered by Intune 😥. To further see which settings exactly are affected, click on the MDM support.
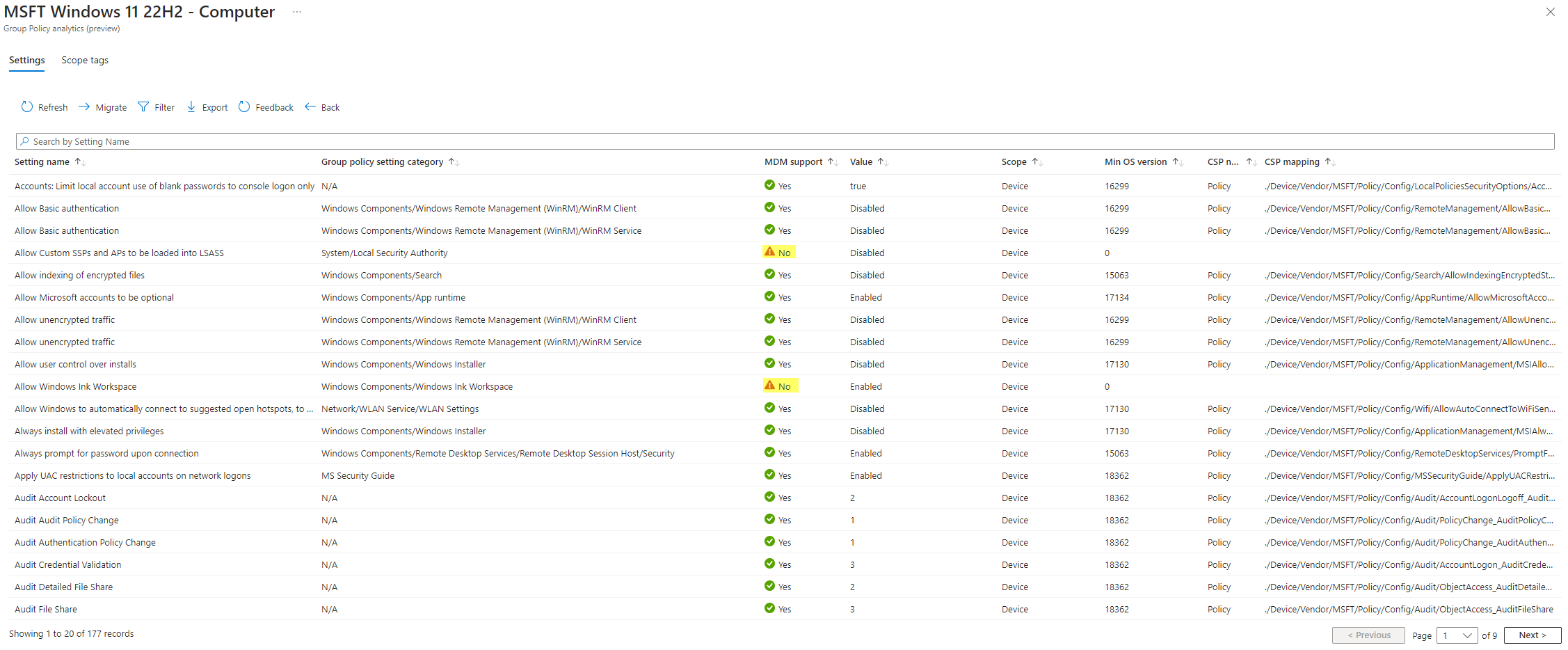
Now you might ask what to do with the settings which can't be managed through Intune. Unfortunately, there is no simple solution as of now. You have to address these settings through configurations in the registry, or if this isn't possible, you need to find other ways. (really dependant on the use case)
Generally, to find more information to the settings you can consult:
- The excel documentation (holding info text, registry path and supported OS version)
- GPO settings or gpresults
- Client configuration on devices
- Other tools, read more in the assessment/validation chapter
Recommendation
My personal advice for the Intune deployment is to use the built-in baselines. If any product or settings are not covered, you have to manually configure the settings or automate it with Remediations.
The goal of endpoint security is to configure security settings profiles according to the security framework you are following.
Operation
Once the baselines and configuration profiles are imported, the time is here for operation. I really want to highlight this topic, as it often goes forgotten or the awareness is too low. Some familiar processes are:
- Deviation/changes - when baseline settings can't be met for some reason
If there is a security setting that potentially affects the operating system (OS), applications, or behavior of any end user process, it is important to follow a systematic approach. Begin by identifying the specific setting responsible for the impact and then proceed to validate its effect on a test device. This validation involves observing and understanding the normal behavior prior to making any changes to the setting. By doing so, you can gain valuable insights into how the behavior is expected to appear when the setting is altered.
Now you need to modify this setting broadly and deviate from the baseline. With this you are not compliant to the Configuration Framework. This is not directly an issue, but you should always:
-Have a clear statement from the business responsible to make this deviation
-Have documentation on the changes
- Documentation - where to find deviations or more information
When you download the Microsoft Security Compliance Toolkit you also get Excel sheets where every single setting is documented. This includes the setting name (Intune or GPO), path, category, recommended value, registry key (if applicable) and info text.
