Kill chain, a simple secure environment and the decision for Microsoft
Recently I was in contact to an official Microsoft employee, talking about cybersecurity in general and of course the modern workplace. I found that topic so interesting, that I decided to dedicate a blog post to my personal opinion and some details about it. In the past I have already published an article, that covers Micrsoft security concepts. Now its time to extend my thoughts:
The kill chain of threats
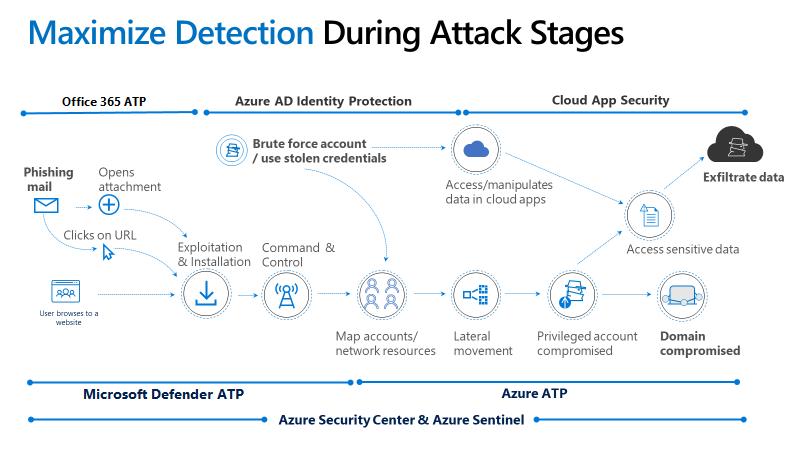
Microsoft released a pretty solid map, that explains a usual attack kill chain, with all the unique states that an attacker uses to breach into your environment and causes damage to your resources. What we see here is, that most common viruses or any other type of dangerous code is initiated through a user action within an office application or the internet. The remediation product for this stage is Defender for Office 365, with products like safe attachments, safe links or anti-spam policies. Let's get to the second part: the activation of that virus. For instance a new CVE (Common Vulnerabilities and Exposures) was posted by someone. The virus takes advantage of this exploited vulnerability in the system and gets control over thing's it is usually not permitted. At this point a "hacker" or what you want to call the attacker is often going to do a reconnaissance to get more information about the domain. The main target is obviously to steal data or compromise an (privileged) account. But to get access to a privileged account it usually takes an infiltrator 200 days average. Defender for Identity is what is forcing against actions in this part. A small agent will be installed on your domain controller that tracks unusual or threatening tasks taken by any principal. And the final steps are the cloud resources, with sensitive data or apps upon to exfiltration. Cloud app security takes place here with the cloud app catalog/database that stores over 17'000 service apps.
Steps for a simple secure environment
(Identity & Access management in Microsoft 365 & Azure)
So far we know which cloud products can help to increase the potential defense against attacks. But are there any simple hardening steps you can take in every Microsoft 365 tenant? Well yes; atleast based on my opinion. Here is a little graphics of mine, that shows some actions that are recommended to implement in every cloud environemnt. Please be aware that some of these steps will require an AzureAD Premium P1 license to stay compliant.

Why Microsoft?
One thing I want to mention is why I am so focused on just the Microsoft products, even if the landscape of great alternatives is huge. Some of them are: The hybrid capabilities. Let's be honest, about 80% of the fortune 500 companies already use Azure and most of them came from a classy Active Directory Domain. The migration from this position to AzureAD and generally Azure is simply the easiest and most convenient way imaginable. Service jungle is a term defined by myself. What I mean is the incredible amount of services in 365 and Azure that all harmonize with each other and act as individual gears in a big machine. The last one of the big three's is globalization & unification. Why should every organization have it's own SecOps Team? Why not using the immense capabilities of the Microsoft Cloud, that disposes more security related information than we all could dream about. These are the things I am currently convinced of when talking about the strategy of Microsoft.