Ensure that you clearly highlight and document the values you have deviated from. It also makes it easier when updating to a new version 😉
Assessment/validation
After applying settings profiles, an assessment can be the next step. This is important to validate if all the settings were successfully applied to the system and the device is now compliant with the framework. There are multiple ways to fulfill this part:
- Policy Analyzer tool by Microsoft, coming with the Microsoft Security Compliance Toolkit
- HardeningKitty by Michael Schneider, a free 3rd party tool to compare client settings with a template
- Other 3rd party tools (often come from security vendor's, ask your security department 😉)
Policy Analyzer
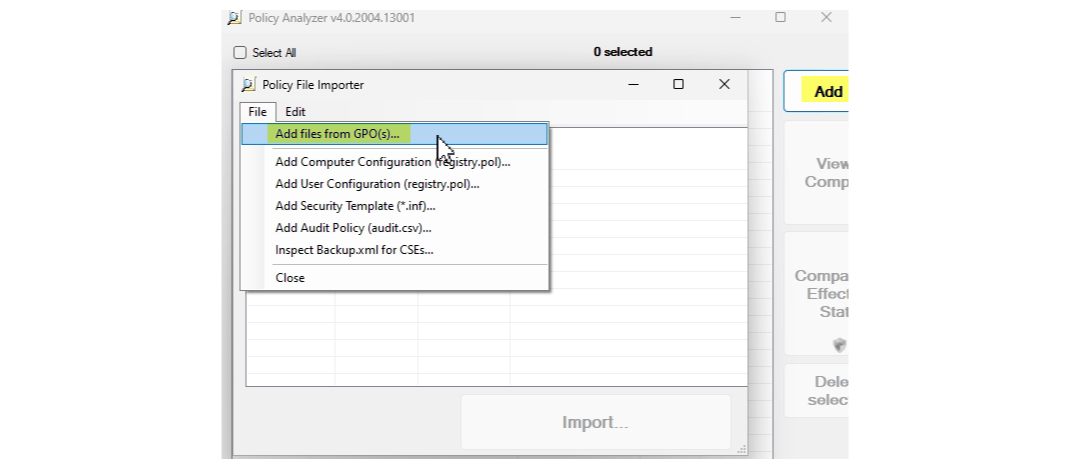
- Run the PolicyAnalyzer application
- Add policy files and choose the ones from the Security Configuration Framework
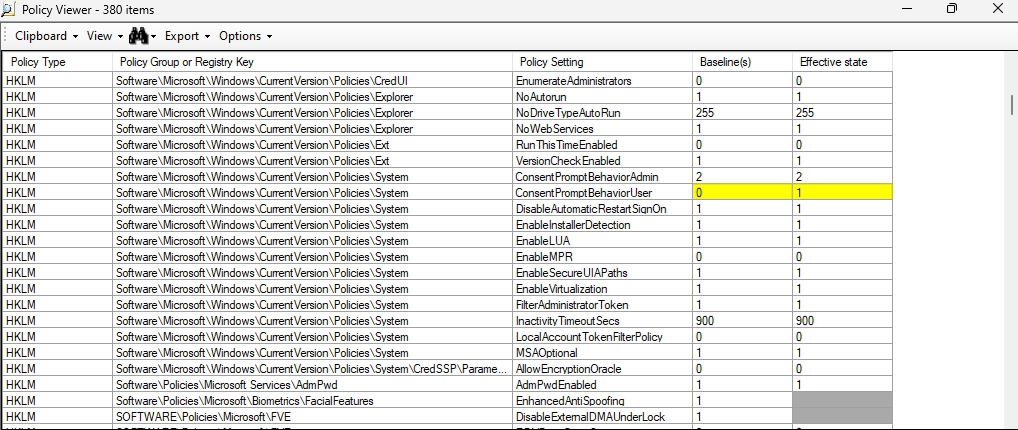
- Now you can import the files and should see the baselines, next you can compare them with the effective state on your device (requires local admin rights)
- Compare the values
- Yellow marked means that there is a deviation from your client settings to the baseline
- Greyed out means that the settings couldn't be validated (no registry key found)
HardeningKitty
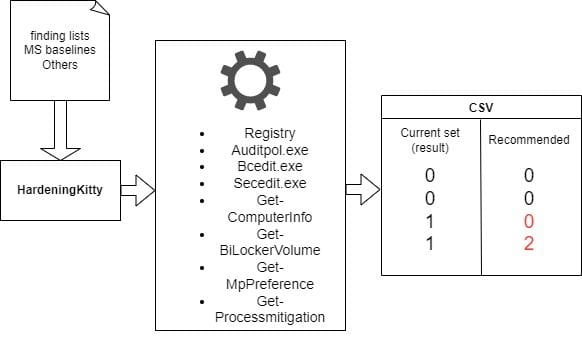
Used modules
- Bcdedit.exe - Windows Boot Manager/Loader
- Secedit.exe
- Get-Computerinfo - General computer system data
- Get-Gitlockervolume - Bitlocker encryption status
- Get-MPPreference - Defender Antivirus configuration and info
- Get-Processmitigation


